Proof-of-authority vs. proof-of-stake: Key differences explained

What is proof-of-authority (PoA)?
One of the most revolutionary technologies in recent years is blockchain. Blockchain, which first emerged as a decentralized public ledger for the Bitcoin (BTC) cryptocurrency, is now extensively used to promote corporate federation and integration.
Blockchain essentially consists of a linked data structure replicated through a peer-to-peer (P2P) network where new blocks are created by issuing new transactions. For example, peers use mechanisms like proof-of-work (PoW) or proof-of-stake (PoS) to reach distributed consensus on transactions operating on permissionless blockchains like the Ethereum blockchain.
Blockchains with permissions like the XRP ledger have emerged as a way to federate businesses and encourage responsible interactions. Numerous consensus methods have been put forth for these blockchains, each with a unique set of advantages and disadvantages.
For example, a novel family of Byzantine fault-tolerant (BFT) consensus algorithms called proof-of-authority (PoA) is widely utilized in practice to ensure superior performance to conventional practical Byzantine fault tolerance (pBFT). Gavin Wood, co-founder and former chief technology officer of Ethereum, presented PoA as a remedy for blockchains based on Ethereum in 2017.
The PoA consensus process grants a few blockchain players the authority to validate network transactions and update its broadly distributed registry. The algorithms function intuitively as rounds where a chosen party serves as the mining leader and is in charge of putting out new blocks on which distributed consensus is obtained.
The creation of online games that can be significantly expanded and yet get an authoritative consensus is one of the proof-of-authority use cases. The benefit for players is the low transaction cost provided by PoA-based systems.
One of the advantages of proof-of-authority over pBFT is that PoA performs better than practical Byzantine fault tolerance because it requires fewer message exchanges and less overhead. However, in a true synchronous network model like the internet, the actual effects of such performance enhancement are somewhat hazy, particularly regarding availability and consistency guarantees, which are among the limitations of proof-of-authority.
What is proof-of-stake (PoS)?
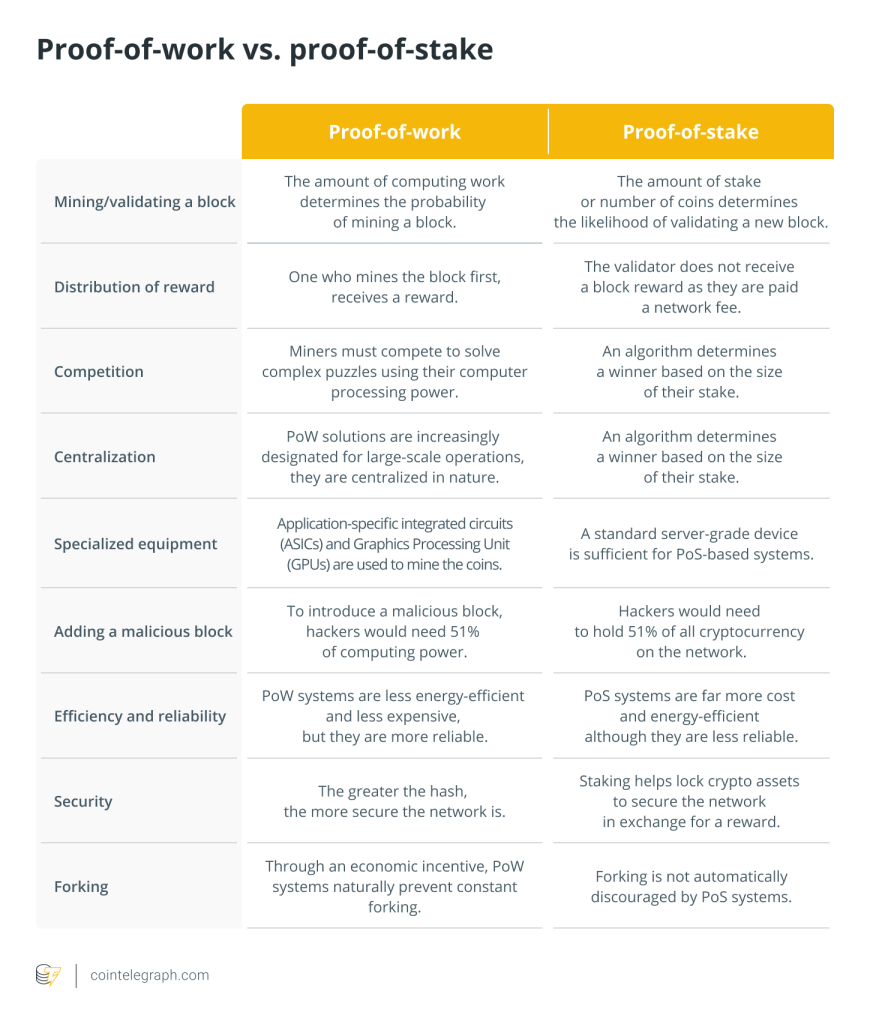
To replace PoW consensus mechanisms that use a lot of energy, proof-of-stake protocols were created. In the PoS consensus method, leaders are chosen based on their stakes or contributions to the blockchain network rather than processing power resources. The number of digital tokens a node holds or deposits constitutes its stake in the PoS consensus method.
