The Internet of Things (IoT): A beginner’s guide

What is the Internet of Things (IoT)?
The phrase “Internet of Things” (IoT) has become a household term over the past several years due to the integration of data analytics capabilities and internet connectivity with vehicles, consumer goods, sensors, industrial and utility components, and other objects that promise to alter how we work, live and play.
As a result, numerous Internet of Things-based products and services have begun to be introduced by businesses. For instance, several IoT-related acquisitions have made headlines, including the well-known acquisition of Hiber by Astrocast, Jasper Technologies by Cisco, Solair by Microsoft and SmartThings by Samsung. But what is IoT?
Generally, the Internet of Things refers to scenarios where computing capability and network connectivity are extended to sensors, objects and everyday household items that are not typically thought of as computers. The IoT technology enabled these devices to generate, exchange and consume data with little to no human involvement. However, there isn’t a solitary, inclusive definition.
The most visible example of IoT technology connecting individuals to the Internet of Things directly through their bodies is wearables. These devices can be worn on their faces, such as smart glasses and virtual reality (VR) headsets, or on their wrists, such as fitness trackers or smartwatches, transforming how healthcare services are delivered.
Similarly, consumers are moving toward the concept of the “smart home,” delivering greater security and energy efficiency, thanks to emerging IoT products, such as home automation components, internet-enabled appliances and energy management gadgets.
According to some proponents, the Internet of Things can bring billions of dollars worth of value to businesses and the global economy. They consider it a revolutionary networked, “smart” world of efficiency, advancement and opportunity. Nonetheless, others warn that the IoT heralds a darker era of customer lock-in, spying and security breaches.
The boon-vs.-bane debate and an inflow of information from marketing and media can make the Internet of Things difficult to comprehend. This article will discuss various IoT applications, why IoT is important, how the Internet of Things is changing the world, and the advantages and disadvantages of IoT.
History of IoT
The concept of embedding intelligence and sensors into physical objects was initially proposed when a group of Carnegie Mellon University students decided to modify a Coca-Cola vending machine to enable remote monitoring of its contents. However, progress was slow, and the technology was cumbersome.
Then with the internet’s inception by Tim Berners-Lee in 1989, connecting “things” on the web became common. Here’s a brief history of the Internet of Things that helps understand several developments in IoT technology after the birth of the internet.
1990
The first internet device, a toaster that could be turned on and off through the internet, was developed by John Romkey.
1994
Steve Mann created WearCam, which performed almost real-time on a 64-processor system. Additionally, with its virtual digital city, De Digitale Stad, Amsterdam developed the first smart city.
1997
Paul Saffo provided the first concise explanation of sensors and their future path of action.
1998
Outside his workplace, Mark Weiser (the father of ubiquitous computing) built a fountain. The volume and price patterns of the stock market were mirrored in real-time by the water’s flow and height.
1999
AutoIDCentre executive director Kevin Ashton first used the term “Internet of Things” in 1999. In the same year, they also created a global RFID-based system for item identification. A technique called radio frequency identification (RFID) transmits data via radio frequencies.
2000
As a significant step toward commercializing IoT, electronics giant LG announced its plans to introduce a smart refrigerator with the capability to decide whether or not the food products it holds need to be restocked.
2003
The Unitd States army’s Savi program extensively used RFID. Walmart, a major retailer, increased the use of RFID in all of its stores worldwide that same year.
2005
The Nabaztag, the first smart home gadget similar to Alexa, was introduced that could inform its user about the weather, movements in the stock market and other topics.
2008
The Internet Protocol for Smart Objects Alliance was established in 2008, which aimed to develop frameworks that make deployment more accessible to encourage the use of IoT.
In addition, the Federal Communications Commission permitted the use of the white space spectrum, or the vacant area between the frequencies used for TV, in the same year.
2011
IPv6, the protocol used to locate things on the internet, was launched.
2013
China announced the first group of 90 cities, districts and towns for its pilot program for smart cities. To guide London’s digital technology policy, the mayor of London also established the Smart London Board.
