What is digital identity management, and why is it important?

In the context of cryptocurrencies, digital identity management refers to the safe handling and authentication of user identities within blockchain networks. Since cryptocurrencies are anonymous and decentralized, sustaining system confidence requires robust digital identity management.
In order for cryptocurrencies to be widely used and accepted in a variety of industries, it is crucial that accurate user verification be made possible. It also strengthens security procedures and creates a platform for trustworthy and transparent financial interactions.
Understanding digital identity management in crypto
In the cryptocurrency and blockchain world, digital identity management is essential for user protection, combating fraud and maintaining regulatory compliance. Understanding digital identity management is crucial in the rapidly evolving world of cryptocurrencies. A key component of blockchain transactions, digital identification is essential to maintaining secure and open trades in the cryptocurrency sphere.
Digital identities are essential for blockchain transactions because they allow for user authentication and activity verification. The rise of decentralized identification solutions, particularly self-sovereign identities (SSI) on blockchain systems, is a key development in this area. By giving people more control over their own digital identities than traditional systems do, SSI improves privacy and security. SSI also ensures a more democratic and user-centric approach to identity verification by getting rid of central authorities.
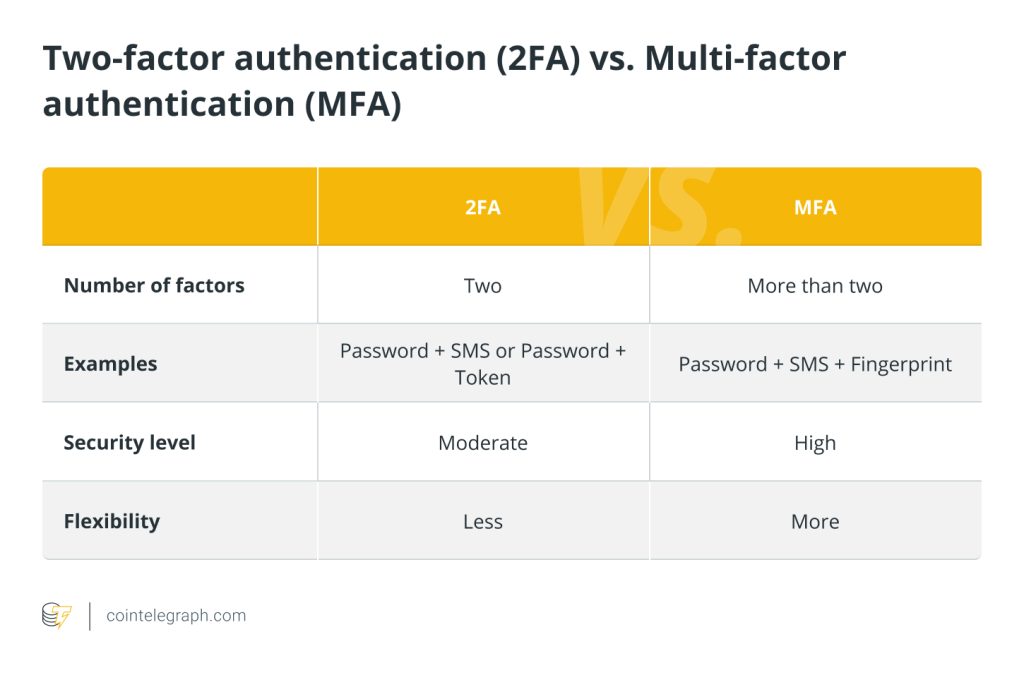
Additionally, Know Your Customer (KYC) identity verification procedures are included in digital wallets, crucial tools for managing cryptocurrency. Implemented in accordance with legislation, KYC procedures confirm users’ identities, reducing the risk of fraud and criminal activity. While these procedures are required for security, they also highlight the difficulty of striking a balance between privacy concerns and legislative needs in the crypto world.
Why is digital identity management important in crypto and blockchain?
Security is of the utmost importance in this decentralized digital environment, and digital identity management is the key to maintaining participant authenticity. By confirming users’ identities, this technique not only increases credibility and trust but also assures adherence to legal requirements, including KYC and AML checks, which are essential for financial transactions.