Polkadot, Avalanche and Cardano are a few instances of contemporary market-dominating PoS blockchains. However, Ethereum, which was initially intended as a PoW network, is transitioning into a PoS blockchain. The consensus layer upgrade is the process through which Ethereum will update its consensus method.
How does proof-of-authority work?
The PoA consensus differs from the PoS consensus in that it uses identity rather than the digital assets each user owns. Identity here refers to the certainty that validators are who they say they are, as shown by the correspondence between their personal identity on the platform and any formal documents presented by them. Thus, a person’s reputation is more valuable than their possessions.
Validators are pre-approved by a group of “authorities” to verify transactions and build new blocks. To be trusted, validators must adhere to a set of requirements. Two of these demands are that they use the same identity on the platform to register in the public notary database and follow the rules to ensure that the network functions properly. Furthermore, the process for choosing authorities should adhere to accepted norms to guarantee that all applicants have an equal opportunity to get selected for the privileged position.
Finally, authorities (around 25 entities) must disclose their identity to act in their position, for which they get rewarded in return. However, using the PoA algorithm for a decentralized network is challenging as only a few users hold power. The PoA consensus is therefore considered a private network solution instead of a public blockchain solution.
How does proof-of-stake work?
Some blockchains employ a particular consensus technique called proof-of-stake to establish distributed consensus. By investing effort, miners in PoW demonstrate that they are putting money at risk; however, validators expressly stake money in the form of Ether (ETH) into an Ethereum smart contract when using PoS.
A user must execute three different pieces of software — an execution client, a consensus client and a validator — and put 32 ETH into the deposit contract to take part as a validator. However, it is possible to stake without having 32 ETH with staking pools. Users who deposit ether are added to an activation queue that controls the rate at which new validators can join the network.
Following activation, peers on the Ethereum network send new blocks to validators. The block’s delivered transactions are carried out again, and the validity is verified by examining the block’s signature. After that, the validator broadcasts a vote (known as an attestation) to support that block throughout the network. If the validator acts dishonestly or carelessly, the staked ether serves as collateral that can be lost. The validator is, therefore, in charge of producing and propagating new valid blocks (occasionally).
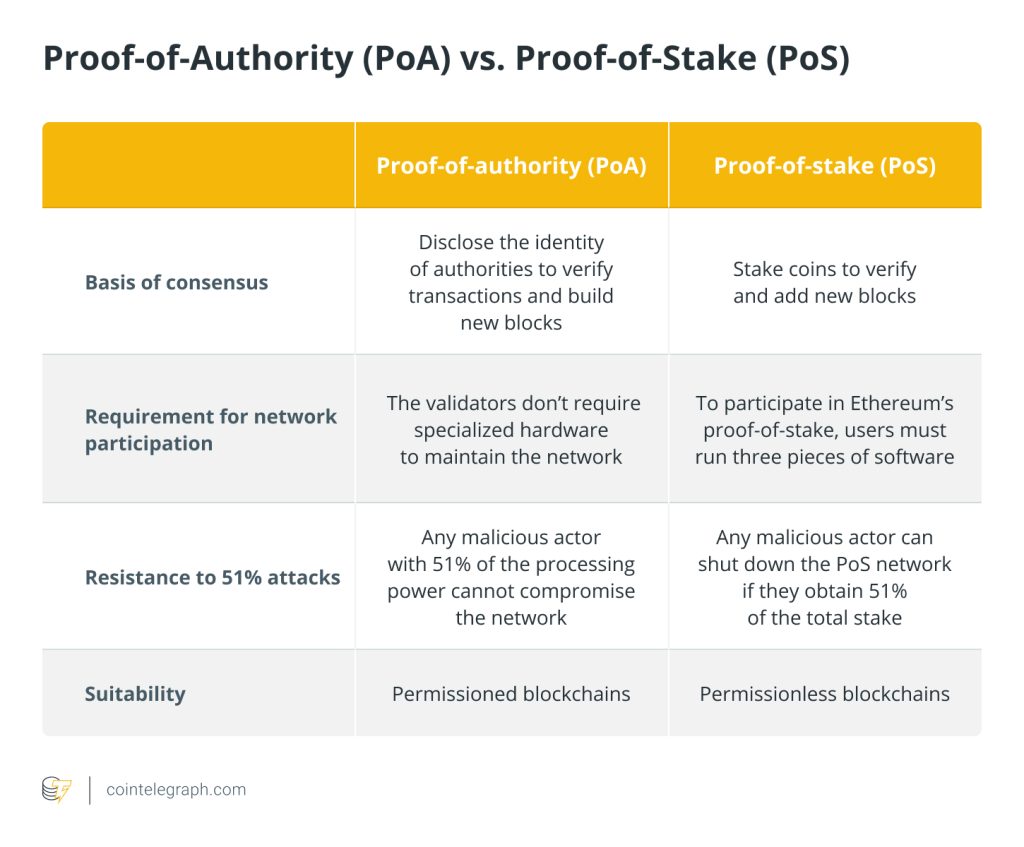
Proof-of-authority (PoA) vs. proof-of-stake (PoS)
PoA and PoS algorithms offer advantages and disadvantages similar to any consensus mechanism. Moreover, in the history of blockchain, no developer or platform has yet been able to put forth a consensus mechanism that is impervious to issues or objections.
The PoA algorithm reduces the power required to run the network and makes validation easier. On the other hand, staking in the PoS consensus mechanism facilitates decentralization by allowing individual participation in network security.
The PoA algorithm does not require puzzle-solving to guarantee the ongoing connection between nodes. Therefore, the validators don’t require specialized hardware to maintain the network. However, three different pieces of software, including an execution client, a consensus client and a validator, are required to participate in the Ethereum staking process.
