Hacker mints 1B tokens in $16M Curio smart contract exploit
Curio said it will conduct a fund compensation program for affected liquidity providers, which could potentially take up to one year to complete.
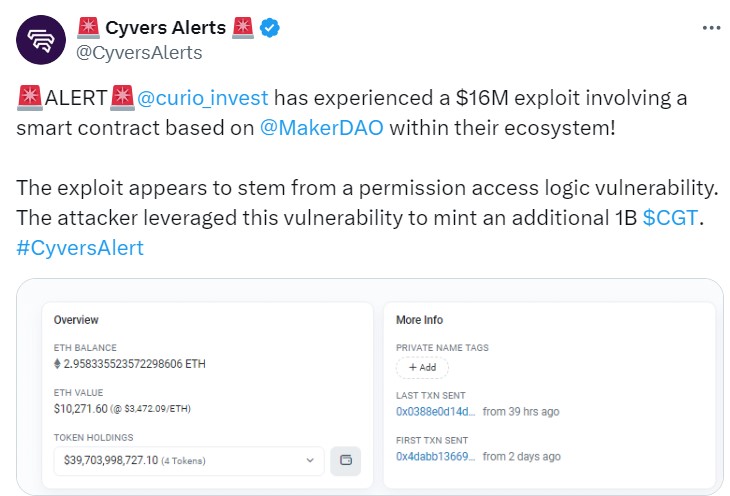
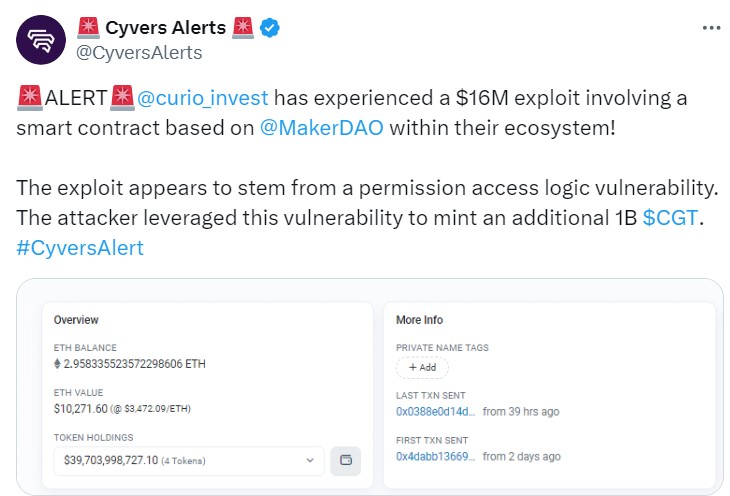
Real-world asset (RWA) liquidity firm Curio suffered a smart contract exploit involving a critical vulnerability related to voting power privileges, allowing the attacker to steal $16 million in digital assets.
Curio alerted its community of the exploit and highlighted that they are addressing the situation. The company said that a MakerDAO-based smart contract used within Curio was breached.
However, the company assured its users that the exploit only affected the Ethereum side and that all Polkadot and the Curio Chain contracts remained secure.
Web3 security firm Cyvers estimated that the losses from the exploit are about $16 million. The security firm said the exploit involved a “permission access logic vulnerability.”
On March 25, Curio published a post-mortem of the exploit and a compensation plan for affected users. Within the report, Curio highlighted that the problem was a flaw in the voting power privilege access control.
With this, the attacker acquired a small number of Curio Governance (CGT) tokens, allowing them to gain access and elevate their voting power in the project’s smart contract.
With the elevated voting power, the attacker performed a series of steps that ultimately allowed the execution of arbitrary actions within the Curio DAO contract. This led to the unauthorized minting of 1 billion CGT.
In the report, Curio said all the funds affected in the exploit will be returned. The team said it would release a new token called CGT 2.0. With the new token, the team promised to restore 100% of the funds for CGT holders.
Related: Hacker moves $10M from 2023 phishing incident to Tornado Cash
For liquidity providers, Curio said that it will conduct a fund compensation program. The team said it will be paid in four stages, with each stage lasting 90 days. This could mean that full payment could potentially take one year. They wrote:
“The compensation program will consist of 4 consecutive stages, each lasting for 90 days. During each stage: compensation will be paid in USDC/USDT, amounting to 25% of the losses incurred by the second token in the liquidity pools.”
The company also said that it would reward white hat hackers who can help in recovering the lost funds. The team said that hackers could receive a reward equivalent to 10% of funds recovered in the initial recovery phase.



Responses