Unizen hacker transfers $2.1M stolen funds to Tornado Cash
The hacker’s use of Tornado Cash marks the first movement of the stolen Unizen funds since March, heightening security concerns.

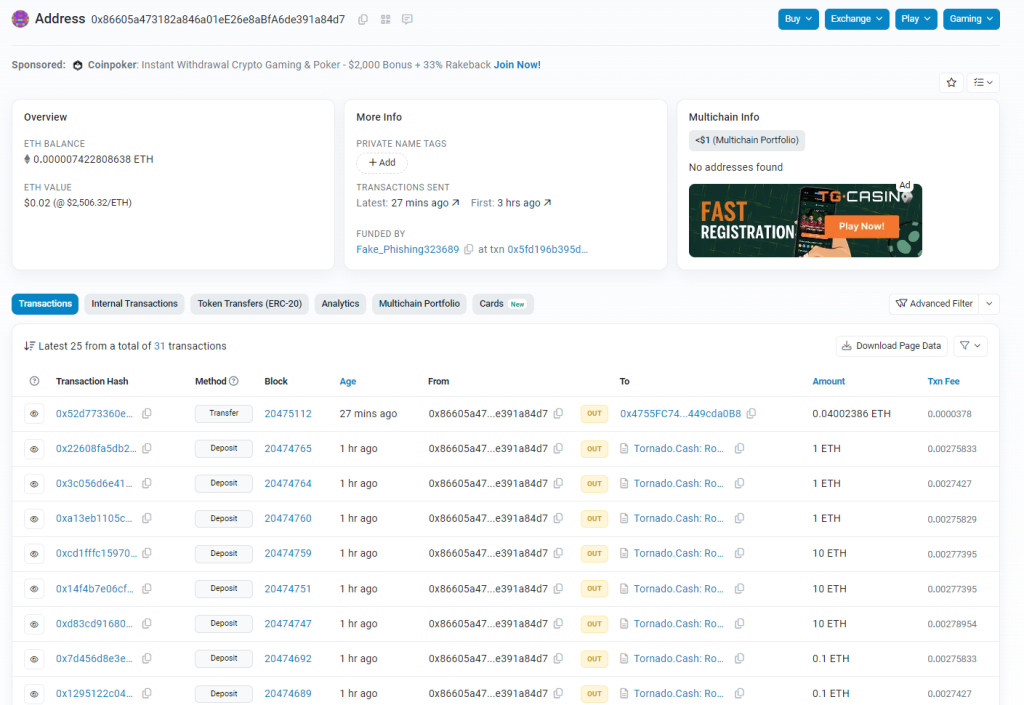
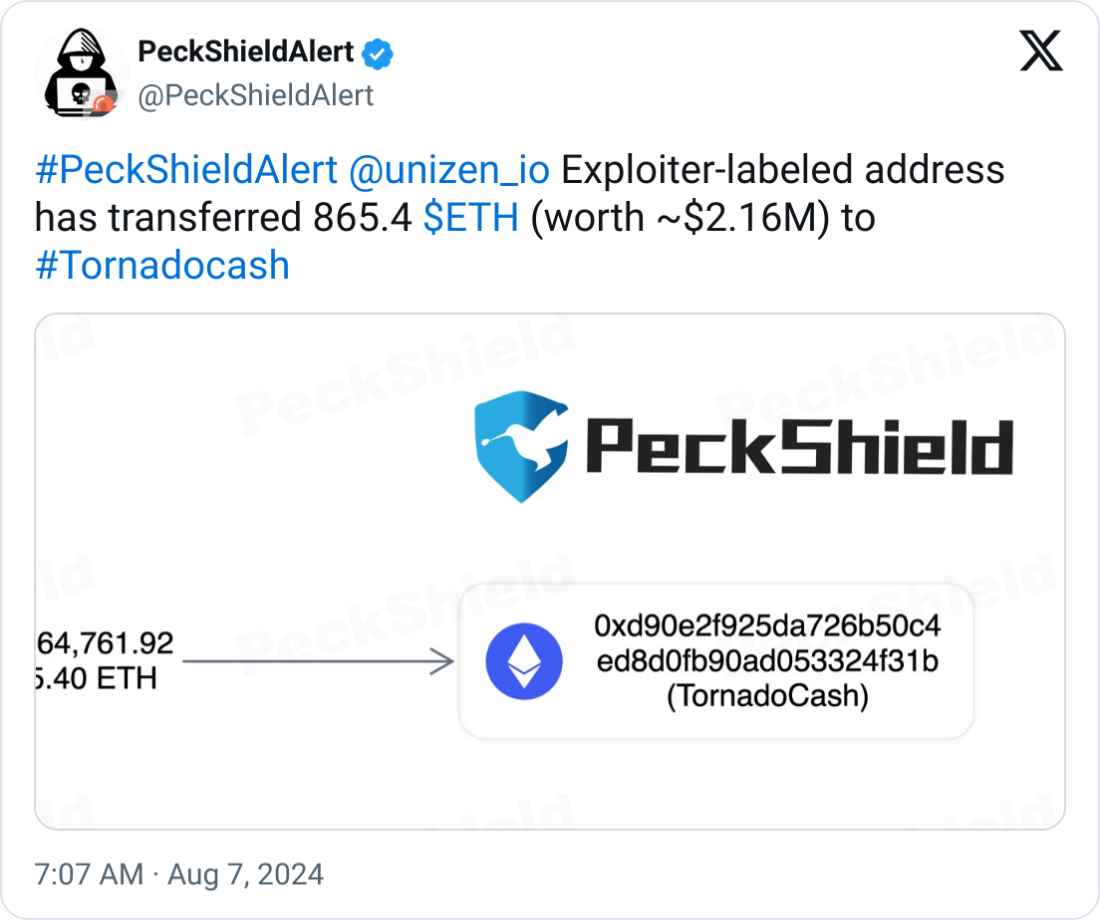
An exploiter-labeled address linked to the decentralized finance (DeFi) protocol Unizen hack has transferred 865.4 Ether, worth approximately $2.16 million, to Tornado Cash.
Blockchain security firm PeckShield flagged the exploiter’s transfer to the mixing service on Aug. 7, revealing the first movement of the stolen funds since March 8.
Around the time of the hack, Unizen announced that users who lost $750,000 or less would be reimbursed, with refunds beginning March 11.
Cointelegraph contacted Unizen for comment on the situation but did not receive a response before publication.
