Permissioned blockchain vs. permissionless blockchain: Key differences

A blockchain is a distributed, decentralized digital ledger of transactions. This ledger is widely duplicated and distributed across a network of computers on the said blockchain.
Technically, blockchains can serve as a decentralized way to store information. Because of the distributed nature of blockchain, it is a system that is virtually impossible to cheat, hack or alter.
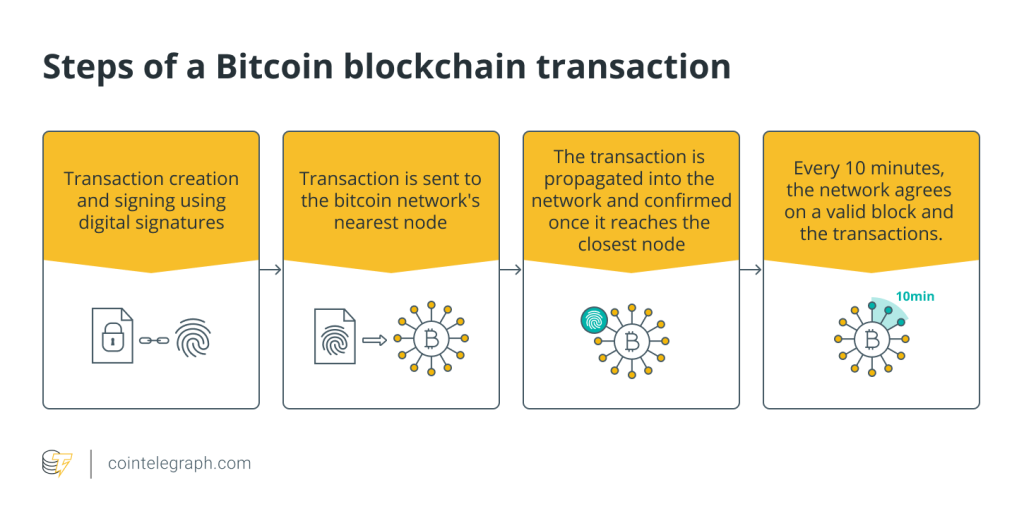
Bitcoin (BTC), as you might know, was the very first cryptocurrency that was blockchain-based. It quickly caught on in the crypto community because it allowed data to be shared publicly among users, allowing participants within the network to verify and validate transactions independently.
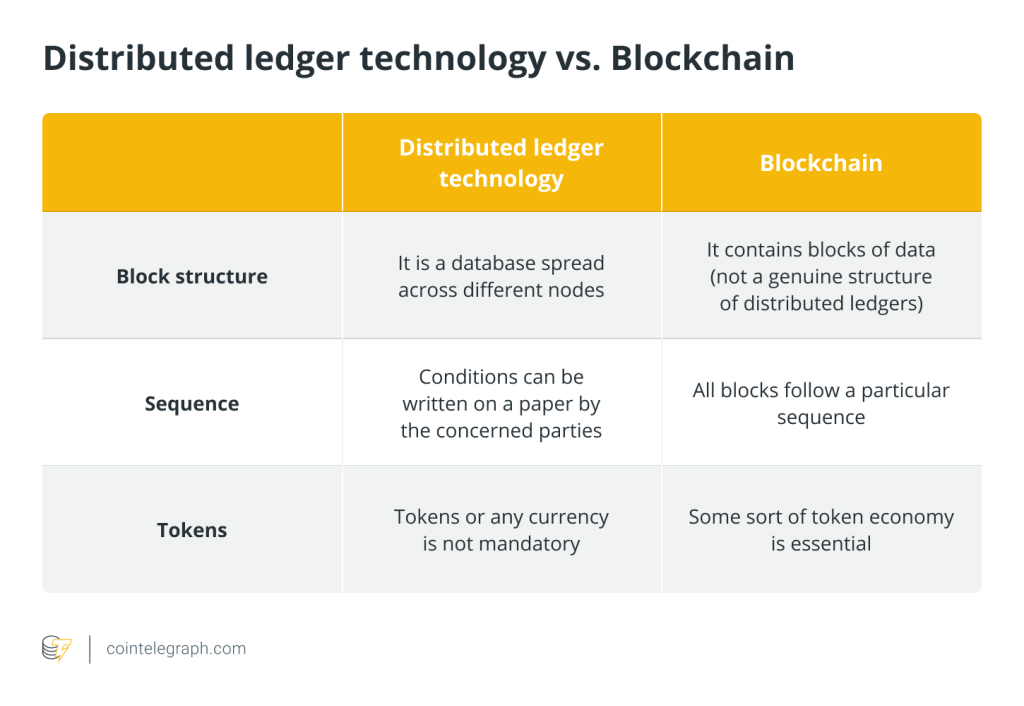
Each block in the blockchain consists of transactions. Each time a new transaction happens, a record of such is added to every participant’s ledger. Hence, this type of decentralized database is called distributed ledger technology or DLT. Blockchain is a type of DLT, and transactions are recorded via a hash (cryptographic signature).