The speed at which the authorities validate transactions is accelerated by the proof-of-authority algorithm. As a result, the blockchain records a higher transaction rate than PoS or PoW due to the predictable generation of blocks dependent on the number of validators.
Additionally, the PoA network is more resistant to attacks than the PoS or PoW consensus because a user who manages to create 51% of the processing power cannot compromise the network. However, an individual or group of hackers may attack or shut down the PoS network if they obtain enough coins (51% of the total stake). So, is proof-of-stake less secure? The answer is that to protect the network’s security, almost every blockchain uses some techniques that discourage hackers’ malicious actions.
For instance, to prevent 51% attacks, many PoS networks additionally employ slashing techniques, which is one of the problems with proof-of-stake. Slashing takes a portion of a validator’s stake to discourage actions that can endanger the network’s security. Nonetheless, slashing presents a problem in that it can occur even if the validator unintentionally does anything that is interpreted negatively. So, is PoA better than PoS?
While PoS has security flaws and PoW consumes a lot of energy, PoA is an ideal option in terms of security and energy usage. But, because PoA is a more centralized strategy for upholding consensus on a blockchain network, it targets businesses or private groups that aim to use permissioned networks.
The summary of the differences between PoA and PoS algorithms is listed in the table below:

The future of proof-of-authority and proof-of-stake
A modified version of proof-of-stake is proof-of-authority, in which a validator’s identification serves as the stake rather than a monetary one. Furthermore, due to the PoA consensus’s simplicity, it is imperative to guarantee validators’ independence and provide them with the tools necessary to safeguard their nodes. These problems can be resolved, though.
For example, the identity-at-stake PoA design establishes an incentive model in which a validator’s optimal course of action is to operate in the best interests of the network. Such a construct is an intriguing paradigm for blockchain consensus due to its cost-efficiency.
Similarly, the fact that proof-of-stake may be used for much more than just money is what makes it so intriguing. For instance, PoS algorithms can be utilized in decentralized anti-spam systems, development of decentralized applications (DApps), security and scalability of cryptocurrencies and potentially various other use cases that we haven’t even seen yet.
So, is proof-of-stake the secret to scaling cryptocurrencies, and is it changing how the money will be used in the future? Considering the rising demand for a cryptographic infrastructure that is scalable, secure and effective, the PoS consensus mechanism can be considered an ideal choice by the blockchain platforms.


… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Here you can find 66175 more Info to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Here you can find 82882 additional Information on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] There you can find 49864 additional Information to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Here you can find 96758 more Information on that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] There you will find 72386 additional Information to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] Find More on to that Topic: x.superex.com/academys/beginner/3401/ […]
… [Trackback]
[…] There you can find 24182 additional Information to that Topic: x.superex.com/academys/beginner/3401/ […]