Due to the immutability of blockchain records, digital identity management also provides protection against fraud and identity theft. Additionally, it is crucial for the execution of smart contracts, where identity confirmation is necessary.
Moreover, digital identity management promotes the idea of decentralized identification and makes it easier to tokenize real-world assets, giving people increased privacy-preserving authority over their own identities. Digital identity management forms the cornerstone upon which the inventive and secure capabilities of cryptocurrencies and blockchain technology are realized, mitigating fraud, enabling seamless international transactions, and safeguarding data privacy.
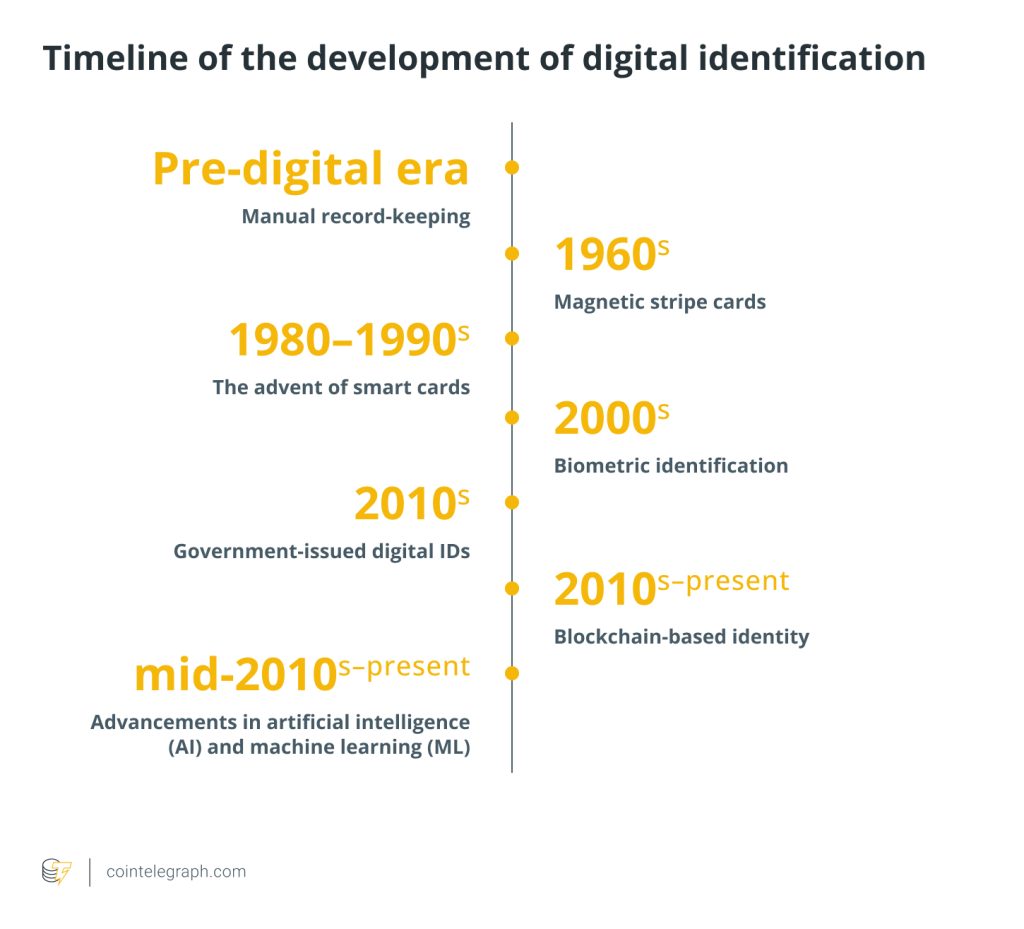
Evolution of digital identification
Over the years, the development of digital identification has experienced major changes, moving from conventional paper-based systems to complex, technologically advanced procedures. Here is a timeline outlining the significant phases in the development of digital identification:

Manual record-keeping (pre-digital era)
Prior to the advent of computers, identifying records were typically manually maintained using paper-based documents, such as birth certificates, driver’s licenses and passports. These documents were vulnerable to loss, theft and forgery.