Briefly put, DLTs include a variety of technologies and frameworks that allow for a distributed design. Two prominent paradigms are permissionless and permissioned blockchains, which we will discuss in further detail throughout this article.
What is a permissioned blockchain?
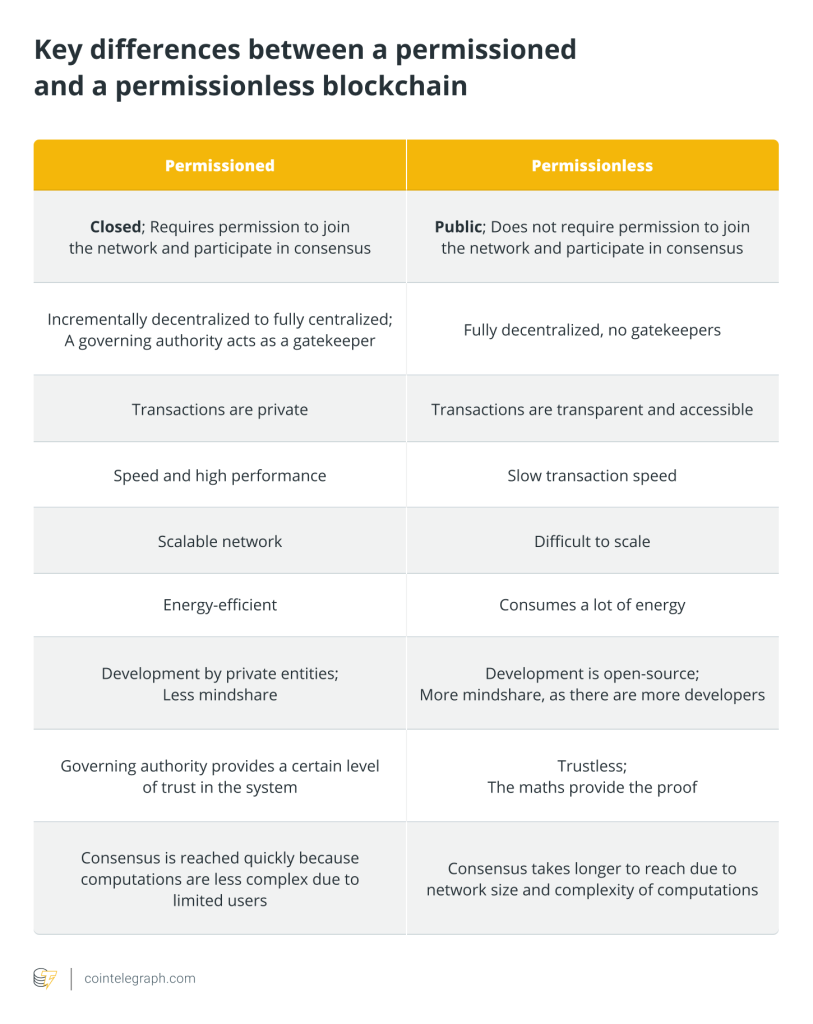
Permissioned blockchains are blockchains that are closed or have an access control layer. This additional layer of security only allows participants to perform the actions that they are authorized to perform.
In a permissioned blockchain, a user would need permission from the network owner to become part of the said network. Technically, a user can only access, read and write information on the blockchain if they are given access to it. A private permissioned blockchain defines the roles that dictate how each participant can contribute to the blockchain and what they can access.
A permissioned blockchain also supports customization. Hence, identity verification can also be done to let people into the permissioned network, instead of having the network owner approve each user. Users would ideally still be able to perform only certain activities in the network, based on the blockchain’s designated permissions.
