DeFi Scams 101: How to avoid the most common cryptocurrency frauds

Cryptocurrency scams ruining DeFi enthusiasm
As many crypto enthusiasts will state, decentralized finance (DeFi) represents a revolutionary next step in terms of finance. Such a new space can potentially offer users new ways to make money while contributing to a larger-than-life community-run purpose.
That said, DeFi’s innovations also come with some downsides. The industry is full of cryptocurrency scams, Bitcoin (BTC) fraud, blockchain scams and other wallet-threatening scenarios.
In 2021 alone, cryptocurrency scams and theft in the DeFi sector totaled over $12 billion in crypto assets stolen from user wallets, as well as exchange holdings. Part of this theft was due to poorly programmed smart contracts and weaknesses in platform security, but the rest were due to cryptocurrency fraud, with bad actors taking advantage of users new to the space.
For the crypto scene to actually expand into the mainstream, the industry must see these scams and security weaknesses taken care of. Unfortunately, it may be some time before the industry solves the issue of blockchain scams. Until that time comes, this guide intends to educate users on how cryptocurrency scams work and how to recognize crypto scams.
How DeFi improves on traditional finance
While the benefits of decentralization may be evident to crypto enthusiasts, one cannot understate the security and accessibility upgrades that come with a decentralized finance network. DeFi upgrades can bring significant positive changes to mainstream finance despite the current cryptocurrency scammer list of attacks.
With traditional finance, banks and online platforms have one central point of contact: a server. While servers have extensive levels of security, there’s little a company can do if its servers are broken into. Once a thief is in, they have access to valuable information like passwords and addresses.
Decentralization, however, distributes access to various points of contact all over the world: the users. Often called nodes in a DeFi network, users are usually incentivized to hold parts of the network on their connected device. Ideally, the more nodes connected to a network, the more secure it will be. Instead of a central point of attack, a bad actor would need to take control of 51% of the nodes connected to a network, which isn’t impossible but is very unlikely to occur.
Nodes also lend themselves to accessibility. Because a network is distributed worldwide via users’ devices, anyone can connect to and use whichever decentralized network they choose. When connected to the network, users can send funds and interact with the network in other ways without the barriers that exist in traditional finance.
For example, one can send funds across the world to a family member nearly instantly, absolving themselves from fees and wait times associated with traditional international transfers. Additionally, there’s no central entity to block users’ transactions or charge them extra for inexplicable reasons.
Nodes also retain complete control over a DeFi network’s changes and upgrades. Users must propose and vote on a change to implement it, compared with the traditional method of a centralized entity implementing changes regardless of users’ wants and needs. If a network experiences a suspicious transaction, it’s up to the users to vote on and reverse it. Decentralization indeed provides users the authority to make decisions.
That said, with all of the power that DeFi provides, that power comes with its own set of problems such as fraud, human error and bad intent — and a responsibility to solve them.
Various ways hackers use to commit cryptocurrency fraud
To many, handing power to the users via blockchain is appealing in its own right. It’s easy to understand how users might be sick of centralized entities telling them what to do. But, with great power comes great responsibility, and if DeFi creators fail to meet those responsibilities, the consequences can be dire.
Humans build decentralized finance platforms with programmers arranging various actions and capabilities to offer their features. However, with human input comes human error, and man-made error is where the exploits come into play.
In the world of DeFi, projects appear left and right. Being first to the game is vital to one’s success, and programmers rushing their code are bound to leave vulnerabilities. Considering blockchain projects are entirely open source, meaning their code is available to all, those with evil intent will find those vulnerabilities and use them to steal funds and otherwise abuse a platform.
While code can be reviewed and fixed via a third-party audit, this process is expensive, especially in the nascent blockchain industry. Many projects struggle to acquire funding just for basic development. Finding the funds for an audit can be difficult, and projects may move ahead without a proper code examination.
