The Wallet Segment- a Shining Star in the Crypto Winter -The Status Quo, Challenges and Opportunities

1. Wallet
A cryptocurrency wallet is often referred to as a crypto wallet or digital wallet. In the Web3 world, a wallet does not only serve the role as managing assets by literal meaning, but also it is the necessary tool to participate in the Web3 world. Academically, a wallet takes custody of private keys, which can be deemed as the username and password of an account.
1.1 Public and Private Keys
In the concept of wallet, private keys, public keys and their respective mechanism are the underlying base. The following diagram reflects the relationship between random numbers, public and private keys, addresses, mnemonic phrase and KeyStore. It is briefly clarified as follows.

Figure 1. Diagram of Public & Private Key, Address, Mnemonic Phrase, KeyStore Relationship (Source: Huobi Research)
- Random number: A random number is to select a number randomly within a computer with 64 to the 16th power possibilities, a number approximately equal to the number of all atoms in the universe;
- Private key: a private key is generated by processing a random number, and a public key is asymmetrically encrypted (elliptic algorithm) based on it.
- (a) Private keys and mnemonics: a converted mnemonic phrase to assist with memorizing the key.
- (b)Private Key and KeyStore: KeyStore is a file format (JSON) for storing private keys. KeyStore is used to keep private keys in a convenient way without compromising security.
- Public key and address: a public key is derived from private key unilaterally. After hashing and format conversion by coding, a commonly seen address starting with "0x" is generated.
Compared to real wallet and account, public key is the address of the wallet, which can be understood as a bank account. Private key can be understood as "debit card number + CVV", and the mnemonic phrase serves the same function. Therefore, the relationship can be expressed as "KeyStore + password = private key = debit card number + CVV".
The above is an introduction to public and private key taking Ethereum as an example. Although the format and standard of non-Evm-compatible L1 chains are different, the underlying mechanisms and the process are the same.
1.2 Types of Wallets
The most critical thing about wallet is to distinct public and private keys. There are many ways to classify wallets, by generally accepted classification, it is summarized as the following:
- Criterion 1: According to whether the user holds the private key or not, it can be divided into decentralized wallet and centralized wallet. Users of decentralized wallets hold their own private keys, such as MetaMask, TokenPocket, imToken, etc.; while centralized wallets are also known as escrow wallets, i.e., the private key is in the custody of a third-party centralized organization, such as Binance, Huobi and other trading platforms.
- Criterion 2: Depending on whether the wallet private key is connected with the Internet, it can be divided into cold and hot wallets. The concept of cold wallets in a broad sense includes "paper wallets" that contain mnemonics, offline mobile phones, hardware wallets, etc. Hot wallets, on the other hand, are wallets whose private keys are connected to the Internet when signing for transactions, including wallets as APP, plug-in wallet on browsers, etc.
2. The Status Quo of the Wallet Segment
2.1 Overview
In terms of the number of users, total number of crypto users are around 300 million. According to data from statistica.com as of November 2022, total wallet users worldwide are approximately 85 million, an increase of about 6.3% from 80M at the end of 2021, and a decrease in the growth rate compared to that of the previous year. With expectation of next cycle to come after the end of current round of bear market, now is the dark before dawn.

Figure 2. The number of wallet users from 2011.11 to 2022.11 (Source: statista.com)
In terms of revenue size, according to a study by future market insight, total revenue of the global crypto wallet market in 2022 is about $1.398 billion, and it is expected to exceed $3.371 billion in the next decade, with a compound annual growth rate of 9.2%, which demonstrates a high growth trend. The winners will still be winners, dominating the market by 35% of market share.