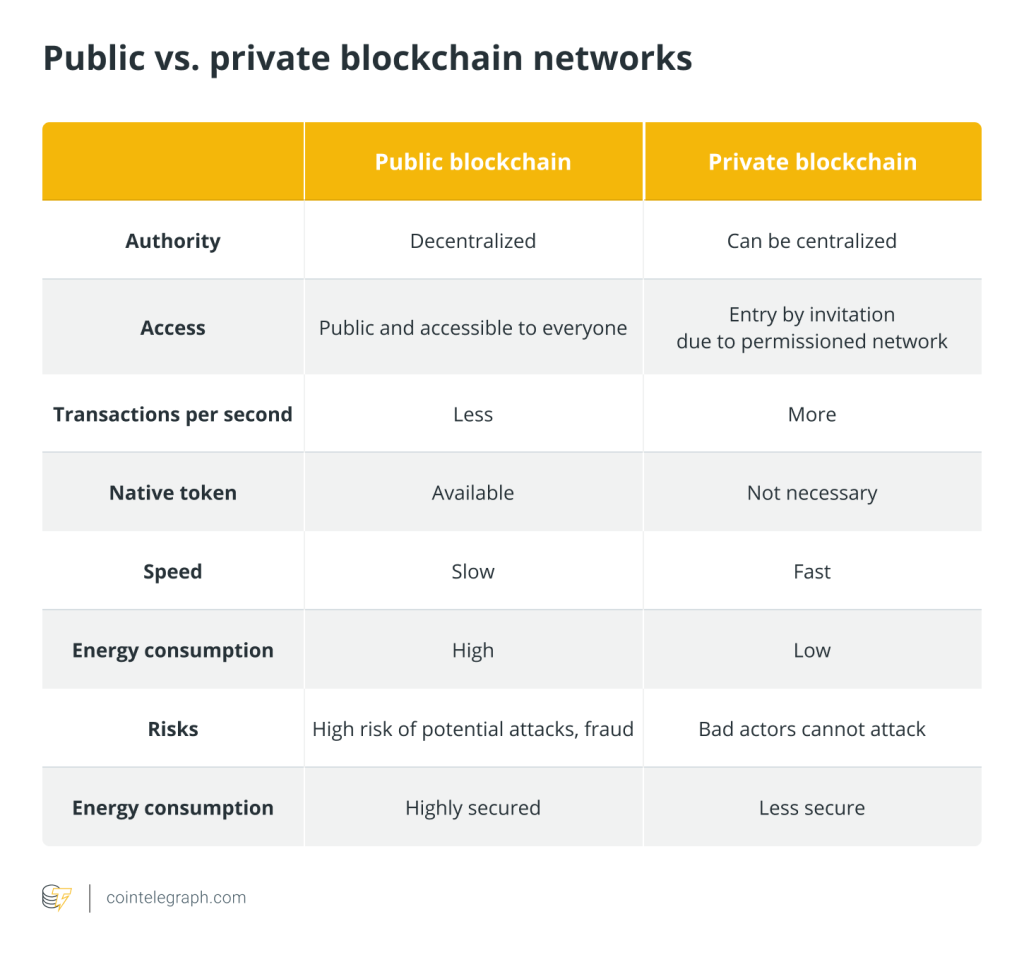
Also sometimes referred to as “private blockchains” or “permissioned sandboxes,” permissioned blockchains are considered to be partially decentralized. This is because, unlike Bitcoin, the network is distributed across known participants.
A good permissioned blockchain example is Ripple, which is a large cryptocurrency that supports permission-based roles for network participants. A lot of businesses prefer permissioned blockchain networks because they allow network administrators to configure settings and place restrictions as needed.
How does blockchain consensus work on a permissioned blockchain?
A permissioned blockchain does not use similar consensus models as permissionless blockchains. Typically, organizations that use permissioned blockchains use models like the Practical Byzantine Fault Tolerance (PBFT), federated, and round-robin consensuses.
-
PBFT consensus: PBFT is a voting-based consensus algorithm. In this model, the network’s safety is guaranteed as long as the required minimum percentage of nodes are behaving honestly and working properly.
-
Federated consensus: In a federated consensus, there is a set of signers trusted by each node in the blockchain. These signers help the nodes reach the consensus stage using a single block generator that receives the transactions, holds them and filters them accordingly.
