What is blockchain technology? How does it work?

Blockchain explained
Blockchains are distributed (i.e., without a single repository) and decentralized digital ledgers that are tamper-evident and resistant. At their most basic level, they allow users to record transactions in a shared ledger within that group. The result is that no transaction can be modified once it has been published under standard blockchain network functioning.
The blockchain concept was integrated with numerous other technologies and computer concepts in 2008 to create modern cryptocurrencies: electronic cash that is protected by cryptographic processes rather than a central repository or authority.
Blockchain implementations are frequently created with a specific goal or function in mind. Cryptocurrencies, smart contracts and distributed ledger systems for businesses are all examples of functionalities.
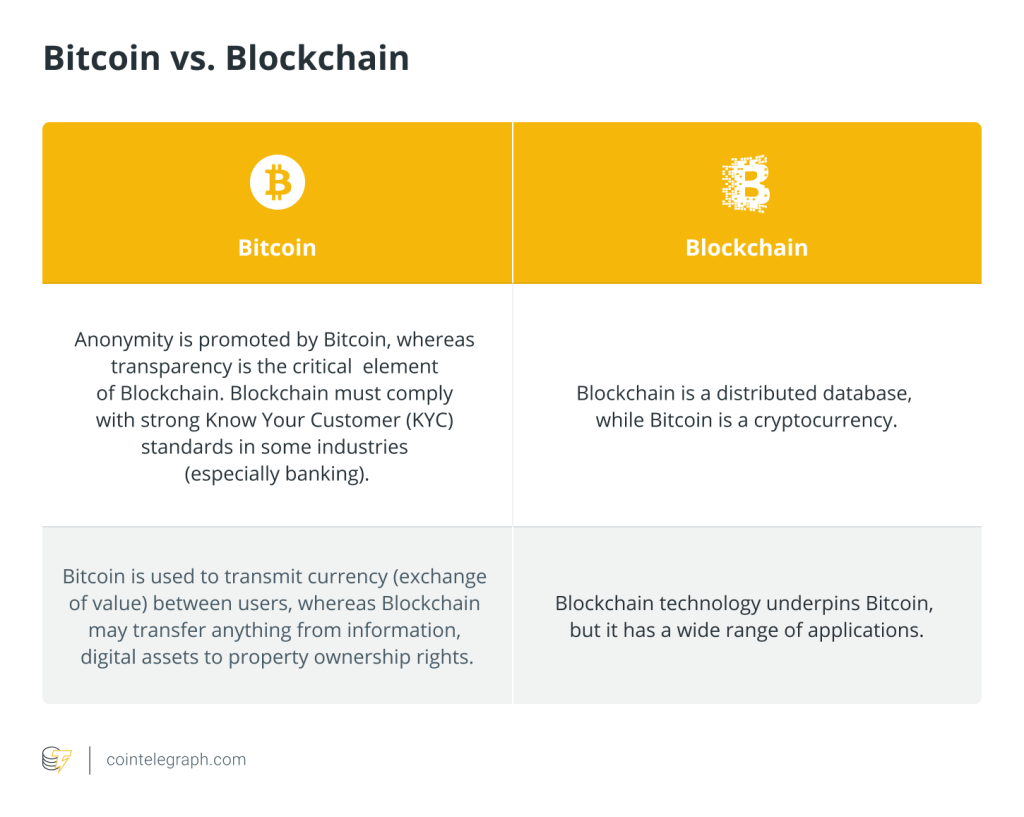
Bitcoin was the first blockchain-based cryptocurrency, allowing users to share data publicly so that participants can independently verify the transaction's validity. Cryptocurrencies are built on blockchain technology, which is named after the intensive use of cryptographic functions.
To digitally sign and securely transact within the system, users use public and private keys. Users can solve puzzles using cryptographic hash functions in the hopes of being paid with a fixed quantity of money in cryptocurrency-based blockchain networks that involve mining.
The field of blockchain technology has seen a steady stream of advancements, with new platforms being introduced regularly — the environment is constantly shifting. Other than cryptocurrencies, blockchain technology can be used to establish a permanent, public, and transparent ledger system for collecting sales data, tracking digital usage, and making payments to content creators like musicians.
This article explains blockchain technology and gives an overview of how it works.
To read more on the different types of blockchain networks, please click here.
How does blockchain work?
A blockchain's fundamental goal is to let people — especially those who don't trust one another — communicate vital data in a safe, tamper-proof manner.
Hash function, blocks, nodes, miners, wallets, digital signatures and protocols are the various main concepts in the blockchain.
Hash function
Let’s imagine that 10 people in one room decided to make a new currency. They have to follow the flow of funds to ensure the validity of the coins in their new monetary ecosystem. One person — let’s call him Bob — decided to keep a list of all actions in a diary. However, another person — let’s call him Jack — decided to steal money. To hide this, he changed the entries in the diary.