Of course, platforms in traditional finance, built on conventional code and servers, aren’t immune to human error and attacks either. That said, traditional platforms are programmed from tried and true security methods with decades of testing in the field and don’t have the challenge of programming automated smart contracts. Blockchain-based platforms don’t have the luxury of that experience, meaning errors can sprout up with no prior warning while developers scramble to find a solution.
Then there’s the problem of ambition. Some projects are (relatively) simple token swap platforms, enabling users to swap one token to another with ease. Others are looking to tokenize and automate the entire world in which we live, providing users with new ways to experience traditional applications and services. As platforms become broader with more varied intentions, building smart contracts that interact with other smart contracts, among other functions, means that more errors are bound to appear.
Sure, decentralization is half of what makes DeFi, but some platforms take decentralization more seriously than others. If a project is too centralized, it runs similar risks to traditional finance platforms existing on conventional servers despite promising the opposite. Bad actors would likely have a much easier time attacking these less decentralized platforms as a result.
How to recognize crypto scams and DeFi scams and how to avoid them
While it’s impossible to prevent crypto fraud and theft throughout the industry, the following common scams should be a part of every DeFi trader’s watchlist.

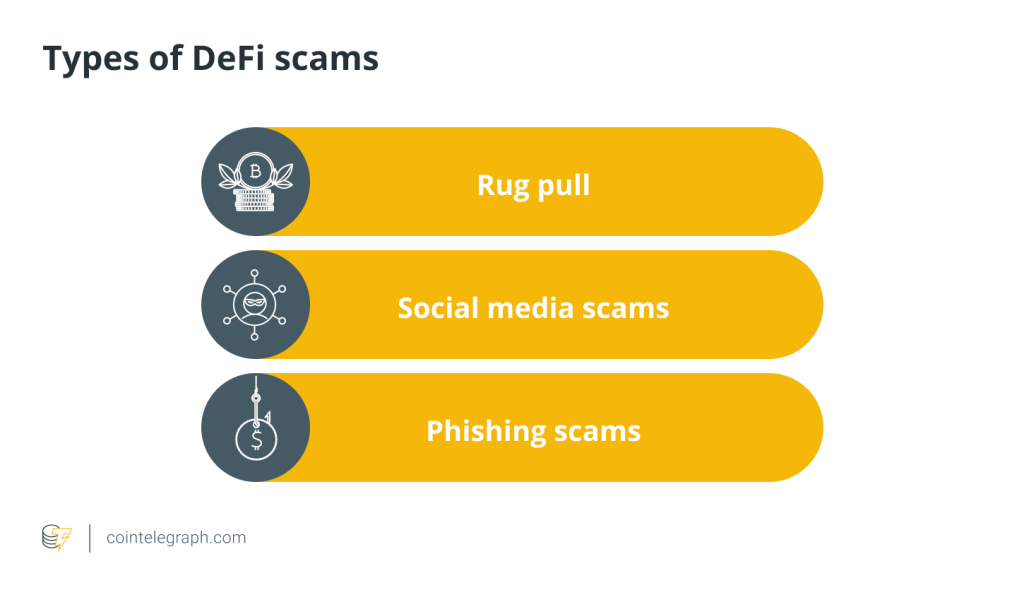
A rug pull
Rug pulls are arguably the most common cryptocurrency scams in the DeFi space but can be one of the easier ones to spot for those who know what to look for.
A rug pull is when developers promote what appears to be an exciting revolutionary project. They gain a following and gather hundreds of thousands, if not millions of dollars, in support from investors.
Then, one day, these developers simply sell the tokens and disappear with the funds. These developers never intended to build a project with investors’ money. They simply wanted to conduct a scam. Investors will suddenly have nothing and the project will cease to exist. Investors essentially get the rug pulled out from underneath them.
By paying attention to a developer’s relationship with their communities, as well as their token distribution plans, it can be easy to spot a rug pulled from a mile away. If a project fails to detail any sort of token lock-up period, especially a lock-up period for the developers, then these teams can do whatever they’d like with tokens at any point.