-
Round-robin consensus: In a round-robin consensus, nodes are selected pseudo-randomly to create blocks. Each node has to wait several cycles before it can be chosen again to add a new block.
Characteristics of permissioned blockchain
Some of the defining characteristics of a permissioned blockchain are deeply connected to security. Since there is an access control layer, permissioned blockchains are seen as more secure alternatives to public blockchain systems like Bitcoin.
As such, it is preferred by people who need to define roles, verify identities and secure access within a network. Permissioned blockchains are also not anonymous and are usually developed by private entities like businesses and private organizations.

Decisions are authorized by a private group
Contrary to permissionless networks, permissioned networks are not consensus-based. Instead, decisions are made by the owners of the network through a central, pre-defined level.
Decentralization isn’t fixed
Unlike Bitcoin, which is a fully decentralized blockchain, permissioned blockchains can be fully centralized or partially decentralized. The members typically decide on the network’s level of decentralization, as well as algorithms for consensus.
Transparency is not required
Unlike permissionless blockchains, permissioned blockchains do not need to be transparent. Transparency is optional, as most permissioned blockchain networks are specifically intended to not be transparent for security purposes. Levels of transparency usually depend on the goals of the organization running the blockchain network.
Advantages and disadvantages of permissioned blockchain
Exclusivity grants permissioned blockchains advantages over public ones, but there are also a few downsides. Here’s a comparison:
Advantages of permissioned blockchain
On top of the list of advantages of permissioned blockchains is a high level of privacy and security. Without having been verified or granted permission, an outsider cannot access or alter transaction information.
Another advantage is flexibility when it comes to decentralization. It can be incremental or fully centralized, giving businesses more freedom to participate without having to worry about the risks associated with a highly centralized network.
They are also highly customizable and can accommodate configurations and integrations based on an organization’s needs. Lastly, they are both scalable and high-performing due to the limited number of nodes needed to manage transaction verifications.
Disadvantages of permissioned blockchain
Despite the advantages we outlined above, there are still some risks and disadvantages associated with this type of blockchain.
Mostly, it’s associated with the lack of transparency within the network and the risk of corruption. Precisely because it’s limited to only some people and is controlled by a private group, there is a high risk of collusion and overriding of consensus. As such, the operators of the network can easily alter consensus rules.
Suffice it to say that while deemed secure, a permissioned blockchain’s security is also dependent on its members’ integrity. Should a person or group with control over the network decide to alter data for their benefit, they can do so. In this regard, the network’s lack of transparency becomes a major downside.
They are also subject to regulation and censorship, especially for businesses that need to operate under certain rules and regulations. As such, there is no liberty to access the features of public blockchains that are uncensorable.
What is a permissionless blockchain?
On the opposite side of the spectrum is another type of DLT paradigm, which is a permissionless blockchain. Most of the major cryptocurrencies (like Bitcoin) run on permissionless blockchain networks.
True to its name, it allows anyone to take part in the network and access information. In short, it is decentralized and open to the public. It’s called “permissionless” because there are no gatekeepers and no censorship. Anyone who wants to access the blockchain does not need to pass Know Your Customer (KYC) requirements or provide identification documents.
Technically, as long as the protocol allows it, anyone can use it to do anything they want within the network. Permissionless blockchains are considered to be closer to Satoshi Nakamoto’s original concept of blockchain.
Now, because it is accessible to the public, the typical trade-off of permissionless blockchains is speed. They tend to be slower than permissioned counterparts, which only have a few members.
So how do permissionless blockchains work? Typically, transaction information stored on these blockchains is validated by the public. Because there is no regulatory body or authority, the network relies on the public to reach a consensus concerning the validity of transactions.
The consensus mechanisms typically used in these types of networks are proof-of-work (POW) and proof-of-stake (POS). Generally, honesty is incentivized with these mechanisms in place and keeps the system working as expected. Some examples of permissionless networks are Bitcoin and Ethereum.
Characteristics of permissionless blockchain
In contrast to permissioned blockchains, permissionless blockchains are characterized by the transparency of their transactions and the anonymity of their users. They also favor open source development.

