What is two-factor authentication (2FA) and how to use it in crypto

Two-factor authentication (2FA), which increases account security, adds an additional layer of defense. Users can set it up by logging into the security settings of their crypto platform, selecting a preferred 2FA method, such as an authenticator app or SMS, and then following the setup steps to protect their assets from illegal access.
Two-factor authentication, explained
Two-factor authentication is a security process that requires users to provide two distinct authentication factors to access an account. By introducing a second layer of verification in addition to a password, it improves security. The two factors involved in the 2FA process include:
- Knowledge factor: This is anything that the user is aware of, such as a PIN or a password.
- Possession factor: This refers to something the user possesses, like a smart card, security token or mobile device.
The theory behind this method is that even if someone were to learn or guess a user’s password (the knowledge factor), they would still require the second factor (possession) to access their account. As a result, the risk of unauthorized access is considerably reduced because it is much more difficult for attackers to penetrate.
Two-factor authentication is often used, and common solutions include getting a one-time code by SMS, generating codes using a mobile app, such as Google Authenticator or Authy, or using biometric information, such as fingerprints or face recognition.
Since two-factor authentication greatly improves cybersecurity and shields critical data from illegal access, it is frequently used to secure a variety of online accounts, including email, banking, social media and cryptocurrency wallets.
Two-factor authentication methods
Various two-factor authentication methods include:
SMS or text message codes
Users receive a one-time code through SMS, which they must enter to finish the login procedure. This is known as SMS or text message codes. Though SMS messages can be intercepted, this method is less secure than others.
Mobile authenticator apps
Users can download a mobile app that creates time-based, one-time codes, such as Google Authenticator or Authy. These apps are synchronized with the server and randomly generate the codes at brief, predetermined intervals that are long enough for users to enter them when logging in.
Email codes
To complete the login process, the user must input a one-time code that is provided to their registered email address.
Hardware security tokens
These physical devices either produce one-time codes or have buttons that must be pressed to authenticate users. They can be pricey, but they are quite secure.
Biometric verification
Users can authenticate themselves via biometric verification, which compares their provided biometric identifier, such as a fingerprint or facial scan, to stored biometric information.
Backup codes
During setup, users are given a set of one-time backup codes. If the primary 2FA technique is not accessible, these can be employed.
Push notifications
When a login attempt is made, users get a notification on their mobile device. The request may be accepted or rejected.
Related: The worst places to keep your crypto wallet seed phrase
Before using any of the above listed methods, users must weigh the pros and cons of each method to avoid losing funds. A notable case involved a Coinbase customer in March 2023 who sued the company for over $96,000 in losses due to SIM swapping, igniting a debate on SMS 2FA security.
How does two-factor authentication work?
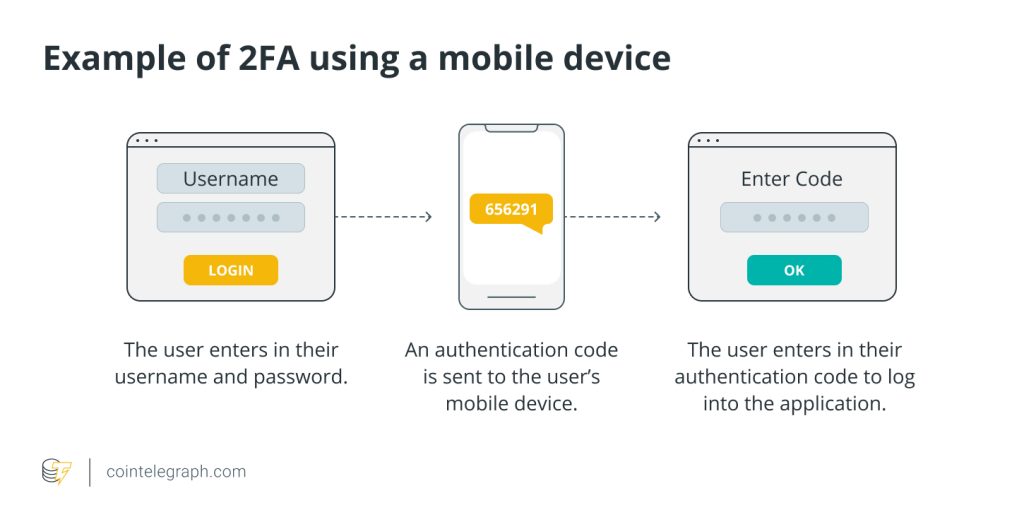
Usually, one needs both something they have (like a mobile device or hardware token) and something they know (like a password) to access their accounts secured using the 2FA process. Here’s how 2FA works, step by step:
The user initiates a login
When a person attempts to log in to an online account, such as an email account, a social media account or a financial website, the procedure starts.
