How the Peraire-Bueno brothers allegedly drained $25M from their MEV bots exploit
The Peraire-Bueno brothers have been charged with fraud in a first-ever MEV bot exploit case. Here is what the DOJ claims they did to pull it off.

On May 15, the United States Department of Justice (DOJ) charged two brothers, Anton and James Peraire-Bueno, with allegedly carrying out an attack on the Ethereum network that resulted in $25 million being transferred from maximal extractable value (MEV) bots to the defendants. The indictment claims that the attackers, through their Ethereum validators, proposed blocks whose ordering was so malicious that it constituted the crime of wire fraud.
The charges were revealed in a grand jury indictment that laid out the DOJ’s view.
The case has divided the crypto community. Some claim that the MEV bots were themselves attempting to defraud the brothers and that the defendants should not be seen as victims, while others say the brothers were in the wrong for exploiting bad code. Some have also argued that the case sets a dangerous precedent and will lead to full-scale regulation of Ethereum.
The technical nature of the case has only compounded the controversy further, as terms like “MEV,” “searchers,” “relays,” “sandwich attacks” and others that may not be understood by all Ethereum users are being tossed around in the discussion.
The following is an exposition of how the brothers allegedly carried out their attack.
What is maximal extractable value?
According to Ethereum network documents, MEV refers to the maximum value that can be extracted from a block of transactions based on their ordering.
Some on-chain trades will be more beneficial to a user if they go through in a particular order. For example, a trader who wants to use their stablecoins to buy a large amount of Ether (ETH) when it’s at a low price will not want another trader to be able to buy it in size first, as the first trader’s purchase may cause the price to increase. In some cases, the user may prefer not to trade at all if they can’t place their trade in priority.
Under normal circumstances, when a user posts an Ethereum transaction, it gets sent to the network’s memory pool, or “mempool,” where it is stored until it is either canceled or confirmed and added to the blockchain. Once it is in the mempool, any device on the network can view its contents.
This means that if a trade is placed through the normal method, another trader can potentially copy it and have it executed first. In this case, the trader who originally posted the trade will pay a higher price for the asset they are buying. The process of copying other traders’ transactions and executing them first as su is called “front-running.”
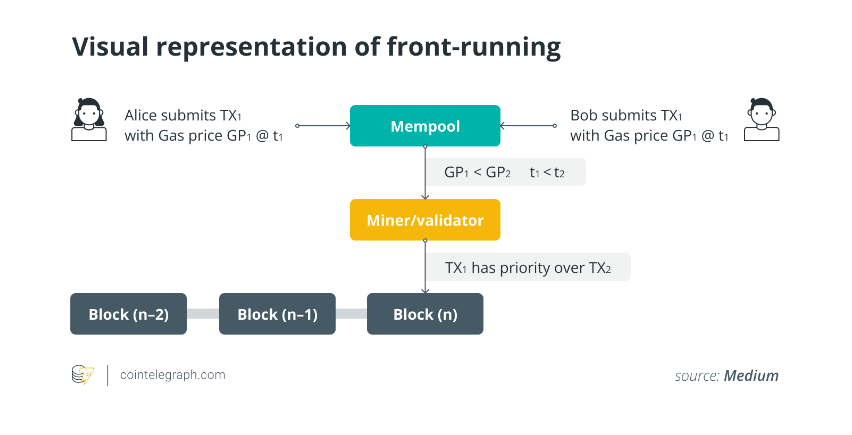
If a trader can front-run a trade, they can potentially profit by performing a “sandwich attack,” which involves first buying up the asset to make the subsequent trader pay a higher price, then selling into the liquidity pool after the subsequent trader’s transaction has been executed.
To defend against sandwich attacks, most decentralized exchanges today submit transactions directly to a whitelisted group of block-builders, bypassing the mempool entirely. This prevents bots from detecting the users’ transactions and copying them.
Related: 1inch releases new tool to protect traders against ‘sandwich attacks’
However, some traders still submit their transactions directly to the mempool, thereby opening themselves up to the possibility of a sandwich attack.