Decentralization
Permissionless blockchains are typically decentralized. As such, a single entity alone cannot edit the ledger, shut down the network or alter its protocols. This is heavily anchored in the consensus protocol, which relies on the majority and their sense of integrity. Such a consensus typically requires the agreement of more than 50% of its users.
Transparency
Users within a permissionless network can access all types of information (except private keys). Because the very nature of a decentralized network is to eschew central authority figures, transparency of transactions in a permissionless network is valued.
Anonymity
Unlike permissioned networks, permissionless blockchains do not ask users for their identification or personal information when they create an address.
Tokens
Permissionless blockchains allow the utilization of tokens or digital assets. These typically serve as incentives for users to take part in the network. Tokens and assets can either increase in value or decrease in value over time, depending on the market.
Advantages and disadvantages of permissionless blockchain
Permissionless blockchains are highly decentralized and open. Naturally, they come with a set of advantages and disadvantages. Here’s a comparison:
Advantages of permissionless blockchain
One of the foremost advantages of a permissionless network is the high level of transparency. Because it is highly decentralized and spans across a large network, transparency facilitates fast reconciliation between unknown parties.
Decentralization has its perks, of course. One of them is that information is not stored in any one central repository, thereby making the public record secure, reliable and accessible to all. For this reason, it is also considered virtually unhackable.
The network is also secure and resistant to censorship because it is highly accessible by users globally. As such, attackers will find it difficult to infiltrate the network. There is no single repository to target, and they would have to attack 51% of the network to override its consensus mechanisms.
Disadvantages of permissionless blockchain
Most of the disadvantages associated with a permissionless blockchain are connected to its performance. One of the biggest challenges of permissionless blockchain is the power required to run it. It requires large amounts of energy and computing power to achieve consensus.
Because it’s typically such a large network, it is usually slower than permissioned networks and harder to scale. Due to its size, and the computing power needed to verify transactions, permissionless blockchains thus consume a lot of energy and computing power. As such, it’s difficult for some companies to adopt permissionless networks as an enterprise solution for their organization.
There is also less privacy over transaction information due to its public nature.
To an extent, anonymity can also be considered a downside of permissionless systems. Because anyone can participate in the network, there’s no way to readily filter out malicious players or fraudsters.
Key differences between a permissioned and a permissionless blockchain

Similarities between a permissioned and a permissionless blockchain
In terms of common ground, here are a few characteristics shared by both blockchains.
First, both are considered distributed ledgers, meaning that multiple versions of similar data are stored in different places across the network. Both blockchains also use consensus mechanisms, meaning that members can reach an agreement concerning how transactions can be verified or how the ledger should look.
Both blockchains are also immutable, although not fully for permissioned networks. Immutability means that data stored in these networks, theoretically, cannot be altered unless consensus mechanisms are overridden, or the system is hacked.
Permissioned vs. permissionless blockchain: Which is better for you?
The two blockchain architectures have different use cases, making each of them more suitable for certain applications, respectively.
For instance, permissionless blockchains are more suited for financial applications. It is also highly applicable for those that require high levels of decentralization, such as:
-
Donations and crowdfunding
-
Trading of digital assets
-
Blockchain storage
Meanwhile, permissioned blockchains are suitable for applications that require high levels of security and privacy, such as:
-
Identity verification
-
Claims settlement
-
Supply chain tracking
As with anything, it is recommended to consider the pros and cons of both DLT paradigms before committing your funds into them. In a research paper published in the Journal of Software, researchers Solat, Calvez, and Naït-Abdesselam presented a strong case as to why permissionless blockchains are better than permissioned blockchains.
The paper, entitled “Permissioned vs. Permissionless Blockchain: How and Why There Is Only One Right Choice,” presented the following arguments:
Possibility of recalculating next blocks in a closed network
A blockchain system ensures the integrity of data by verifying transactions and protecting historical transactions from tampering. This works in a permissionless network by invalidating the rest of the succeeding blocks when one block is altered.
In a permissioned network, the researchers asserted that “it is possible to recalculate all the next blocks (…) such that all altered blocks will become valid again. In other words, only chaining blocks to each other, based on the hash of the previous one, cannot ensure the integrity and security of the data and protect transactions against tampering.”
Simply chaining blocks to each other isn’t enough
Chaining blocks to each other based on the previous block’s hash isn’t enough. In the paper, the researchers demonstrated how this method “cannot ensure the integrity and the security of the data and protect transactions against tampering.”