The user shares something they have
A username and password are frequently used as the first factor because they are something that the user is likely to know; this is the first stage in authentication. As usual, the user inputs their login and password.
The server validates the first factor
The first factor is validated by the server, which compares the supplied login and password to its database to see if they match. The first authentication factor is confirmed if the credentials are accurate, but access to the account is not yet given.
The server requests a second factor
Following the successful verification of the first factor, the server asks the user for the second factor. The user contributes something they own: A cell phone, a hardware token or an authentication app are examples of items the user typically has access to physically as the second factor.
The user provides something they have
The user’s physical possession of a mobile phone, a hardware token or an authentication program typically serves as the second factor. There are numerous ways to use the second factor, including hardware tokens, SMS codes and email codes.
The user enters the second factor
The user enters the one-time code or offers the second factor as required. This code is continually changing and time-sensitive, increasing security.
The server validates the second factor
The second factor is verified by the server, which verifies that it corresponds to the predicted value. The second authentication factor is confirmed if it does.
Access is granted, and the session gets established
The server gives access to the user’s account if both authentication factors — something the user has and something they know — are properly validated. The user is then logged in and has access to their account and its features due to the session being established.
How to setup two-factor authentication for crypto
There are various steps involved in setting up 2FA for cryptocurrencies. The user should first download a trustworthy authenticator app to their smartphone, such as Google Authenticator, Authy or a comparable one, from their app store.
The user must next provide their login and password to access their cryptocurrency account. The user should find the 2FA section of the account security settings and click “Enable 2FA.” To link their account to the app, they must then open their authenticator app and select “Scan QR Code” or “Add Account” before scanning the QR code shown on the crypto platform.
Some systems might give users backup codes, which they should store in a safe location. If the user misplaces their phone or the authenticator app, they can use these backup codes to recover access to the account.
The user must enter the time-based, one-time password (OTP) produced by the authenticator app into the cryptocurrency platform to complete the setup. They can log out of their account and then try to log back in, at which point they will be asked to enter the OTP from the app to test the 2FA setup.
If the app provides recovery keys, the user must safely keep them offline. In the event of phone loss or app problems, these keys can be used to reclaim access to 2FA-protected accounts. Alternative 2FA techniques, such as SMS or email verification, may be available from some exchanges, but utilizing an authenticator app is generally thought to be more secure.
Finally, the user should regularly examine and update their 2FA settings, making sure that their authenticator app is kept up-to-date and their recovery information is accurate. As a result, their cryptocurrency accounts are securer overall, making it much harder for unauthorized parties to access their money. Users should never divulge their recovery information, OTPs or recovery keys to anyone.
How to set up two-factor authentication on Coinbase
The steps below explain how to set up two-factor authentication on Coinbase:
- Go to Coinbase’s security settings at https://www.coinbase.com/settings/security_settings.
- Scroll down to the “2-Step Verification” section.
- Select “Authenticator.” Users will need to confirm their existing 2FA or approve via SMS if they are a new user. Existing clients updating 2FA must confirm with their current 2FA.
- Enable authenticator support. After approval, a QR code will appear in a pop-up window.
- Scan the QR code using the Authenticator app.
- Enter the six-digit code and click “Enable.”