If a user does submit a trade to the mempool, other users — which are typically bots — will compete with each other to sandwich-attack the original user. In this case, the bot that pays the highest gas fee to the validators will have their transaction executed first and will, therefore, be able to perform the attack.
However, the attack will only be profitable if the gas fee paid is less than the profit from the attack. Therefore, the bot should theoretically only be willing to pay an amount equal to or less than the profit. This amount, the maximum amount of gas a user should be willing to pay to execute an arbitrage, is called the “MEV.”
MEV doesn’t only refer to the extraction that occurs in sandwich attacks or front-runs, though. It can also describe other arbitrage opportunities that arise from the order of transactions, such as profits from liquidating bad loans.
However, the Peraire-Bueno case specifically involves bots that were attempting to perform a sandwich attack, so the other types of MEV are not relevant in this instance.
The MEV ecosystem
To understand the claims made in the indictment, it’s also helpful to consider how the MEV ecosystem works today.
In the early days of Ethereum, individual firms ran MEV bots that were also validator nodes. This led to rampant competition and a reduction in profits. However, most nodes today use the Flashbots system, which allows bots to hide their profitable arbitrages until the moment their transactions are added to the blockchain.
This allows them to earn bigger profits through custom coding, as their arbitrage transactions are never added to the mempool and cannot be copied.
Flashbots has also allowed traders to hide their own trades to defend themselves against sandwich attacks.
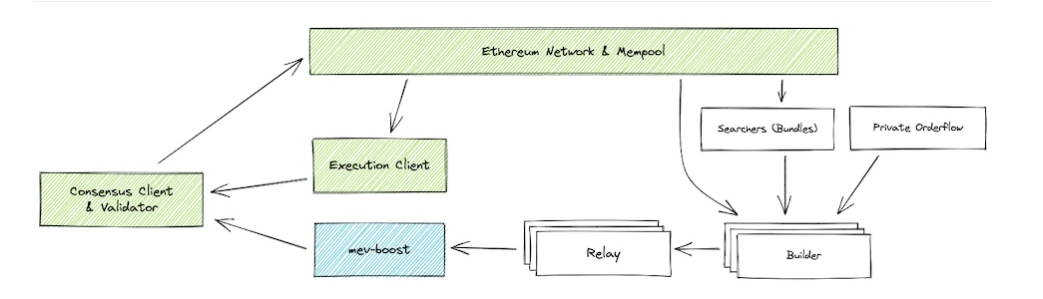
According to its documents, in the Flashbots system, some computers play the role of “searchers.” They use proprietary code to scan the blockchain for arbitrage opportunities. Once they find a set of profitable transactions, they order them into a bundle and send them to a “builder” computer.
The builder computers collect bundles from the searchers, as well as transactions from traders who want to bypass the mempool. These bundles and extra transactions are sent to relays, which take in transactions from multiple builders and use them to create a proposed block.
Once a relay has created a proposed block, it offers a gas fee to the validators in exchange for a commitment to confirm its block after publishing. The relay attempts to propose a high enough gas fee that its block will likely be published, but not high enough to make the various individual trades unprofitable for its clients — the individual builders, searchers and users.
If a validator node wants to publish a relay’s block, it responds with a signature committing itself to confirming that block. Only once the signature is transmitted does the relay reveal the transactions within the block. The block is then added to the blockchain after other validators on the network confirm it.
The Peraire-Bueno brothers are accused of exploiting this flashbots MEV system, transferring $25 million to themselves by tricking the system into believing that a profitable arbitrage existed, when, in fact, the “arbitrage” resulted in losses for the searchers who discovered it.
Related: MEV bot pulls $1.7M profit from a single ‘inefficient’ Dogwifhat trade
How they allegedly exploited the MEV system
According to the indictment, the two brothers carried out the exploit by first creating 16 Ethereum validator nodes. Through these nodes, they published a set of “bait” transactions that appeared to be lucrative MEV opportunities. Relays picked up some of these transactions and included them in blocks, while others were not included. Over time, the accomplices used these test transactions to determine how to guarantee that their transactions would be included in a relay’s block.
