Bybit Hacker Has Laundered Over 50% of Stolen ETH, Mainly Swapping to BTC via THORChain

SuperEx continues to track developments in the Bybit hack. According to Spot On Chain reports from February 28, the Bybit hacker has laundered more than 50% of the stolen ETH within a week after the attack. Over the past 5.5 days, the hacker has moved 266,309 ETH (~$614 million), accounting for 53.3% of the total 499,000 ETH stolen.
The hacker primarily exchanged ETH for BTC via THORChain, transferring an average of 48,420 ETH per day. With 233,086 ETH remaining, at the current rate, the funds could be fully laundered within the next five days. Below is a detailed breakdown of the laundering operation.
- Click to register SuperEx
- Click to download the SuperEx APP
- Click to enter SuperEx CMC
- Click to enter SuperEx DAO Academy — Space

Core Laundering Mechanism: THORChain’s Cross-Chain Infrastructure
The laundering operation heavily relies on THORChain’s cross-chain infrastructure.
THORChain facilitates trustless cross-chain asset swaps through decentralized liquidity pools and atomic swaps. The hacker injects ETH into THORChain’s Ethereum liquidity pool, where smart contracts automatically match the equivalent value in BTC liquidity pools, completing the swap without KYC verification. Since on-chain records only show standard asset transfers, tracking these transactions becomes extremely difficult.
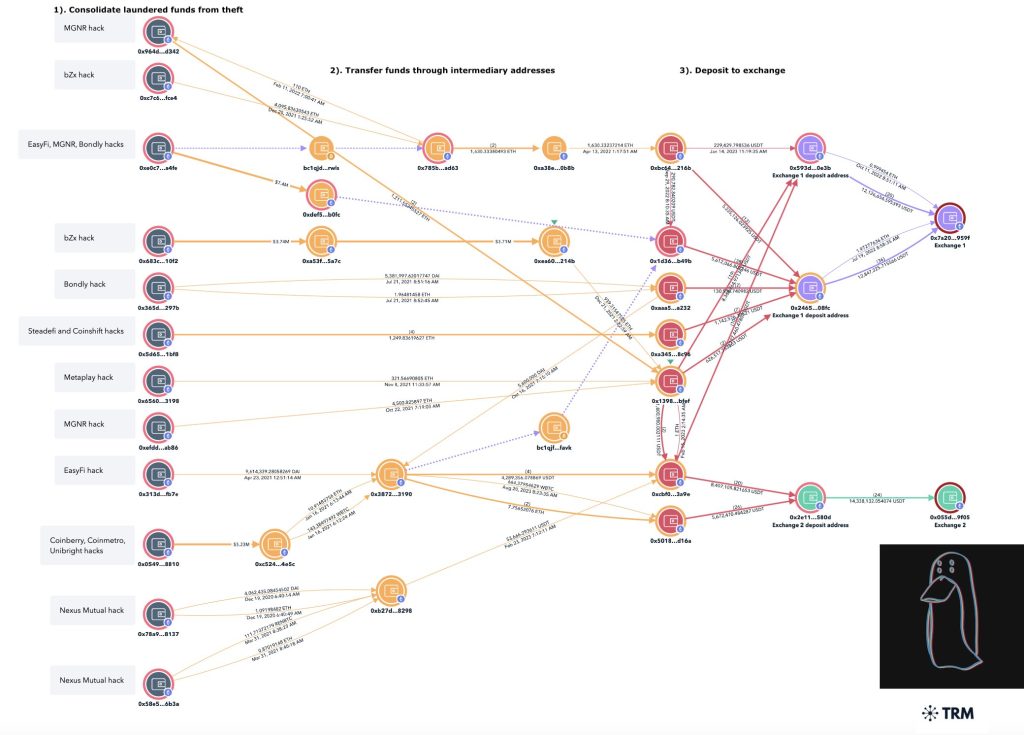
Hacker’s Operational Strategy: “Dispersed Input – Aggregated Output”
- Fragmented ETH Deposits: The stolen ETH was split into multiple small transactions (200–500 ETH per transaction) and distributed across dozens of intermediary addresses before being transferred to THORChain.
- Anonymous Wallets: Most of these addresses were newly created and anonymous, with some funds passing through Tornado Cash for additional obfuscation before the cross-chain swaps.
- BTC Aggregation: After conversion, BTC was consolidated into three primary addresses, which have so far accumulated over 42,000 BTC (~$2.08 billion).
- Layered Mixing Techniques: These BTC holdings were further obscured using advanced mixing strategies, making tracking even more difficult.
Technical Loophole: THORChain’s Non-Custodial Cross-Chain Model
THORChain’s “non-custodial cross-chain” mechanism plays a crucial role in this laundering operation.
- Threshold Signature Scheme (TSS): Cross-chain assets are secured using TSS, meaning they are collectively managed by validator nodes, with no single entity having full control.
- Regulatory Challenges: This security model, while ensuring protocol integrity, also makes it impossible for authorities to freeze assets in a traditional manner.
- ETH to Native BTC: The hacker converted stolen ETH into native BTC (not wrapped versions), effectively removing it from Ethereum’s monitoring framework.
THORChain’s Role and Its Exposure to Risk
This incident highlights THORChain’s dual identity:
- A decentralized financial infrastructure.
- A primary laundering channel for illicit funds.
THORChain’s Liquidity and Network Risks
As of February 2025, THORChain’s cross-chain transaction volume reached an all-time high, with over $1.2 billion processed daily. However, 68% of this surge was directly linked to Bybit’s stolen funds, triggering three major crises:
1️⃣ Liquidity Drain:
- ETH/BTC liquidity depth shrank from $850M to $320M in 5 days.
- Market makers increased slippage protection to 1.5%, tripling transaction costs for regular users.
2️⃣ Node Trust Crisis:
- THORChain validator TCB reported that over 70% of network transactions originated from Lazarus Group-associated addresses.
- This prompted validators to halt certain services to prevent further illicit activity.