Then one day, Bob noticed that someone had interfered with his diary. He decided to change the format of his diary to prevent future tampering. He used a program called a hash function that turns text into a set of numbers and letters, as shown in the table below.
This process harnesses a secure hash algorithm, or SHA, that turns the letters into character strings. Bob can choose different types of SHAs that each varies in complexity and serves different needs.

A hash is a string of numbers and letters, produced by hash functions. A hash function is a mathematical function that converts a variable number of characters into a string with a fixed number of characters.
Just a small alteration in a string creates a completely new hash. After each diary entry, Bob inserted a hash. But then Jack decided to change entries again. He got to the diary, changed the record and generated a new hash.

Bob noticed that somebody had sifted through the diary again. He decided to complicate the record of each transaction. After each record, he inserted a new hash generated from the recorded last hash. Therefore, each entry depends on the previous.

If Jack tries to change the record, he will have to change the hash in all previous entries. Jack, however, was a determined thief, so he spent the entire night counting all the hashes.
Bob did not want to give up, so he added a different, random number after each record. This number is called a “nonce.” Nonces should be chosen in a way that results in the generated hash ending in two zeros.

To forge records with Bob’s updated entry system, Jack would now have to spend hours and hours determining the nonce for each line.
Nonces are difficult for even computers to figure out, but the task is possible, as miners compete to discover them as part of the blockchain mining process.
Blocks
Bob’s initial spreadsheet of 5,000 transactions is called the genesis block — the starting point for this blockchain. The adoption of this currency has spread, so transactions come quickly and often. New blocks are created, which can also hold up to 5,000 transactions and have codes that correlate with former blocks, making them unforgeable.
Let’s assume that this blockchain updates itself every 10 minutes with a new block. It does so automatically. No master or central computer instructs the computers to do this.
As soon as the spreadsheet or ledger or registry is updated, it can no longer be changed. Thus, it’s impossible to forge it. You can only add new entries to it. The registry is updated on all computers on the network at the same time. Changes to blockchains require consensus from a majority of the network’s participants.
One potential risk to a blockchain is a “51% attack,” during which a party overtakes the majority of a blockchain’s hash rate, allowing them to then dictate the network.
In general, a block contains a timestamp, a reference to the previous block, the transactions and the computational problem that had to be solved before the block went on the blockchain. The distributed network of nodes that must reach consensus makes fraud almost impossible within the blockchain.
Nodes
Bob kept up the diary in this manner for a short time. As new transactions continued occurring, however, he soon became burdened by the number of records, seeing his current system as unsustainable. So, as soon as his diary hit 5,000 transactions, he converted it to a one-page spreadsheet. Mary checked the accuracy of all transactions.
Bob then gave his spreadsheet diary to 3,000 different computers, each located in different regions globally. These computers are called nodes. Every time a transaction occurs, it must be approved by those nodes, each of which checks the transaction’s validity. Once every node has checked a transaction, essentially a type of electronic vote occurs. Some nodes may think the transaction is valid, while others may see it as fraudulent.
Each node has a copy of the spreadsheet diary. Each node checks the validity of each transaction. If a majority of nodes say that a transaction is valid, then it is written into a block.
Now, if Jack wants to change one entry in the spreadsheet diary, all the other computers will have the original hash. They would not allow the change to occur.
Miners
Mining is the process by which miners add new blocks to the chain. Every block in a blockchain has its unique nonce and hash, but it also refers to the hash of the previous block in the chain, making mining a block difficult, particularly on big chains.