2018
Microsoft unveiled Azure Sphere and Azure Digital TwinsIoT services. Microsoft’s highly secure end-to-end solution for networked microcontroller-powered devices is called Azure Sphere. Building digital clones of physical assets are made possible by the Azure Digital Twins service, which is a crucial tool for scaling analytics and other IoT solution components across thousands of devices.
2020–Present
During the COVID-19 pandemic in 2020, the number of Google searches for the term “Internet of Things” unexpectedly fell by about 15%. The IoT market, however, expanded in 2020 as active Internet of Things connections (such as connected smart home gadgets) overtook non-IoT connections — e.g., laptops, smartphones, etc.
Telehealth, which a doctor uses to treat a patient via video conferencing, was one of the applications that grew significantly during the epidemic. Furthermore, the IoT Cybersecurity Improvement Act was approved as U.S. legislation in December 2020.
The Chinese government announced a three-year plan to build 30 fully connected 5G factories in a press release in January 2021. Bosch, a German automotive supplier, presented its AIoT strategy in February 2021, and Facebook changed its name to Meta in October 2021 to focus on the metaverse concept.
5G networks offered manufacturers new opportunities in 2022, including accelerating IoT adoption through faster data transfer rates and more effective communication and connections among devices. In addition, the synthesis of the Internet of Things and blockchain technology accelerated the adoption of peer-to-peer networking offerings like the Helium Network and enterprise-level supply chain management solutions like VeChain.
How does the Internet of Things (IoT) work?
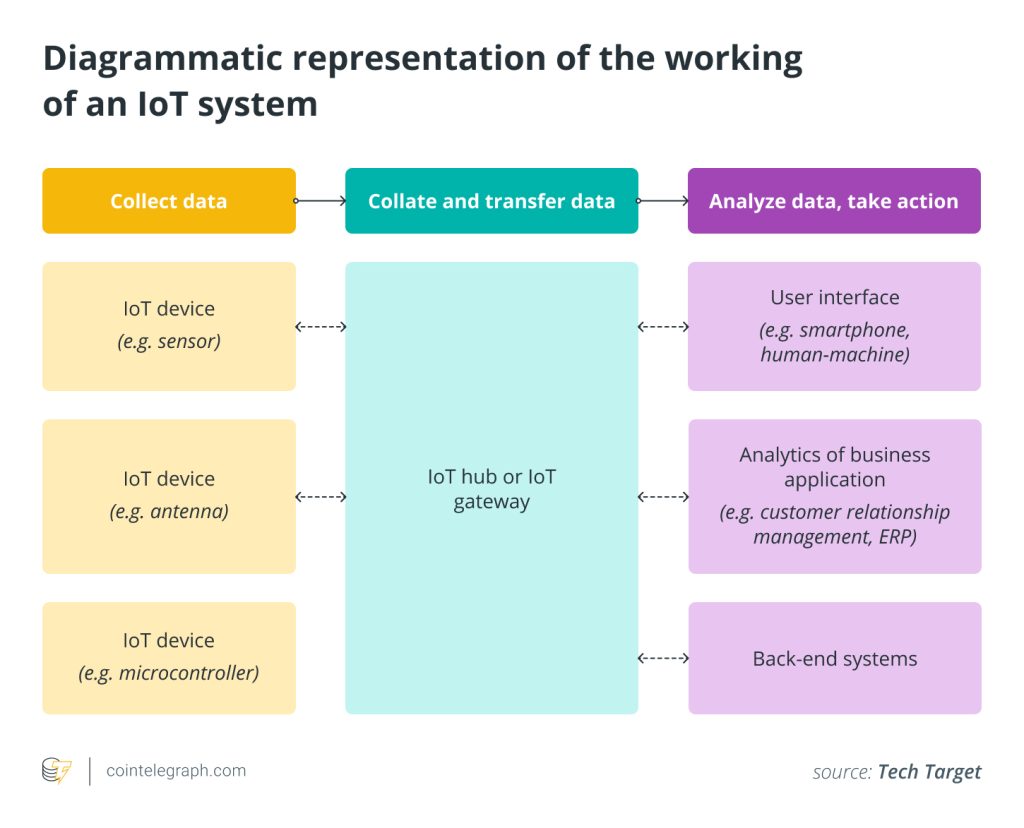
Web-enabled smart devices, such as smartphones, tablets, etc., are part of the IoT ecosystem. These devices use embedded systems, such as sensors, processors and communication gear, to gather, send and act on the data they get from their surroundings by connecting to an IoT gateway or edge device.
