Based Doge hit with 'same as Normie’ exploit as 91.4M BOGE is drained
An attacker minted 91 million BOGE tokens and crashed its price, relying on a similar vulnerability as the Normie exploit one day earlier.

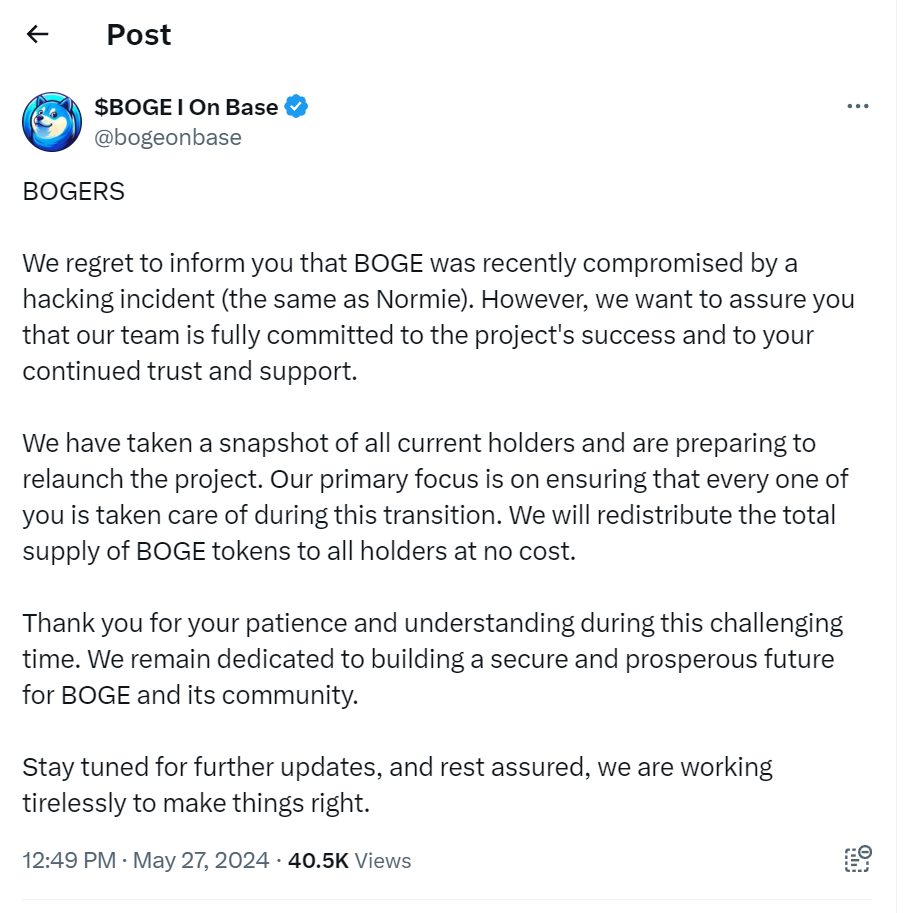
Memecoin protocol Based Doge (BOGE) on the Base network was exploited on May 27, the team has confirmed. The attack was “the same as Normie,” the team stated, implying that the attacker exploited a vulnerability similar to the one that caused the recent Normie exploit.
The team reported the attack on X, stating “We regret to inform you that BOGE was recently compromised by a hacking incident (the same as Normie).”
Normie was exploited on May 26, the day before the Based Doge attack.
Based Doge is a memecoin project inspired by the Doge meme. It has released a Web3 video game called “FlappyBoge” and plans to release a nonfungible token collection.
According to the post, the team will take a snapshot of current token balances and relaunch the project so that all victims of the attack will be compensated.