Magnetic stripe cards (1960s)
Credit cards, debit cards and access control cards were all made possible by the encoding of personal information on cards made possible by magnetic stripe technology. Although magnetic stripe cards were securer than paper-based systems, they were nevertheless susceptible to skimming and copying.
The advent of smart cards (1980s–1990s)
Personal data could be stored more securely thanks to smart cards’ safe components and microprocessors. They found use in a number of industries, including government, healthcare and finance. Smart cards greatly improved security, yet they were still vulnerable to some assaults.
Biometric identification (2000s)
In the 2000s, biometric identification techniques such as fingerprint, iris and facial recognition gained popularity. Biometrics provided a high level of security and were frequently utilized in mobile devices, border control and access control systems. However, issues with privacy and the retention of biometric information surfaced.
Government-issued digital IDs (2010s)
Several nations started issuing digital IDs that were connected to their residents’ biometric information. For secure online authentication and digital signatures, these digital IDs frequently incorporated a chip or other feature that kept personal information. Mobile-based digital IDs that use smartphones for secure identification also gained popularity.
Blockchain-based identity (2010s–present)
Decentralized identity management systems are made possible by blockchain technology. Self-sovereign identities can be created because of the blockchain’s immutability and capability for securely storing encrypted data. Furthermore, storing identity information on a blockchain enables individuals to authenticate their data, reducing reliance on centralized identity providers.
Advancements in artificial intelligence (AI) and machine learning (ML) (mid-2010s–present)
AI and ML technologies have improved identity verification procedures. Automated algorithms may now evaluate enormous volumes of data, including face traits, behavioral patterns and historical records, to precisely and quickly authenticate identities.
Integration of mobile devices and biometrics (present and future)
Mobile devices have taken a prominent role in digital identity in both the present and the future. Biometric authentication techniques, such as facial recognition and fingerprint scanning, are widely available on smartphones and make secure identification more convenient for consumers. Mobile device biometric integration is still developing, ensuring a seamless and safe user experience.
How can an identity be verified via blockchain?
Creating a digital representation of a person’s identity and securely preserving it on the blockchain involves typical steps in the blockchain identity verification process. Let’s understand the identity verification process using an example of identity verification by a cryptocurrency exchange utilizing blockchain.
User registration
Users who sign up on a cryptocurrency exchange platform must provide personal data and supporting documentation to undergo KYC verification. Name, address, government-issued ID and a selfie for facial recognition are all included in this data.
Documentation verification
The trading platform’s verification system examines the given documents’ legitimacy. The user’s information is prepared for blockchain verification once it has been validated.
Creation of digital identity
A distinct digital identity is generated when the confirmed user’s information has been encrypted. This digital identity includes hashed copies of the user’s identification documents and biometric information (such as face recognition).
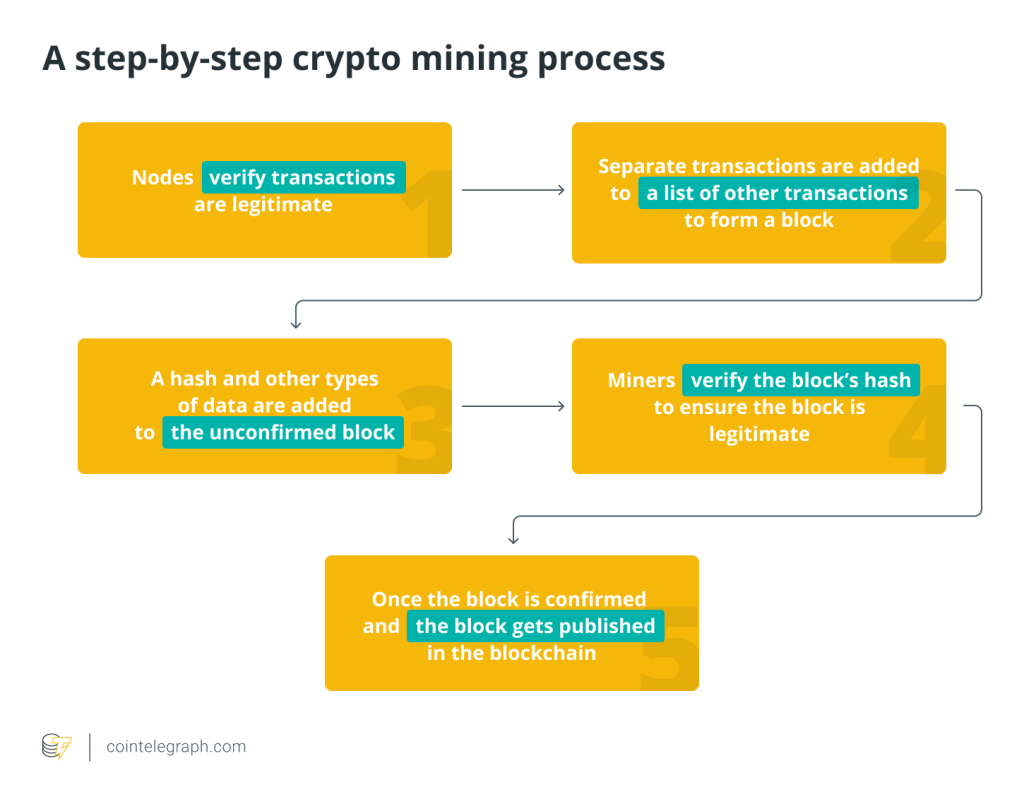
Adding data to the blockchain
The digital identification data is contained in a transaction that is created. The blockchain is then updated with this transaction by adding it to a block. To protect security and privacy, the data is hashed and encrypted before being kept.