A centralized hub known as an IoT gateway links IoT gadgets and sensors to the cloud. Through a variety of communication and delivery methods, including satellite networks, WiFi, Bluetooth, wide-area networks and others, the sensors can be linked to the cloud. Every medium has limitations and trade-offs in terms of bandwidth, range and battery consumption.
Bidirectional data transmission (or two-way data synchronization) between the cloud and IoT devices is frequently made possible by modern IoT gateways. As a result, IoT sensor data may be uploaded for processing, and commands can be sent to IoT devices from cloud-based apps.
The software processes the acquired data once it has been collected and transferred to the cloud. The tasks can be as basic as reading the temperature reading on appliances like boilers or quite complicated, such as when computer vision is used to transform 2D images into 3D models.
Utilizing artificial intelligence (AI), computer vision enables computers to extract valuable data from visual inputs like images and videos. Following that, automated actions are taken using the insights gleaned from computer vision. Although individuals can set up the devices, give them instructions or retrieve data, IoT devices accomplish most of the job without their help.
The information is then made available to the user by setting off alarms on their phones or sending them SMS or emails to alert them. The user might also be able to take action, such as adjusting the boiler’s temperature if it is too hot or cold. Additionally, there are instances where some actions happen automatically. For example, the entire IoT system may alter the settings automatically by developing and implementing a few established rules where no human intervention is required.

IoT-enabling technologies
Different technologies, such as near field communication (NFC), RFID, and virtual and augmented reality (AR), allow physical objects to be identified interactively and referred to through the internet, enabling users to bring physical objects into the realm of the cyber world. Various IoT-enabling technologies are discussed below.
Radiofrequency identification
Radiofrequency identification uses radio waves to wirelessly transmit a serial number that identifies a person or an object. Tags, antennas, readers, software, access controllers and servers are the main RFID components. IoT relies heavily on RFID technology to solve object identification problems practically and affordably.
Near-field communication (NFC)
NFC is a set of short-range wireless technologies consisting of communication protocols for electronic devices, often smartphones. A connection is typically established at a distance of 4 cm or fewer, enabling connecting two different IoT devices with a simple tap-and-go approach and guarding against hackers’ unauthorized access simultaneously.
Internet protocol
Internet protocols are a collection of guidelines that control how people communicate and exchange data online. The internet protocol of the 21st century, IPv6, offers a highly effective multicast communication function that does away with the need for routine broadcast messaging. By reducing the number of packets processed, this improvement helps IoT devices maintain their battery life.
Bluetooth
With an effective range of 10–100 meters, Bluetooth, short-range radio technology eliminates the need for a proprietary cable between devices like laptops, printers and cameras. As a result, IoT driven by Bluetooth can make a significant difference for businesses trying to cut back on human labor and boost productivity.
Additionally, by keeping IoT devices in sleep mode until they are connected, Bluetooth Low Energy, a version of Bluetooth created for low-powered devices, can help IoT devices conserve energy.
Wireless Fidelity (WiFi)
WiFi is a networking technology that enables wireless communication between computers and other devices, maximizing the potential of IoT applications and devices.
Wireless Sensor Network (WSN)
Wireless sensors build the foundation upon which the Internet of Things (IoT) comes to life. A WSN is made up of distributed sensors that track physical and environmental factors, including sound, motion, etc. For instance, sensors attached to a patient’s body monitor how they react to medication so that medical professionals can gauge its effects.
Artificial intelligence (AI)
IoT systems produce enormous volumes of data; thus, AI and machine learning technologies are applied for data analysis to extract actionable insights. For instance, artificial intelligence may evaluate manufacturing equipment’s data and predict that maintenance is required, lowering operational costs and downtime.