Once they were sure they could get their transactions included in a block, they waited for one of their 16 validator nodes to get chosen as a block producer. They then published eight “lure” transactions that they wanted included in a block. These transactions were picked up by three different searchers and were ultimately included by a relay. After building blocks that included the transactions, the relay published the header for its block and requested the brothers’ node to confirm it.
The brothers’ validator node responded by producing a fake signature committing to propose the relay’s block, the indictment alleges. Due to a flaw in the cryptographic system used to produce the signature, it was possible for the node to fool the relay into believing it had signed the message, but in fact, the signature was not valid and would not be accepted by other validator nodes as a firm commitment. The indictment states:
“After the Relay released the blockheader for the proposed block which contained the Victim Traders’ ordered transactions, […] the defendants, exploited a vulnerability in the Relay’s computer code by sending the Relay a false signature […] in lieu of a valid signature. Based on their research and planning prior to the exploit, [the defendants] knew that the information contained in the False Signature could not be verified for ultimate publication to the blockchain.”
Once this fake signature was transmitted, the relay published the contents of its block. In response, the validator reordered the block and signed it with the real signature, officially proposing the reordered block instead of the one the relay had preferred. As a result, this reordered block was confirmed by other validators, the indictment claims.
In the original block proposed by the relay, the three searchers first used stablecoins to purchase a large number of highly illiquid tokens, pushing up their prices. Afterward, the brothers purchased these same tokens at a higher price. This resulted in a large amount of stablecoins being transferred into the exchange’s liquidity pool.
The searchers then unloaded the tokens they had just purchased, draining the pool of the stablecoins that both parties had just put into it. Finally, the brothers sold their tokens into the now-drained pool, causing them to receive much less for the tokens than they originally paid. In essence, the original block executed a classic sandwich attack against the brothers.
However, the reordered block did something very different. In it, the brothers purchased the tokens first, pushing up their prices. Then, the searchers purchased more tokens, draining them from the pool and replacing them with stablecoins. After the searchers made their purchase, the brothers sold their tokens into the pool, draining most of the stablecoins out of it.
Finally, the searchers attempted to resell their tokens. But at this point, the pool no longer had enough liquidity to buy back the tokens. As a result, the final transaction failed, and the searchers were stuck with essentially worthless tokens.
Because the reordered block was confirmed instead of the original, the brothers profited $25 million in stablecoins from the trade, while the searchers lost $25 million. Essentially, the brothers reversed the sandwich attack, causing the attackers to lose money instead of themselves.
In the Justice Department’s view, this action constituted “wire fraud” because the lure transactions and false signature were “material representations,” binding statements made from one party to another in a commercial transaction, and because they were knowingly sent to deceive the MEV bots. As the indictment states:
“The defendants […] engaged in a scheme to defraud the Victim Traders, by making material representations, [including] the Lure transactions and False Signature, in order to fraudulently obtain cryptocurrency.”
The Peraire-Bueno brothers have not been arraigned, and no trial date has been set as of the time of publication.
The crypto community responds
The case has been controversial within the crypto community.
Some Ethereum users have expressed incredulity at the DOJ’s view that MEV bots, which were allegedly attempting to sandwich-attack traders themselves, deserved to have their opponents thrown in jail.
For example, on May 15, Helius Labs CEO Mert Mumtaz asked rhetorically on X, “Hold up. These guys are being charged with wire fraud for *checks notes* baiting MEV bots on Ethereum??????” TradingStrategy co-founder Mikko Ohtamaa argued that the DOJ is practicing a double standard. “You are only allowed to sandwich retail users,” he claimed. “When you sandwich MEV bots then you are a criminal and MEV bot operator sues you in the nearest US court.”
