ParaSwap evades hack targeting Augustus v6 contract vulnerability
ParaSwap paused the v6 API soon after discovering the vulnerability and secured the potential victims’ funds through a white hat intervention. Plans to reimburse potential victims are underway.

Decentralized finance (DeFi) aggregator ParaSwap discovered a vulnerability in its newly launched Augustus v6 contract and prevented a colossal loss of funds through timely white hat intervention.
On March 18, the ParaSwap Augustus v6 contract went live, promising greater efficiency in swapping gas fees than all its preceding contracts. However, the contract contained a critical vulnerability, allowing hackers to drain funds when approved.
Soon after discovering the vulnerability on March 20, ParaSwap paused the v6 application programming interface (API) and secured the potential victims’ funds through a white hat hack.

ParaSwap advised all users to revoke permissions to the Augustus v6 contract to avoid further loss of funds until the vulnerability is neutralized.
Despite ParaSwap’s proactive effort to roll back the vulnerable v6 contract and inform users to take necessary steps, the hacker managed to cash out funds worth roughly $24,000 from four different addresses.
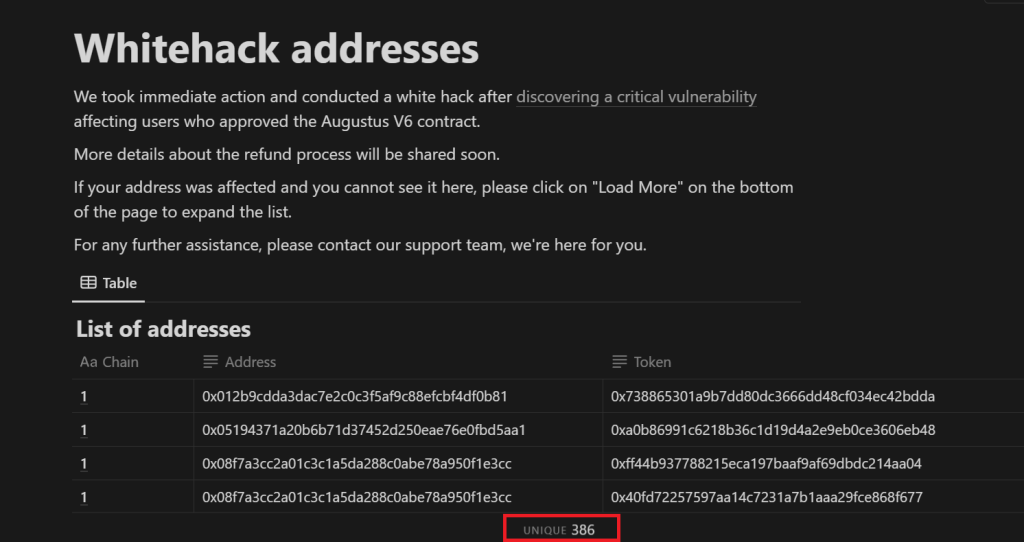
In total, ParaSwap revealed that 386 addresses were affected by the vulnerability. The protocol also asked users to report any loss of funds that may have gone unidentified during the preliminary investigation.

In addition, ParaSwap also deactivated the support for the vulnerable v6 contract on its recently updated user interface (UI) and reverted to using v5. “We have successfully recovered funds for all addresses, and more details about the refund process will be shared soon,” the company added.
ParaSwap did not immediately respond to Cointelegraph’s request for comment.
Affected users remain at risk as long as they haven’t revoked their approvals, and ParaSwap recommends individuals use exploit checker services like Revoke to confirm their safety. Check out Cointelegraph’s guide on how to identify and mitigate smart contract vulnerabilities.
Related: Old Trust Wallet iOS vulnerability from 2018 may still affect some accounts
Generative artificial intelligence (AI) tools like the ChatGPT-4 are good at generating code. However, the tools fail to perform as a fully reliable security auditor.
According to a recently published research paper from a pair of researchers from Salus Security, a blockchain security company with offices in North America, Europe and Asia:
“GPT-4 can be a useful tool in assisting with smart contract auditing, especially in code parsing and providing vulnerability hints. However, given its limitations in vulnerability detection, it cannot fully replace professional auditing tools and experienced auditors at this time.”
According to their findings, ChatGPT is good at detecting true positives — actual vulnerabilities that would be worth investigating outside of a testing environment. It reached greater than 80% precision in testing.

Responses