Table 1. crypto wallet revenue and growth (Source: future market insight & Huobi Research own research)
In terms of regional distribution, North America was an early player and still dominates with a market share of over 30.0% in revenue last year. There are several key players in the North America region, including Coinbase Global, Inc. and BitGo and BitPay among others. In June 2022, PayPal Holdings, Inc. announced that all eligible PayPal account holders in the U.S. can send and receive cryptocurrencies on PayPal, which has also accelerated the growth of wallet users to some extent. The second fastest growing regional market is Asia Pacific, particularly Mainland China and Hong Kong. The Asia Pacific region will play a crucial role in blockchain innovation. The region has large population with high financial awareness and technical enthusiasts, driving innovation in crypto wallets in the region.
2.2 Business model
Current business models of crypto wallets are evolving along with the industry development. In early days, most wallets (hot wallet) mainly served as private key storage and management tool, i.e., it was to store money. Until various on-chain apps came out in 2020, the main business model is by collecting transaction fees, and this revenue stream is relatively weak.
As Defi and cross-chain demand soared, crypto wallets have continued to launch various on-chain services such as built-in cross-chain, staking, flash pay, etc. Some have launched financial products, such as mining, wealth management and subscription of relevant information. Some companies embedded exchanges as a built-in function in the form of H5 in an attempt to start exchange services with the wallet as the portal.
After a study on most wallets offered on current market, ranging from average hot wallets, custodial wallets to hardware wallets, the revenue streams and business models are summarized as the following:

Table 2. crypto wallet profitability model (source: Twitter & HuobiResearch Self Study)
2.3 Leading Projects
From the publicly available information, the leading wallets are mostly big companies, either as internal product or as equity investment. Table 3 illustrates the participation method of big companies in wallets: one type is as direct development of big companies, such as MetaMask, Coinbase Wallet, wallet from Facebook; and the other type is as investment received from big companies, such as Trust Wallet with Binance’s investment, C98, etc.


Table 3. crypto wallet profitability model (source: Twitter & HuobiResearch Self Study)
Overall, Meatmask, a giant entry wallet, has the highest revenue (at $200M), with the second tier being wallets owned by Coinan, and the particular highlight being the Coin98 wallet, which focuses on aggregated transactions and DEFI and has a market cap of $2.1B. Among the fast-growing wallets, imToken and TokenPocket are the most well known, and in the Chinese community topping the list.
3. Challenges
In current market cycle (2020-present), the overall development of the wallet segment has been on the fast track that numerous innovations that have added momentum, such as DeFi Summer in 2020 and the blossom of L1 chains in 2021. However, user-friendliness, security, privacy and regulation have always been the challenges on the path.
3.1 User-friendliness
Wallets are more intricate than centralized treasury platforms: as long as exchanges or centralized WM platforms provide convenient services, users do not need to understand the whole logic, while wallets require every step of interaction to be completed by users themselves, which mandates some basic understandings of blockchain. Once any problem is encountered by users on authentication or interaction, there will be no customer service team from the wallet team, which hinders new users that do not have certain level of technical background from entering the Web3 world
Most wallet brands have poor interaction with users, and there are plenty of room for development, such as more user-friendly interactive anti-phishing (security) alerts can be inserted on the plug-in side and mobile side, more convenient settings and user-friendly NFT\Token integration tools can be added, and more widely applicable Dapp environment adaptations can be designed (Table 4). In addition to the interactive experience, the function/login /UI of wallet is different from that of the Web2 applications. Many new and existing users end up choosing traditional centralized wallets again due to the drawbacks mentioned above. While centralized wallets may be vulnerable to human manipulations, they are simple to use and the interface is user-friendly; if decentralized wallets were to desire more users, user-friendliness must be addressed.

Table 4. Challenges of wallets on user-friendliness (Source: Huobi Research)
3.2 Privacy and regulation
Discussions on privacy and compliance are inevitable in Web3, data privacy and compliance issue remain concerned by wallets. Recently, unauthorized privacy collection of MetaMask has eventually brought the privacy issue on the table. According to the updated privacy disclaimer of Alchemy in October, IP addresses, user settings, MAC addresses, cookie identifiers, mobile carrier, browser or device information, location information, internet service providers may be automatically collected or to obtain such personal information by third-party. On November 23, ConsenSys (the parent company of MetaMask and Infura) updated privacy policy and state that when Infura is used as the default RPC in MetaMask, the corresponding IP address and ETH address will be collected when the user initiates a transaction (Figure 3); it lighted the bomb for more aggressive discussions on privacy invasion.