If multiple users use the same login, they must all scan the QR code for 2FA enrollment. They can either gather everyone in one location for the scan or, for remote setup, hold a video call with screen sharing.
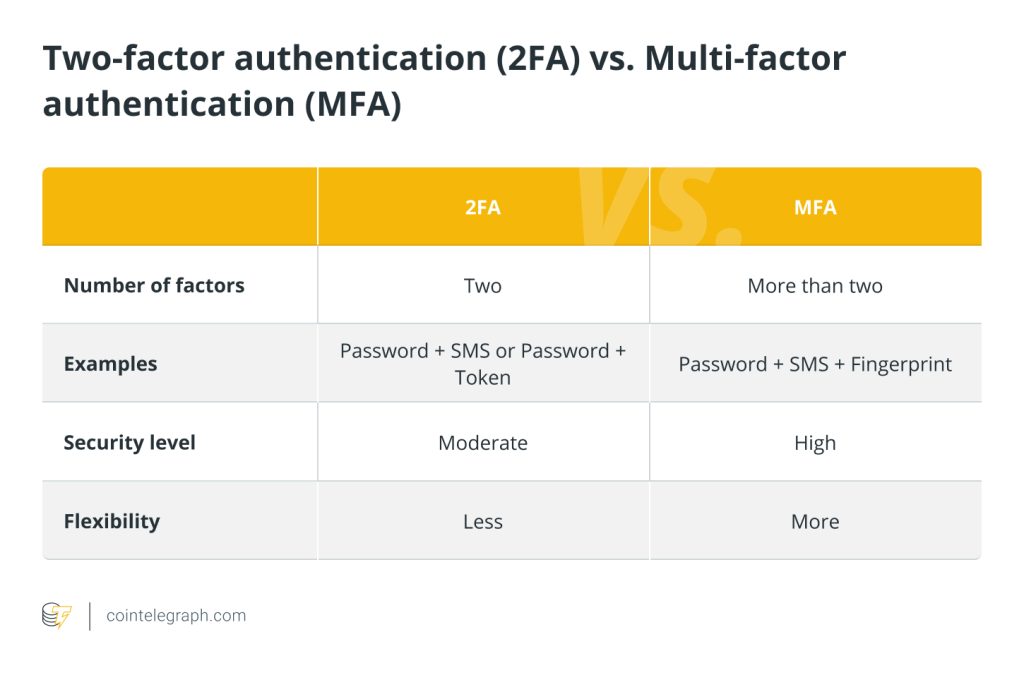
Two-factor authentication vs. multi-factor authentication
To authenticate their identity while logging in to their accounts, users must employ two or more different authentication factors. This is known as multi-factor authentication (MFA). MFA increases security by requiring additional elements such as biometrics (like fingerprints or facial recognition) or additional possession factors (smart cards), in contrast to 2FA, which only requires two factors (typically something known, like a password, and something possessed, like a smartphone).
This multi-layered approach offers greater flexibility for customizing security measures to specific requirements and risk levels and considerably improves security by making it much harder for unauthorized users to acquire access.
Here’s a quick summary of 2FA and MFA:

Security issues with two-factor authentication
Even though 2FA helps improve security, it is not impervious to security problems. Users may be duped into supplying both factors during phishing attempts. Moreover, attackers are able to intercept SMS codes by switching SIM cards. Some authenticator apps are vulnerable to malware infection. Therefore, backup codes need to be kept safely because losing them can result in lockouts.
Similar to fingerprints, biometric 2FA can be evaded using copies. Lastly, if users disregard or disable 2FA, user complacency may reduce its effectiveness. Despite these concerns, 2FA is still a useful security measure, and its risks can be reduced by careful user behavior and, whenever possible, the use of multiple authentication methods.


… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Here you will find 37730 more Info to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More here on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Information here on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Here you will find 31882 additional Information on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] There you will find 98642 additional Info on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/2230/ […]
cinemakick
… [Trackback]
[…] There you will find 40288 additional Info on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More on to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More here to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] There you can find 32285 more Info to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/2230/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/beginner/2230/ […]