Cloud and quantum computing
A centrally located server with accessible computing resources is known as the cloud. The IoT’s enormous data packages can be moved across the internet thanks to cloud computing. In addition, cloud computing is used to store IoT data in a way that is both economical and that facilitates real-time control and data monitoring.
Due to the enormous volume of data generated by IoT devices, which necessitates intensive calculation and other complicated optimization, quantum computing offers exceptionally high speed.
It makes use of quantum cryptography to protect against attacks such as malware and data breaches to safeguard IoT devices. To prevent hackers from accessing data, quantum cryptography uses quantum mechanics concepts for data encryption and transfer.
Blockchain
There is currently no method to verify that IoT data has not been altered before it is sold or shared. The use of blockchain in IoT helps dismantle data silos and promote trust as anyone can verify the authenticity of data on blockchain explorers. Additionally, it can keep track of data gathered by sensors and prevent fraudsters from duplicating it with other harmful data types.
Virtual and augmented reality
Virtual reality (VR) gives Internet of Things consumers a remarkable, immersive experience through a simulated environment, where users can adjust the view angles at their convenience.
Similarly, IoT is a collection of networks that link physical things to the cloud, whereas AR is more of an interactive technology. Together they establish a framework for gathering data for analysis and taking necessary actions. For instance, order pickers can use AR eyewear to quickly access the barcodes of the items they need to ship.
Digital twins
A digital twin is an interactive virtual representation of a real-world system, asset or environment that resembles and functions exactly like its physical counterpart. With the help of digital twins, one can visualize how the system will interact with objects, people and environments by combining data from various IoT devices with data from other sources. It also helps test systems before use, significantly reducing costs and saving time.
IoT communication models
Device-to-device, device-to-cloud, device-to-gateway and back-end data-sharing were listed as the four most popular communication models used by IoT devices in a guide to IoT networking published by the Internet Architecture Board (IAB) in March 2015. The IAB is responsible for overseeing the technical development of the internet.
Device-to-device model
In contrast to using an intermediary application server, the device-to-device communication paradigm depicts two or more devices that connect and communicate with one another directly. Numerous networks, including IP networks and the internet, are used by these devices for communication; however, these gadgets frequently set up direct device-to-device connections via protocols like Bluetooth.
Device-to-cloud model
A device-to-cloud communication model connects an internet cloud service, such as an application service provider, directly to an IoT device to exchange data and manage message flow. This method usually uses already-in-use communication channels, such as WiFi connections, to connect the device to the IP network, which in turn connects to the cloud service.
Device-to-gateway model
In the device-to-gateway model, application software runs on a local gateway device — e.g., a smartphone — that serves as an intermediate between the device and the cloud service and offers security and other features like data translation.
Consumer electronics such as fitness trackers use this model, which usually relies on a smartphone app to act as an intermediary gateway to link the fitness device to the cloud because they lack the inherent capability to connect directly to a cloud service.
Back-end data-sharing model
The back-end data-sharing model enables users to export and combine data from external sources with smart object data from a cloud service for analysis. The data gathered from a single IoT device data stream can be aggregated and analyzed thanks to a back-end sharing architecture.
Layers of IoT
An IoT architecture can be either three-layer, five-layer or service-oriented as explained in the below sections.
Three-layer architecture
The three-layer architecture consists of the perception, network and application layers. The perception layer includes cameras, sensors and RFID tags to identify each object in the IoT system, which accomplishes this by compiling data on each object.
The network layer transmits the data that the perception layer has gathered. Along with the management and information centers, it includes the software and hardware internet network instrumentation. The application layer’s goal is to combine industrial IoT technology with social demands.
Five-layer architecture
The five-layer architecture of the Internet of Things consists of the business, application, processing, transport and perception layers. The goal of the business layer is to manage IoT applications. It is also in charge of user privacy and any IoT application-related research. The types of apps that will be employed in the IoT are determined by the application layer. Additionally, it improves the IoT applications’ authenticity, intelligence and security.
