What is MEV: A beginner’s guide to Ethereum’s invisible tax

What is miner extractable value (MEV) and how does it work?
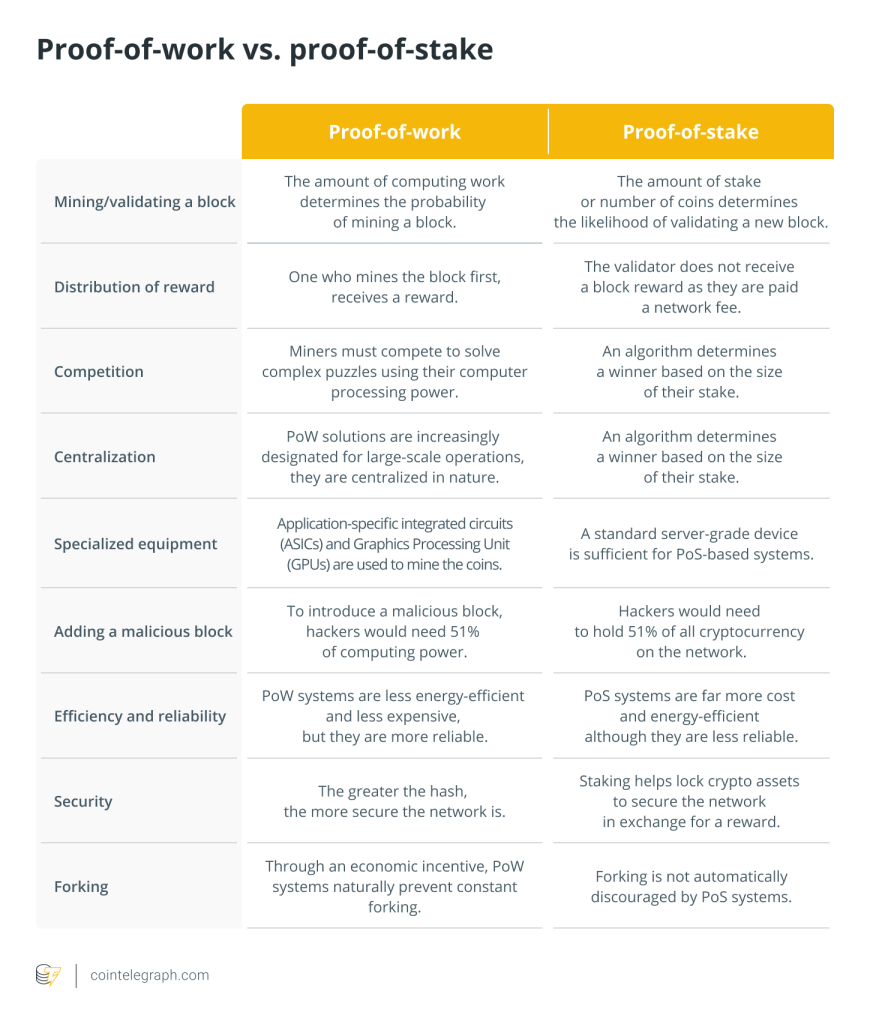
Mining is the foundation of blockchain-based proof-of-work (PoW) cryptocurrencies like Bitcoin (BTC), which pays the miner for discovering new blocks for transactions. As a result, crypto mining has become a source of living for miners. To cryptographically link a new block to the prior block in the blockchain, miners must solve a complex mathematical challenge that is computationally expensive.
The total processing power of all users will determine how difficult this puzzle is to solve. Depending on the difficulty, an individual will need strong machines to increase the likelihood of mining a block and earn incentives in return. As miners control the inclusion, exclusion and ordering of transactions, they can extract value in excess of the standard block rewards and gas fees.
The value that miners can obtain from changing the sequence of transactions inside the blocks they generate is known as the miner extractable value (MEV). Therefore, order fairness presents a problem for permissionless PoW cryptocurrencies. When the stakes are large enough, MEV can even reward blockchain forks, which may impact future transactions and the security of the consensus layer.
This article will explain the concept of miner extractable value, why MEC occurs, MEV strategies, the most common MEV attacks and the pros and cons of MEV.
How does MEV extraction take place?
To understand how MEV works and why MEV occurs, let’s take an example of an arbitrage transaction on decentralized exchanges (DEXs). Arbitrage across DEXs is built into their design, whereas in traditional markets, arbitrage opportunities are considered a sign of an inefficient market.
Automated market makers (AMMs), a class of decentralized exchanges, let users purchase and sell tokens without the involvement of a third party. The AMM, a piece of computer code running on a blockchain, is unaware of the token’s current market price and is dependent on arbitrageurs to return the token’s price to the market price. Therefore, arbitrageurs make sure that decentralized exchanges have fair prices.
The settlement mechanism of decentralized ledgers allows orders to be organized in batches and exposed before they are settled, allowing any agent (miner) to suggest a series of trades that are dependent on one another. This trustworthy commitment has given rise to flash loans, which allow anyone to start arbitrage trades. By trading ahead of profitable trading opportunities presented for settlement due to orders being disclosed, settlement agents (miners) can thwart the efforts of arbitrageurs who create these opportunities.
Additionally, these arbitrageurs risk being taken advantage of by other bots or miners if they use the standard transaction channel for their transactions. For example, Ethereum’s original architecture called for all pending transactions to be maintained in the mempool, open to the public and submitted to a peer-to-peer network for processing. By submitting the same trades with themselves listed as beneficiaries and a greater fee, knowledgeable users could evaluate the pending transactions and execute their deal ahead of the arbitrageur.