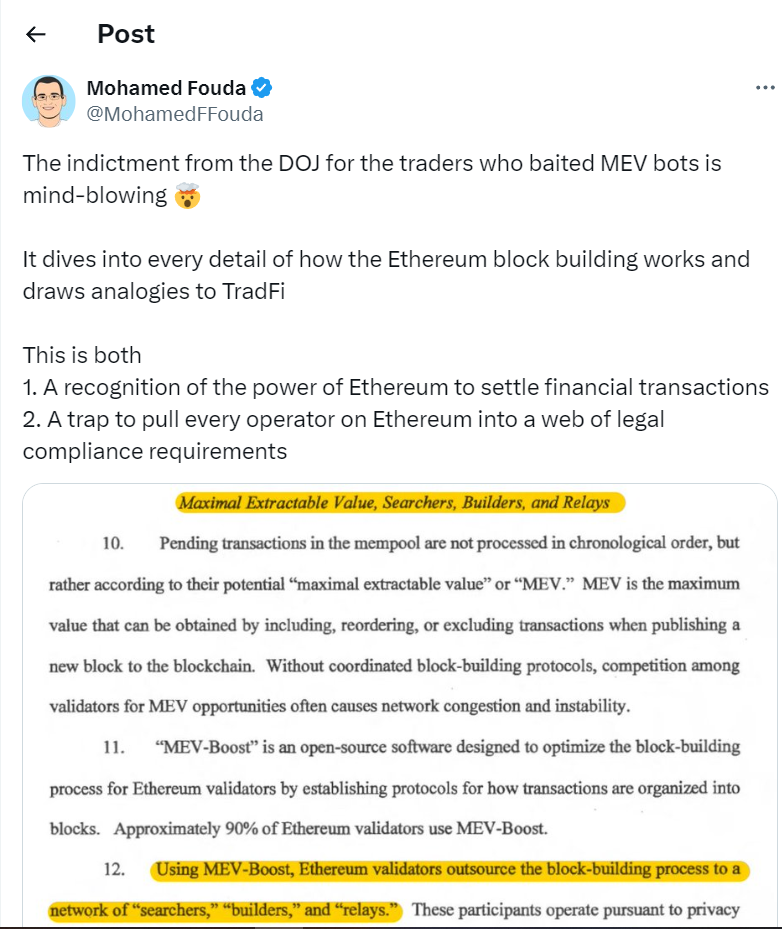
AllianceDAO contributor Mohamed Fouda argued that the case creates a slippery slope, as it may lead to full-scale regulation of Ethereum. The indictment is both “a recognition of the power of Ethereum to settle financial transactions” and simultaneously “a trap to pull every operator on Ethereum into a web of legal compliance requirements,” he claimed.
The indictment “legitimizes the harmful behavior of Sandwich attacks and frontrunning,” treating them as normal, Fouda stated, which he considers to be “catastrophic.”
In addition, it “draws a faulty picture of the roles of relayers in the Ethereum system,” treating them as escrow services. Fouda claimed that this treatment was “probably to tie them to specific ‘responsibilities’ and ‘duties’ they owe to the MEV searchers,” which can cause Ethereum operators to be subjected to “multiple compliance requirements.”
While some users shared these criticisms, others defended the DOJ’s actions. Crypto trader Beanie posted to X on May 15 to argue that “exploiting software for gain is always illegal,” adding that “code isn’t law. Lots of precedence here.”
Polygon Labs vice president Hudson Jameson expressed a similar view in a reply to Fouda’s post. “It wasn’t simply baiting bots and sandwiching,” he claimed. “They actually exploited a flaw in MEV boost itself.” In response, Fouda conceded that “what they did is probably a crime” but argued that it “doesn’t negate the fact that sandwich bots are Ok or business as usual.”
The practice of obtaining MEV has been controversial since the beginning of the Ethereum network. Some networks have attempted to prevent what they consider to be “malicious” MEV in various ways. For example, Shutter claims to use threshold encryption to stop front-running and sandwich attacks, whereas Neo X has stated that it accomplishes a similar aim using a delegated Byzantine fault tolerance consensus mechanism.
However, these are technical solutions to the perceived problem. So far, there are no known cases of sandwich attack victims attempting to prosecute MEV bots for wire fraud.
Related: Vitalik Buterin proposes solutions for Ethereum’s MEV problem





Responses