3️⃣ Protocol Insolvency Risk:
- The hacker’s heavy use of THORChain depleted liquidity reserves by $210M.
- THORChain halted lending features and started an emergency token issuance to replenish reserves.
Governance Flaws: A Key Vulnerability
While THORChain’s core technology remains intact, the lack of governance safeguards exacerbated the problem:
- Daily trade limits were set at $1 billion, but there was no address reputation scoring system.
- This oversight allowed illicit funds to masquerade as regular user transactions, bypassing risk detection.
Market Impact & Fund Flow Analysis
This laundering operation has triggered structural shifts in the crypto market:
🔹 Hacked BTC Movement
- 37% of converted BTC has been moved to regulated exchanges in Russia and Turkey, likely for fiat off-ramping.
- 29% entered Wasabi Wallet, a well-known coin-mixing service.
- 34% remains in cold wallets, with no further movement detected yet.
🔹 Market Repercussions
- ETH/BTC Exchange Rate Under Pressure:
- Large-scale ETH sell-offs caused ETH/BTC to drop 7.2% from Feb 25–28, marking the biggest weekly decline since 2024.
- Derivatives Market Volatility:
- ETH perpetual contract funding rates plunged to -0.12%, indicating widespread short-selling panic.
- BTC futures open interest rose by 24%, signaling a capital shift from altcoins to BTC as a safe haven.
Regulatory Response & International Crackdown
U.S. & E.U. Interventions
Regulators are escalating actions, turning this into a major geopolitical issue:
-
U.S. OFAC (Office of Foreign Assets Control)
- On Feb 27, OFAC blacklisted THORChain validator nodes, adding them to the Specially Designated Nationals (SDN) list.
- U.S. entities are now prohibited from engaging with these nodes.
-
European Union Proposal
- The EU is considering amending the “Funds Transfer Regulation”, requiring cross-chain protocols to follow AML procedures similar to centralized exchanges.
Projected Laundering Completion & Potential Disruptions
The hacker still holds 233,086 ETH (~$5.5B). At the current daily laundering rate of 48,420 ETH, full completion is expected by March 5. However, several factors could delay the process:
1️⃣ Liquidity Depletion
- THORChain’s ETH/BTC pool now holds under $300M.
- At the current swap rate, BTC reserves will be exhausted by March 1, forcing the hacker to find alternative cross-chain protocols.
2️⃣ Regulatory Freezes
- South Korea’s Financial Supervisory Service froze 42 related accounts on Upbit and Bithumb, slowing fiat off-ramping.
3️⃣ Technical Countermeasures
- Ethereum developers proposed tighter monitoring of Tornado Cash, tracking zero-knowledge proof associations to block laundering routes.
Potential Backup Plans: Ren Protocol & Bitcoin Sidechains
Blockchain security firm Arkham Intelligence detected suspicious activity on February 28:
- Some ETH was converted to L-BTC on Liquid Network (Bitcoin sidechain) via Ren Protocol.
- Funds then moved to Bitcoin’s mainnet using the Stacks protocol.
This multi-layered obfuscation strategy will extend the laundering cycle by 3–5 days, but greatly reduces traceability.
Final Thoughts: The Industry-Wide Implications of This Laundering Operation
As of February 28, 2025, this laundering operation has processed over $6 billion, far exceeding the original stolen amount in total transactions.
🚨 Key Takeaway:
This event is not just an isolated hack—it exposes a fundamental conflict between decentralized technology ideals and sophisticated criminal exploitation. The crypto industry must now redefine the balance between anonymity and compliance, as decentralized finance faces increasing scrutiny from global regulators.




Responses