However, miners are best placed to front-run other participants in the network, as they ultimately decide which transactions are completed in the block and in what sequence. Additionally, they can quickly duplicate all winning deals from the mempool and execute their transactions ahead of arbitrageurs and anyone attempting to outperform them.
It’s common to refer to the value a miner could extract in this fashion as miner extractable value or MEV, or an invisible tax, that a miner can collect from users. Nonetheless, arbitrage is only regarded as MEV when another transaction is switched by a miner with their own to benefit from the opportunity.
Like front-running, miners can opt for back-running, which happens when a miner enters a sell order to sell into the purchasing pressure after noticing a significant buy. Alternatively, in a sandwich deal, miners place a sell order right after the transaction that affects the market price and a buy order right before it, i.e., the risk is controlled by having contemporaneous buy and sell orders.

Does MEV apply to Bitcoin mining?
Theoretically, MEV applies to Bitcoin as it is a crucial feature of the proof-of-work consensus mechanism. However, in reality, MEV has occasionally been seen on the Bitcoin blockchain, as almost all transactions are BTC transfers between two parties.
As a general rule, miners have more opportunities to generate MEV by taking advantage of the inefficiencies brought on by increased transaction complexity. That said, due to smart contract-based complex transactions, MEV opportunities were available on the Ethereum blockchain (before it switched to a proof-of-stake consensus mechanism).
After The Merge, validators are responsible for transaction ordering, inclusion, or exclusion; the value extraction method is now called maximal extractable value. According to the Ethereum Foundation, the success of MEV extraction can only be validated by validators in theory. However, in practice, searchers extract MEV’s large portion.
What is an MEV searcher?
Searchers are independent network participants that extract a large portion of MEV by running complex algorithms on blockchain data to identify lucrative MEV possibilities and set up bots to submit those profitable transactions to the network automatically. So, does this mean validators do not get MEV benefits from Ethereum invisible tax?
As searchers are ready to pay high gas prices to have their transactions included before those of other users, validators still receive a percentage of the MEV (in the form of gas fees, for instance). That said, if searchers submit the transaction with the highest gas price, they can be sure that their arbitrage transaction will run.
The most common MEV attacks
Other than DEX arbitrage, nonfungible token (NFT) MEV, liquidations, Uncle-Bandit and Time-Bandit attacks are common MEV examples.
NFT MEV
Searchers can use MEV extraction strategies in the NFT market. One well-known instance of NFT MEV was when a searcher shelled out $7 million to purchase every Cryptopunk at the price floor. Similarly, an NFT can be bought for a discount if it is inadvertently posted at a low price, allowing a searcher to outbid other buyers.
Liquidations
Liquidators are searchers who specialize in liquidating overcollateralized loans to extract MEV from lending protocols like Aave and Maker that use deposited collateral, such as Ether (ETH), to lend to other users. Users can borrow different assets and tokens from other users up to a certain amount of the collateral they deposited. In addition, the protocol permits anyone to sell the collateral and swiftly pay back the lenders if the value of the borrowed assets exceeds the collateral’s value due to market fluctuations.
In order to quickly decide which borrowers can be liquidated and to be the first to submit a liquidation transaction and earn the liquidation fee for themselves, searchers compete to liquidate the collateral as quickly as possible. The MEV opportunity arises because, if a loan is liquidated, the borrower is sometimes forced to pay a sizable liquidation charge, of which a portion goes to the liquidator (searcher).
Uncle-Bandit attacks
You might be asking yourself what “uncle” means here; let’s clarify. When two blocks are mined and broadcasted simultaneously with the same block number, uncle blocks are produced. The other block that is left after the canonical block receives greater validation from nodes and whose transactions do not change any state is referred to as an uncle or orphaned block.
Transactions inside the uncled block are public, offering MEV opportunities to searchers or attackers. For instance, when flashbots users (searchers) submit a sandwich trade (a bundle of transactions), they can apply an arbitrage after taking the sandwich’s buy portion. Moreover, miners running MEV-Geth enable users to bypass the public mempool and avoid front-running risk by submitting bundle transactions directly to validators.

