Mystery malware targets Call of Duty cheaters, stealing their Bitcoin
Malware database vx-underground has warned of a new info-stealing malware in cyberspace that is targeting video gamers, especially those who use cheating software.

A new flood of mystery malware has reportedly been targeting video gamers and draining their Bitcoin (BTC) wallets as part of a new info stealer campaign, which also has been targeting cheaters.
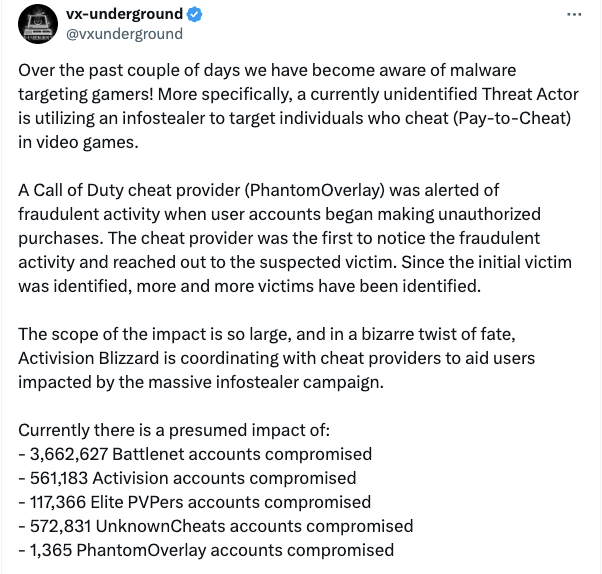
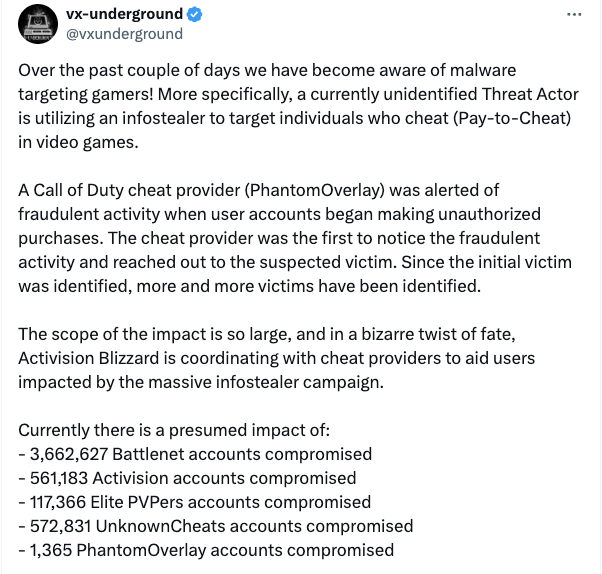
Malware information repository vx-underground said in a March 28 X post it was aware of a “currently unidentified Threat Actor” using malware to steal login and other credentials of those using pay-to-cheat video game software.
The attacks target players, including those who buy cheating software, and have compromised over 4.9 million accounts for Activision Blizzard users and its game store Battle.net along with accounts for a game-focused trading site Elite PVPers and cheat software markets PhantomOverlay and UnknownCheats.
“Impacted users have begun reporting being victims of crypto-draining — their Electrum BTC wallets have been drained. We do not have any information on the amount of money stolen,” vx-underground wrote.
In a March 27 Telegram post, PhantomOverlay claimed the number of hacked accounts “are inflated” as over half of the logins in a database it viewed “are invalid garbage.”
It added the malware “seems to be an entire network of free/cheap software” that has originated from “some latency program, VPN, or something that millions of gamers are using.”
“It’s the largest infostealer malware campaign in gaming/cheating community history.”
In a separate post, PhantomOverlay claimed it has “a pretty good idea of where the malware is coming from but the malware gang is aware of suspicions on them [and] has made it increasingly hard to prove anything.”
Activision Blizzard had contacted the cheat-selling site and “will help us assist millions of infected users,” PhantomOverlay said.
An Activision Blizzard spokesperson told Cointelegraph it was aware of claims that credentials “across the broader industry could be compromised from malware from downloading or using unauthorized software.”
Related: Prisma Finance exploited in $10 million breach
It said its servers “remain secure and uncompromised” and recommended users change their password if they want to ensure their accounts are protected.
In its post, vx-underground wrote that PhantomOverlay was “alerted of fraudulent activity when user accounts began making unauthorized purchases.”
PhantomOverlay contacted the alleged victim, and since then, more have been identified, it said.



Responses