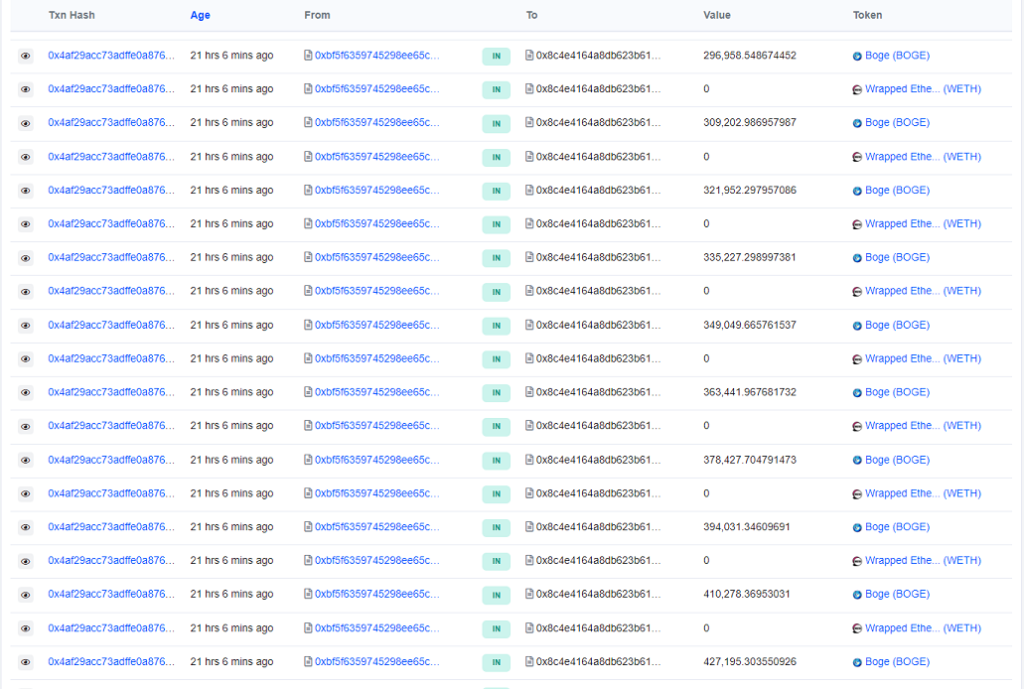
Blockchain data shows that at 5:48 pm UTC on May 27, an account ending in bAOC initiated over 120 transactions on Base. Each transaction resulted in hundreds of thousands of BOGE being transferred into the account, for a total of approximately 91.4 million BOGE.
Within each transaction, the attacker called an unverified function on a smart contract located at an address ending in 1a42. Because the contract is unverified, the code for this function is not human-readable.
Immediately after receiving these 91.4 million BOGE, the attacker swapped them for approximately 4.47 Ether (ETH), worth approximately $16,926 at the time.
Although the amount gained by the attacker was small, the impact on the price of BOGE was much larger. Prior to the attack, the price of BOGE was $0.002983, and the total supply of the coin was 1 billion, according to CoinMarketCap. This implied a market cap of approximately $2.9 million.
As the attack occurred, the price plummeted to 0.000072, implying that the 1 billion coins that existed before the attack lost more than $2.8 million in value.
According to an analysis published by Web3 insurance provider Neptune Mutual, the previous Normie attack was caused by a faulty “get_premarket_user” function. This function allowed a user to mint new tokens if they were either a premarket user or if they had the same balance as the deployer wallet. The attacker traded tokens until they had a balance equal to the deployer wallet, allowing them to become a “privileged user” who was allowed to mint new tokens.
Once they had minting authority, they minted over 170,000 Normie tokens and dumped them on the market, causing over $800,000 in losses.
Related: Memecoin trader loses over $1M following Normie exploit
Smart contract exploits continue to pose risks for crypto users. On May 17, an attacker drained $20 million from DeFi protocol Sonne Finance. The same day, an ex-employee of Solana memecoin platform Pump.fun allegedly exploited the protocol using privileged access. The alleged attacker claimed that he was arrested by U.K. police in connection with the incident.





Responses