Funds moved to Tornado Cash
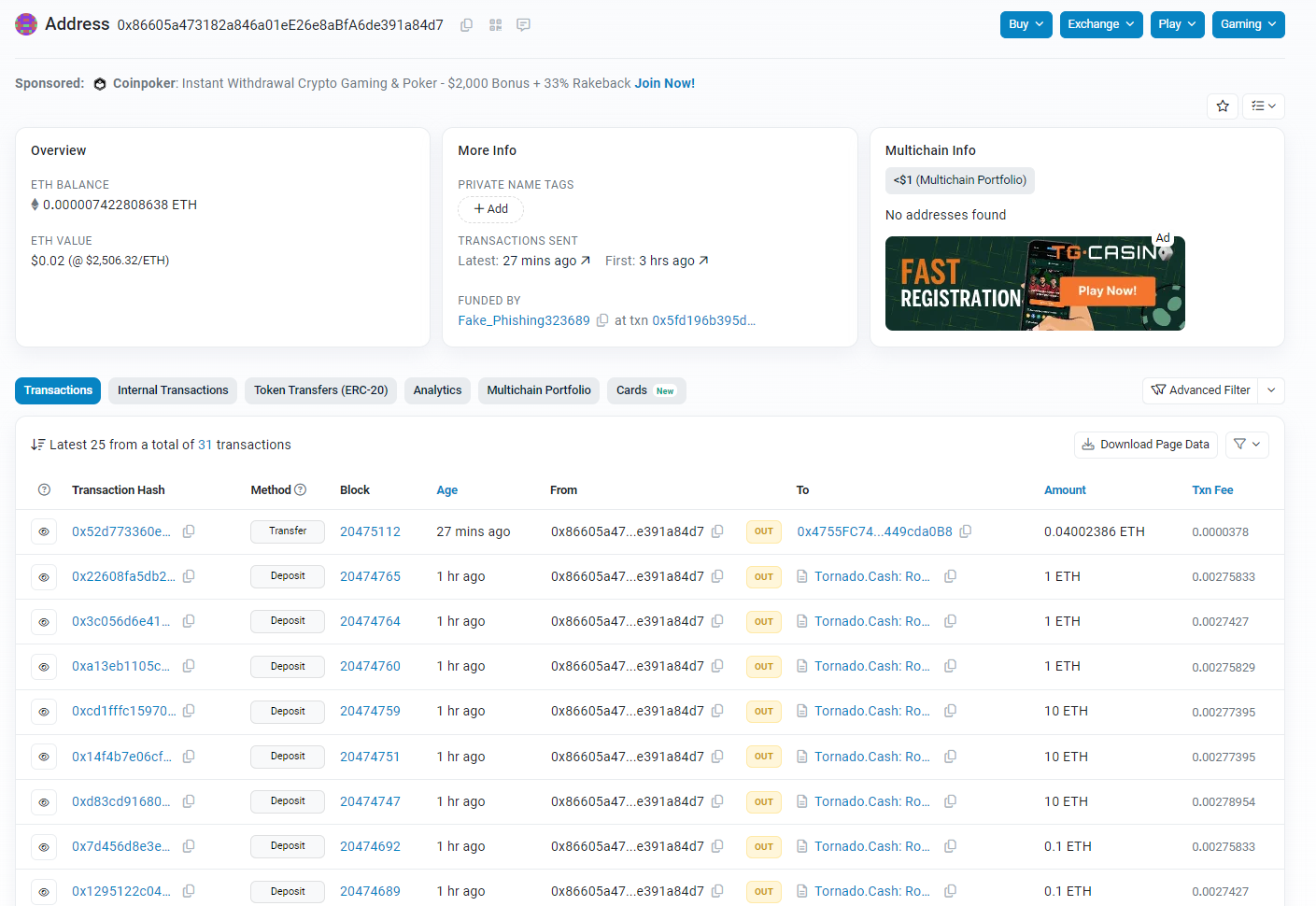
On Aug. 7, stolen funds, including the Maker Protocol stablecoin Dai (DAI) began to leave the exploiter wallet for the first time since the Unizen hack 151 days ago.
Related: DeFi protocol Unizen to provide ‘immediate reimbursement’ after $2.1M hack
At 4:12 am UTC, 500,000 DAI was sent out, followed by a further outflow of 1,679,859 DAI, bound for an unknown wallet (0x8660…84d7).
From 4:14 am, the exploiter began converting the 2,179,859 DAI into 863.67 Ether (ETH). Following that, the exploited started sending out the ETH from 5:35 am to Tornado Cash via 26 separate transactions.
Related: DAO Maker hack victims still await reimbursement 3 years later
Stolen funds reimbursement
On March 11, Unizen announced that the firm’s CEO, Sean Noga, had loaded funds to the company to facilitate refunding lost funds back to victims of the $2.16 million hack.
The announcement explained that returned funds would be in Tether (USDT) or USD Coin (USDC).
For users who lost more than $750,000 during the hack, the DeFi protocol explained that it would handle those victims on a case-to-case basis.
Related: Old Dolomite exchange contract suffers $1.8M loss from approval exploit
Post-hack security measures
Following the exploit in March, Unizen’s chief technology officer, Martin Granström, stated on X that the firm was collaborating with third-party security firms and law enforcement to identify the hacker.
Granström announced that the firm would share an incident report and invest more in security in the future.




Responses