Miners utilize specialized software to solve the exceedingly difficult math issue of generating an acceptable hash using a nonce. Because the nonce is only 32 bits long and the hash is 256 bits long, there are around four billion nonce-hash combinations to mine before finding the proper one.
Miners are considered to have discovered the “golden nonce” when this happens, and their block is added to the chain. Making a change to any block earlier in the chain necessitates re-mining not only the affected block but also all subsequent blocks.
This is why manipulating blockchain technology is so tough. Consider it “safety in math” because identifying golden nonces takes a long time and a lot of computational resources. When a block is successfully mined, all nodes in the network acknowledge the change, and the miner is compensated financially.
Read more in the article “How to mine Bitcoin?”
Wallets, digital signatures and protocols
Continuing with the same example, Bob gathered the 10 people together (the 10 people initially gathered that are part of the new currency). He needed to explain the new digital coin and ledger system to them.
Jack confessed his sins to the group and apologized. To prove his sincerity, he gave Ann and Mary their coins back.
With all that sorted, Bob explained why this could never happen again. He decided to implement something called a digital signature to confirm every transaction. But first, he gave everyone a wallet.
What is a wallet?
If you possess digital money, then you need a digital wallet or an online platform or exchange for storage.
A wallet is a string of numbers and letters, such as: 18c177926650e5550973303c300e136f22673b74. This is an address that will appear in various blocks within the blockchain as transactions take place. No names or personally identifiable information is included — just the wallet number.
Public wallet addresses are strings of characters to which certain assets can be sent. The address of each particular wallet is generated from a public key.
Related: Bitcoin wallets for beginners: Everything you need to know
Digital signature
To carry out a transaction, you need two things: a wallet, which is an address, and a private key. The private key is a string of random numbers. Unlike the address, however, the private key must be kept secret. A private key controls funds held within its related wallet.
When someone decides to send coins to anyone else, they must use their private key to sign the message containing the transaction. The system of two keys — a private and a public key — is at the heart of encryption and cryptography, and its use long predates the existence of blockchain. It was first proposed in the 1970s.
Once the message is sent, it is broadcast to the blockchain network. The network of nodes then works on the message to make sure that the transaction it contains is valid. If it confirms the validity, the transaction is placed in a block. After that, no information about it can be changed.
What are cryptographic keys?
A cryptographic key is a string of numbers and letters. Cryptographic keys are made by key generators or keygens. These keygens use very advanced mathematics involving prime numbers to create keys. Such keys can be used for encrypting or decrypting information.
Protocols
Blockchain technology consists of individual behavior specifications, a large set of rules that are programmed into it. Those specifications are called protocols. The implementation of specific protocols essentially makes blockchain what it is — a distributed, peer-to-peer, secured information database.
Blockchain protocols ensure that the network runs the way it was intended to by its creators, even though it’s completely autonomous and isn’t controlled by anyone.
Here are some examples of protocols implemented in blockchains:
-
Input information for every hash number has to include the previous block’s hash number.
-
The reward for successfully mining a block decreases by half after 210,000 blocks have been mined. For Bitcoin (BTC), this is called halving. At 10 minutes per block, mining 210,000 blocks takes about four years; hence, Bitcoin’s halving event every four years.
-
To keep the amount of time needed to mine one block at approximately 10 minutes, mining difficulty is recalculated every 2,016 blocks. Mining difficulty essentially balances the network to account for the number of miners. More miners mean a more competitive atmosphere, making blocks more difficult to mine. Fewer miners mean it’s comparatively easier to mine blocks, thus enticing miners to participate.