As per the researchers, this renders the chaining of transactions no longer meaningful, and this type of blockchain becomes an “unhelpful structure.” The researchers did acknowledge the shortcomings of permissionless blockchains, as well as the appeal of permissioned blockchains. Nonetheless, they highlighted that despite permissionless blockchains’ challenges in scalability in performance, closed networks are still not a good alternative.
A permissioned blockchain does not allow open participation
The researchers argued that a closed network cannot achieve the goal of a blockchain. This is because a permissioned blockchain “does not allow open participation in either submitting transactions or participating in [the] transaction validation process.” Furthermore, “sending a transaction needs some permission beyond mere possession of some way to pay transaction fees or participants cannot fairly expect the network to resist censorship.”
According to the paper, there are three things that a blockchain system must possess all the time:
-
Openness
-
Being public
-
Being permissionless
Under this argument, openness becomes both a “compulsory and necessary feature for a blockchain network.” Permissionless blockchain networks Bitcoin and Ethereum use proof-of-work (PoW), for example, to defeat Sybil attacks. Ethereum has since shifted to proof-of-stake (PoS), which is also a consensus mechanism.
These consensus mechanisms serve to prevent validators from creating spam blocks. They also effectively “force” validators to consume power to defeat the Sybil attack, as per the researchers.
With all that being said, it is still up to the organization to decide whether or not the risks and flaws associated with each network far outweigh the benefits they offer. In the next section, we’ll discuss whether or not the two paradigms can co-exist.
Can permissioned and permissionless blockchains co-exist?
As we delve deeper into this topic, it’s important to look back on the implications of Satoshi Nakamoto’s white paper, in the first place. Nakamoto is a pseudonymous figure known as the “Father of Bitcoin,” who also proposed the complete opposite to centralized institutions such as banks and other financial gatekeepers as a solution to many of the problems with modern finance.
Back in 2008, Nakamoto first outlined a decentralized peer-to-peer protocol for tracking and verifying digital transactions. The blockchain in Nakamoto’s paper was an answer to crises that highlighted the weaknesses of a centralized financial system.
Nakamoto’s blockchain, then, was a permissionless, trustless and stateless blockchain. The system could prevent double-spending and also generate clear, accessible records of transactions for all participants to inspect at any time.
As with anything tech-related, however, once it became apparent that blockchain technology could be used for multiple applications, offshoots from the original purpose were explored. Permissioned blockchains were born to “bridge the gap” between traditional blockchain technology and use cases by organizations that preferred limited access.
As we’ve outlined above, there’s a strong argument against networks with gatekeepers, so to speak. The basic reasoning is that consensus mechanisms like PoW and PoS serve that purpose.
Again, as with anything tech-related, the public (and the powers-that-be) is typically resistant to “public” technologies. We saw this in debates and public acceptance of the following since the 1990s:
-
Cloud infrastructure vs. on-premise infrastructure
-
Internet vs. intranets
But since they are flexible, have more benefits, and have lower barriers to entry, of course, the more public versions of these technologies will prevail. The same is true with permissionless blockchains, which are more widely used now.
However, while public technologies may be dominant, this doesn’t mean that closed technologies have no merit. It can be said that there are still specific use cases and applications that work well with closed technologies.
A permissioned blockchain’s strength lies in its efficiency. It can:
-
Facilitate quick and secure trading among members within a closed group
-
Create a single reference for risk management, compliance and other critical teams within an organization
-
Eliminate unnecessary paperwork
So, it can be argued that in certain business settings and use cases, permissioned blockchains may be more appropriate. For one, permissioned blockchains do not require algorithms to be as complex as permissionless blockchains, since it’s only accessible to a closed group. This makes processing data and transactions more energy-efficient, with a consensus being reached more quickly as well.
The same principle applies to the internet and intranets. The internet is virtually accessible to everyone and is undeniably useful to a larger group of people, correct? However, we also cannot discount the fact that intranets are useful within organizations. A lot of workplaces use them to communicate, collaborate remotely and store confidential files.
In summary, it could be said that yes, permissionless and permissioned blockchains can coexist. It’s just that they have different purposes.


… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More Information here on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Here you can find 51915 more Info on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Here you will find 45314 additional Information to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Find More here on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Here you can find 56200 additional Info on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/3411/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/3411/ […]