The processing layer handles the information acquired by the perception layer. The two critical stages of the handling procedure are storing and analyzing. This layer uses several methods for processing and storing information, including cloud computing, database software, ubiquitous computing and intelligent processing.
Using technologies like WiFi, infrared and Bluetooth, the transport layer transfers and receives information from the perception layer to the processing layer and vice versa. The perception layer collects data about each object in the system, determines the physical meaning of each object in the IoT system, such as locations and temperatures, and converts this data into signals.
Service-oriented architecture
The service-oriented architecture consists of the sensing, network, service and interfaces layer. To sense the status of things, the sensing layer is integrated with the hardware. The infrastructure for supporting wired or wireless communications is provided by the network layer. The purpose of the service layer is to develop and manage services that users or applications need, and the user or application interaction methods are included in the interfaces layer.
Benefits of IoT
IoT offers many advantages, such as promoting device connectivity, which keeps physical equipment connected and results in less inefficiency and more quality transparency. Also, there is significant automation and control in operation due to physical items becoming connected centrally and digitally via wireless infrastructure. Without human involvement, machines can communicate with one another, producing output more quickly and on schedule.
Since machine-to-machine communication is more efficient, accurate results can be attained quickly, allowing people to perform other creative projects instead of repeating the same daily tasks. However, IoT networks’ increased quality of life benefits everyone, not just humans. For example, internet-connected traffic sensors and lights might help entire communities by reducing congestion in densely populated places.
With the Internet of Things engineering, the interactivity between devices generates tremendous benefits. If a heart patient’s heart rate monitor (through a smartwatch) were connected to their phone so that their healthcare physician could receive this information, imagine the improvement to their overall health.
The majority of physical things deteriorate after being acquired, whereas an IoT product may even get better with time. For example, IoT device manufacturers can update the software exactly like PC businesses can update an operating system because the devices are linked to the internet.
Public policy contributes to citizen safety, and IoT would enable it to be deployed more quickly and precisely. For instance, requiring smoke detectors has been demonstrated to reduce the number of fatalities brought on by fires. Furthermore, IoT is anticipated to contribute to environmental preservation; for example, an IoT-enabled public energy system, SmartGrid, helps measure, monitor and control energy use.
Challenges of IoT
Security and privacy are two significant disadvantages of IoT devices. For instance, data management, preservation and oversight are challenging due to the volume of data created by IoT devices. Adding so many new hubs to the web and systems gives hackers an entry point into the network leading to data breaches and phishing attacks.
Similar to IoT security issues, people may find it challenging to learn that their personal information is being collected due to the passive nature of many IoT devices. Furthermore, IoT devices usually lack screens or other interfaces, making it difficult to give information on privacy policies.
In addition, it may not be possible for an organization to have complete control over IoT devices. For instance, because third-party telecommunications providers typically offer 5G communication technologies, companies frequently have little to no control over security and privacy threats.
When consumers’ or organizations’ data is housed in vendor silos that are incompatible with one another, inconsistent data formats can hinder data portability, making it challenging to switch suppliers while maintaining existing data.
Many Internet of Things devices are not interoperable or lack centralized management with no specific IoT standards, which poses a challenge for organizations. This implies that similar devices might need to be managed separately and that managing devices from various manufacturers frequently necessitates using several interfaces, which can lead to privacy and security difficulties.
The future of Internet of Things
While the Internet of Things has a promising future and expectations are growing, there are still substantial hurdles to overcome, both from commercial and technological viewpoints. For instance, when agile software cultures collide with rigorous hardware not only within firms but even in the early stages of product creation, fundamental managerial issues are likely to appear. This implies that organizations may need to adjust or redefine existing business models.
From a technological perspective, IoT security and privacy remain key challenges that need to be addressed. Future research is being inspired by these issues, with the other concerns being the effects of IoT-based innovation on corporate IT infrastructures and strategy.


… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] There you can find 97286 additional Info to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More on on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More Info here on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Here you can find 90111 additional Information to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More on on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/3168/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3168/ […]