Blockchain technology: Pros and cons
The majority of blockchains are built as a decentralized database that acts as a distributed ledger. These blockchain ledgers keep track of and store data in blocks that are arranged in chronological order and linked by cryptographic proofs.
The development of blockchain technology has resulted in numerous benefits across a wide range of businesses, including enhanced security in trustless situations. However, the fact that it is decentralized has significant drawbacks. For example, blockchains have restricted efficiency compared to typically centralized databases and require more storage space.
Various pros and cons of blockchain include:

What is decentralization in blockchain and why is it important?
Blockchains are essentially types of distributed databases. The database is the blockchain, and each node on a blockchain has access to the whole chain. No one node or computer regulates the information it contains. Every node can validate the records of the blockchain. This is all done without one or several intermediaries in control of everything.
It is architecturally decentralized, and there is no single point of failure that would bring down the blockchain, which makes it a critical component of blockchain systems. However, the nodes of a blockchain are logically centralized, as the entire blockchain is a distributed network performing certain programmed actions.

Peer-to-peer transmission
In decentralized peer-to-peer (P2P) transmission, communication always occurs directly between peers rather than through a central node. Information about what is happening on the blockchain is stored on each node then passed to adjacent nodes. In this way, information spreads through the whole network.

Transparency in blockchain technology
Anyone inspecting the blockchain is capable of seeing every transaction and its hash value. Someone using the blockchain can act pseudonymously if they wish, or they can give their identification to others. All that is seen on the blockchain is a record of transactions between wallet addresses.
Once a transaction is recorded on the blockchain and the blockchain updates, altering the record of this transaction becomes impossible. Why? That particular transaction record is linked to the record of every preceding one, making it immutable. Blockchain records are permanent, they are ordered chronologically, and they are available to all other nodes.
It is nearly impossible to turn off the network. As numerous nodes exist and operate globally, a single party can not take over the entire network.
Faking a block is also nearly impossible because the validity of each block and, by extension, its inclusion into the blockchain is determined by an electronic consensus of nodes. There are thousands of these nodes, scattered all over the world. As a result, capturing the network would require a computer with a virtually impossible amount of power.
Using blockchain technology as a normal database would prove difficult, however. Can you store three gigabytes of files on the blockchain in the same way as using database platforms such as Microsoft Access, FileMaker or MySQL? This would not be a good idea. Most blockchains are not suitable for this by design or simply lack the required capacity.
Traditional online databases usually use a client-server network architecture. This means that users with access rights can change entries stored in the database, but the overall control remains with administrators. When it comes to a blockchain database, each user is in charge of maintaining, calculating and updating every new entry. Every single node must work together to make sure they are all coming to the same conclusions.
Blockchain technology architecture also means that each node must work independently and compare the results of its work with the rest of the network, so reaching a consensus can be very time-consuming. Because of this, blockchain networks historically have been considered slow when compared with traditional digital transaction technology. Advancements have increased blockchain-related transaction speeds in some cases, as seen in some crypto assets, projects and solutions.
That said, there are experiments in producing databases with blockchain technology. These platforms aim to take an enterprise-class distributed database and build on top of it while adding the three key attributes of blockchain: decentralization, immutability and the ability to register and transfer assets.
How secure is blockchain technology?
Although blockchain is not immune to hacking, its decentralized nature provides it with a stronger line of security. A hacker or criminal would need control of more than half of all machines in a distributed ledger to change it.
The most well-known and largest blockchain networks, such as Bitcoin and Ethereum (ETH), are open to everyone with a computer and an internet connection. Having more participants on a blockchain network tends to boost security rather than create a security concern. More nodes participating means more individuals are reviewing each other's work and reporting bad actors. That's one reason why, counterintuitively, private blockchain networks that require an invitation to join can be more vulnerable to hacking and manipulation.
Furthermore, blockchain is beneficial in combating “double-spending” attacks in payments and money transfers. Cryptocurrency attacks are a significant source of concern. A user will spend their cryptocurrency more than once in a double-spending attack. It's a problem that doesn't exist when dealing with cash.
If you spend $3 on a cup of coffee, you no longer have $3 to spend on anything else. However, when it comes to crypto, there's a chance that a user will spend the cryptocurrency numerous times before the network notices.
This is something that blockchain can help with. Within a cryptocurrency's blockchain, the entire network must agree on the transaction sequence, confirm the most recent transaction, and publish it publicly, which helps preserve the network's security.
Bitcoin vs blockchain
Let's understand how Bitcoin and blockchain are two different things:

Where can blockchain technology be used?
The last portion of this article will discuss some of blockchain’s many applications. Blockchain technology is particularly ideal for what is known as “smart contracts.” So, what exactly are smart contracts?
Smart contracts define the rules and penalties around a specific agreement, similar to the function of traditional contracts. The big difference, however, is that smart contracts automatically enforce those obligations. Thanks to their coding, smart contracts discharge on the fulfillment of specific criteria.
Decentralized finance
Decentralized finance, or DeFi, is the utilization of blockchain technology that allows participants access to features similar to those common in the mainstream financial world, except in a decentralized fashion. Using different DeFi solutions, participants can loan and borrow funds — as well as access other opportunities — governed on the blockchain away from the control of a centralized authority.
Nonfungible tokens
Nonfungible tokens, or NFTs, serve as an application of blockchain technology with vast potential in several different use cases. Such tokens are verifiably unique and are not exchangeable one-for-one with others for the same value. One potential use case for NFTs is the authentication of artwork, with art pieces tied to NFTs, which can verify their authenticity and ownership.
Supply chains
Applying blockchain technology to a supply chain can provide the ability to track ingredients, foods, materials and more back to the source to prove their origins, as well as to provide other pertinent information about any given supply chain.
Warranty claims
Settling warranty claims can be expensive, time-consuming and often difficult for those making the claim. It is possible to implement smart contracts using blockchain technology, which will inevitably make the process notably easier.
Insurance claims
With smart contracts, a certain set of criteria for specific insurance-related situations could be established. In theory, with the implementation of blockchain technology, you could just submit your insurance claim online and receive an instant automatic payout — pending, of course, that your claim meets all the required criteria.
Identity verification
With blockchain and its decentralization aspect, the verification of identity online could be much quicker and potentially safer. Keeping online identity data in a central location could become a practice of the past with the use of blockchain, meaning computer hackers would no longer have centralized points of vulnerability to attack.
The Internet of Things (IoT)
Linked together via the internet for interaction purposes, the IoT is an ecosystem of software-friendly items, such as vehicles and devices, which include certain technological specifications that make such interaction possible.
Blockchain technology could play a role in the future of IoT, partly by providing potential methods for guarding against hackers. Because blockchain is built for decentralized control, a security scheme based on it should be scalable enough to cover the expansion of IoT.
Archiving and file storage
Google Drive, Dropbox and others have thoroughly developed the electronic archiving of documents with the use of centralized methods. Centralized sites are tempting for hackers. Blockchain and its smart contracts offer ways of reducing this threat substantially.
Fighting crime
As the technology gains more mainstream attention, blockchain and its smart contracts have the potential to help in the fight against money laundering tactics.
Blockchain provides for a more comprehensive analysis of the system rather than only monitoring entry and exit points. As blockchain is a decentralized network in which each user or node is responsible for validating updates, it enhances the network's security.
Voting
Voting in elections and similar processes, could be greatly improved with smart contracts and blockchain. Various related applications have come into existence over time.
The future of blockchain technology
The potential of blockchain technology is virtually limitless, and recent advancements have brought us closer to a decentralized, trustless internet, transaction transparency and more.
As we move away from the pandemic period and into the era of the 'new normal,' blockchains are likely to be at the forefront of our progress in addressing these new societal challenges and redefining the true meaning of wealth in the brave new world of digital money.
The future of blockchain technology appears bright, and given that it is already demonstrating potential in nearly every field, it seems that the best is yet to come.
Meanwhile, it will be intriguing to see where blockchain technology goes in the future, particularly in terms of banking services, money transfers, decentralized markets and other areas.


… [Trackback]
[…] There you can find 82531 more Information on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Find More on on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More here on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] There you can find 86262 additional Information on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you will find 54542 more Information to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Find More Info here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you can find 27457 additional Information to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] There you will find 17443 more Info to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you can find 3901 more Information on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you can find 86581 more Information on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you can find 41850 additional Information to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] There you can find 46094 more Info to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Here you can find 66948 more Information to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Find More Info here to that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/3470/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/3470/ […]