The MEV-Geth is a gateway into the Ethereum network, which can operate as a full node, an archive node or a light node. The bundles of transactions frequently contain the searcher’s transactions in addition to pending transactions from other Ethereum users that were retrieved from the mempool. Validators are encouraged to include the bundle in their blocks because they receive 80–90% of the rewards earned by the searcher.
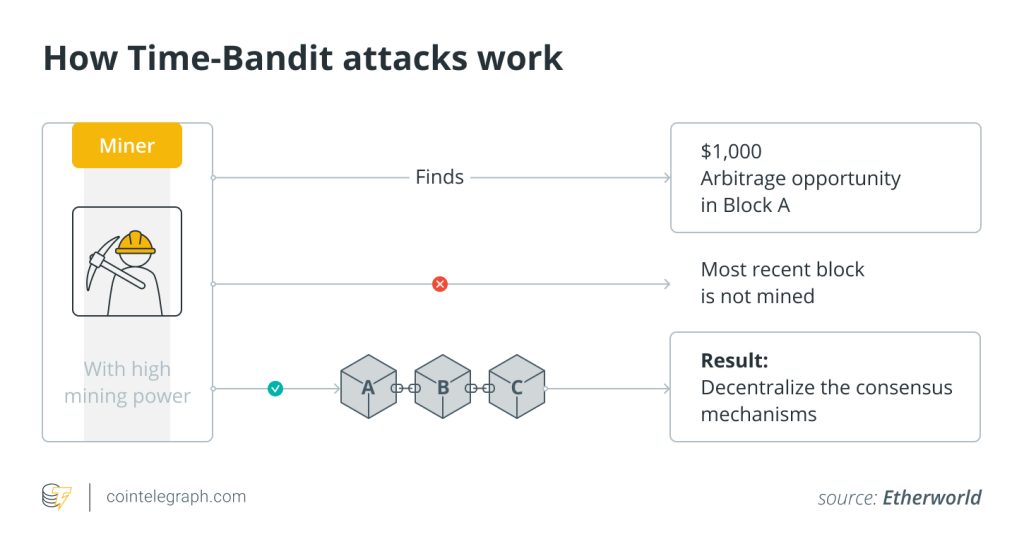
Time-Bandit attacks
Time-Bandit attacks aim to reverse transactions on the blockchain. For instance, if searchers discovered extremely profitable MEV opportunities in the previously validated blocks, they can propose to change the course of Ethereum’s history and remine/revalidate these blocks to capitalize on the chance they just discovered. To reverse transactions, they encourage the validator to carry out a Time-Bandit attack by offering a lucrative incentive.

As such attacks allow anyone to post a proposal to alter the blockchain'’ history, they function as a tool to auction off the consensus of the chain’s present state to the highest bidder, risking the integrity of the Ethereum network.
The good and bad of MEV
Like any other strategy, MEV also has positive and negative consequences. For instance, rational searchers help fix economic inefficiencies (such as speedy liquidations on lending protocols), ensuring the robustness of decentralized applications (DApps) and decentralized finance (DeFi) protocols.
On the other hand, front-running frequently causes network congestion and expensive gas fees for everyone else trying to conduct standard transactions, which is one of the downsides of MEV. Additionally, sandwiched users face increased slippage, the maximum deviation from the target price that a user is willing to accept in a deal.
Furthermore, as searchers offer lucrative incentives to validators for reorganizing blocks, it may lead to consensus instability, disregard of the immutability feature of blockchains and impact the honest validators and overall security of the blockchain network.
How can DeFi users protect themselves from the MEV issue?
All transactions can be settled in a single batch if DApp users sign transactions and submit the trade off-chain with order preferences. This practice renders the reorganization of transactions unimportant because all deals have the same price regardless of the order, increasing the difficulty of replication.
However, even if validators or miners (searchers) attempt to profit by figuring out the signed messages, it would be pointless because they would need to know which AMM pool those trades will be settled during off-chain execution, saving users from invisible tax.
Alternatively, Chainlink’s solution to the MEV problem is called fair sequencing services (FSS), a decentralized transaction ordering service that ensures fairness and predictability in the time-ranking of transactions for all users and can help to reduce MEV. In addition, the smart contract economy can scale with such a solution by leveraging layer-2 rollups like Arbitrum. If FSS (that uses decentralized oracle networks) is used to sort transactions and is applied to the same layer 2, it can minimize the consequences of MEV.


… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More here on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More on to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] There you will find 61646 additional Information to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More here on that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Find More Info here to that Topic: x.superex.com/academys/beginner/2559/ […]
… [Trackback]
[…] Here you can find 18075 additional Information to that Topic: x.superex.com/academys/beginner/2559/ […]