It’s best to align with projects that have detailed token lock-up periods to prevent developers from running off with funds. These projects will generally be very open with their community, providing consistent updates and a long-term plan. (While not exclusive to DeFi, a pump and dump scam is very similar to a rug pull.)
When a project is declared “unruggable,” it signifies that the development team has not contributed many tokens. For example, a project could be termed unruggable if it lacks the considerable hallmark of team-held tokens that could be taken in a rug pull or exit scam.
Another approach to consider an unruggable project is if the team relinquishes control of any tokens, such as those obtained during a presale.
Social media scams
All over Twitter are scam accounts impersonating various celebrities — some in the crypto space and others not. Regardless, these impersonators will reach out to crypto enthusiasts regarding their new project and might pretend to hold giveaways and competitions where users must send funds to a specific address.
It’s easy to check if these accounts are legitimate. For example, an impersonator will probably have a few thousand followers compared to the millions of followers on the actual celebrity account. These accounts often have basic grammatical errors and misspellings. Regardless, one should simply never respond to or send funds to an account on Twitter in the first place.
Such a seemingly simple cryptocurrency fraud plan might sound ridiculous, but they occur daily. In fact, in 2020, bad actors hacked legitimate celebrity accounts to send out such scammy tweets.
Phishing scams
Phishing is a scam tactic as old as the internet — one where scammers pretend to be legitimate companies and gather personal info about their victims.
DeFi phishing is usually conducted via email, with a bad actor pretending to be a representative from a trading platform or protocol. A scammer will make up an error such as “your account has been compromised. Send over your email and password so we can secure it.” Such tactics can include asking for wallet addresses and passwords, or demanding the victim send over funds.
Phishing emails might link to fake websites similar to an existing platform, enticing victims to input their private information only to have it stolen by the scammers.
To prevent falling for phishing blockchain scams, one must always check the contact’s email address. Often, the email will be full of random characters instead of an actual website name. Otherwise, never click on a link in a suspicious seeming email. If there may be a legitimate security problem, navigate to a platform’s website manually and double-check URLs to avoid such scams. For example, ensuring the URL has an https security certificate and that the URL is spelled perfectly correct.
General security measures to follow
It’s vital to keep an eye out for the aforementioned scams and frauds within DeFi, but some generalized methods exist to help one stay off of a cryptocurrency scammer list.
Two-factor authentication (2FA)
No matter which realm of DeFi one chooses to invest within, all platforms should have some form of two-factor authentication. 2FA is a security method that sends a text or email to a verified account, required after one inputs their password. This way, even if a bad actor gains access to one’s password, they’d need access to a mobile device or email to actually break into an account.
Use a hardware wallet
Hardware wallets are external devices in which users can store their private keys. As the DeFi space develops, more decentralized applications (DApps) are becoming compatible with hardware wallets, meaning users can store their assets in a secure space while still easily accessing their DeFi platforms of choice.
It’s difficult to recommend storing one’s assets in an online wallet, even if a platform provides that wallet. By holding assets online, users leave their funds open to theft. DeFi attacks often result in thousands of users losing millions in funds. By removing a platform’s access to users’ funds, users are stepping their security up one level higher.
Investigate a community
Successful DeFi projects often cultivate a fruitful community full of active users and developers who communicate back and forth. Such communication is vital to safely develop a platform everyone can enjoy.
That said, if there’s a project with inactive or quiet developers, they may be planning a rug pull or other type of scam. Crypto enthusiasts will always say that it’s best to know the team behind a project. If a team keeps their plans a secret or does not communicate with their community, there’s reason to believe they have bad intentions.
It is considered best to get involved in projects with thriving communities and, even then, do some additional research before forming an opinion. One can also pay attention to listing platforms and why they may or may not include a token. If a listing platform denies a token, it’s probably not one to invest in.




… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] There you can find 96886 more Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More Info here to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More here on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] There you can find 87230 additional Information to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] There you will find 93592 more Info to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Here you can find 63899 additional Info to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Here you will find 22639 more Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More here to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] There you will find 65519 additional Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] There you will find 82634 additional Info on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/2553/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/2553/ […]