Confirmation and consensus
Using consensus techniques (such as proof-of-work or proof-of-stake), the network’s nodes verify and confirm the transaction containing the digital identification information. The transaction is recorded on the blockchain once a consensus has been established.
Identity-checking procedure
The crypto trading platform demands identification verification each time a user tries to access a sensitive account function or makes a transaction. After the user enters their digital identity, it is hashed and compared to the hash that is recorded on the blockchain.
Access control with smart contracts (optional)
Smart contracts can be used for access control to automate the verification process. For instance, a smart contract could specify the terms and circumstances under which a user is permitted to utilize particular services. In the event that the user’s digital identity and the data stored on the blockchain match, the contract would automatically execute and allow access.
Selective disclosure for transactions
By using selective disclosure during a crypto transaction, the user can give only the information required to complete the transaction while protecting their full identity. This enhances privacy while confirming the legitimacy of the transaction.
Immutable record
The user’s identity becomes an immutable record once it has been confirmed and stored on the blockchain. As a result, there is no way to change the data, making this a secure and trustworthy method of verification.
The potential challenges associated with blockchain-based identity verification
Implementing blockchain technology for digital identity verification offers solutions for security and efficiency, but it also has its share of difficulties. The immutability of blockchain data raises questions about permanently recorded information and the possibility of linking it to real-world identities, which is a major privacy concern for users.
Another challenge is scalability, which is particularly problematic for public blockchain networks because they have trouble processing a large number of transactions quickly. The development of a global digital identification standard is further hampered by interoperability issues across different blockchain platforms and with current identity infrastructures.
Regulatory compliance is a crucial factor because different jurisdictions have different regulatory standards, such as the stringent General Data Protection Regulation in the European Union. Additionally, there is a major risk of losing access to digital identities owing to missing private keys, which makes user-friendly recovery techniques necessary.
The user experience is still difficult since non-technical consumers may be put off by complicated encryption procedures. Adoption is made more difficult by security concerns at the application layer and the high expense of creating and implementing blockchain-based identity systems.
Therefore, it is necessary to undermine ingrained trust in conventional systems and build legal frameworks that include obligations and rights in case of conflict if one wants to persuade stakeholders to accept these technologies. To fully utilize the capabilities of blockchain-based digital identity verification systems, research, collaboration and user-focused design initiatives must continue despite these obstacles.



… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More Info here on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Here you can find 96386 more Info to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More on on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Here you can find 85710 more Information to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More on to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Find More Info here to that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/2232/ […]
… [Trackback]
[…] There you will find 65411 more Info on that Topic: x.superex.com/academys/beginner/2232/ […]