Figure 3. Screenshot of updated privacy policy of ConsenSys (source: https://consensys.net/)
The subject matter has sparked another discussion on decentralization, after all, one of the best features of the Web3 narrative is that users can take full control of their own data, disrupting the landscape that most platforms are in possession of user data. MetaMask, as the most popular wallet at the moment, violated the grain of most Web3 users. However, decentralization of data inevitably leads to a lack of regulation, making it difficult for any third parties and law enforcement agencies to step in when disputes or theft of assets are encountered.
Wallets are essentially the largest traffic portal in the Web3 ecosystem, but with current unstable business model, wallets are confronted with the intractable issues with compliance that wallet service providers, which offer exchange of digital assets, lending or borrowing, and hardware wallets should comply with the policies and regulations of the country where the services are provided.
3.3 Security
Wallets typically have a high level of security that no third-party is necessary, and wallet users have complete control over their assets in the wallet. Compared to centralized wallets, users of decentralized wallets are worry-free on misappropriation or abuse of authentication on assets by banks or exchanges. Furthermore, decentralized wallets are less dependent on centralized institutions, which is less likely to be subject to single point of failure or attacks. However, most current wallet users are responsible for managing their private keys and assets themselves, and it is more vulnerable to threats such as social engineering attacks and virus (Table 5).
Common categories of asset theft Main causes

Table 5. Common asset theft security issues (Source: Huobi Research)
The biggest security challenges for users remain the custody of private keys and anti-social-engineering-attacks. The lack of knowledge and awareness on security, as well as careless operating habits, can create excellent opportunities for hackers. For wallet developers, the underlying security of the wallet is also challenging. In addition to the open-source wallet code, developers must conduct thorough auditing on the security of the codes for each major update and the storage and management of the private keys.
4. Outlook
The Dapp ecosystem of wallets has grown significantly in the current market cycle (2020-present), and as a traffic portal for Web3, wallets have become a must-have for new users to enter the crypto world being one of the most critical blockchain infrastructures. The current influx of startups in the wallet segment compete in multiple ways, such as EOA wallets, smart contract wallets & MPC multi-sig wallets, etc. With a forward looking, the significance of wallet as portal will likely surpass all trading platforms and become the traffic hub for Web3, and a rapid growth may be first spotted in identity portal, payment portal, non-self-custodial wallets and multi-chain wallets.
4.1 As Identification to Enter Web3
Web3 is a decentralized version of the current Web2 Internet powered by blockchain and cryptographic technology. Not only does Web3 ensure the fairness of users in accessing the Internet, but users will be also able to control over their own data, as well as host their own websites and applications; transactions can be initiated at free will by crypto applications without the administrative privileges of a centralized company, bypassing the centralized power of Web2. The decentralized nature of Web3 offers a variety of advantages and endless possibilities. According to the GrandView report, the global Web 3.0 blockchain market size is expected to reach $33.53 billion by 2030, a compound growth rate of 44.9% from 2022 to 2030.

Figure 4. Web3 Login Method (Source: Huobi Research)
Web3 does not require a variety of different logins compared to Web2, and the decentralized wallets are compatible with all Web3 application ecosystems, which endows wallet with the most dominant status as Web3 traffic portal. According to MetaMask in July 2022 during the 6th anniversary retrospective that current total number of Metamask users exceeded 80 million, with more than 30 million are monthly active. Other wallets that disclosed user acquisition data, such as Trust and TokenPocket, have acquired users over 10 million, which is undoubtedly the most dominant traffic entrance in the crypto world, covering almost all mainstream cryptocurrency users. Wallet is expected to achieve the functions of off-chain KYC, on-chain user profiling, on-chain credit evaluation with the enormous user base, eventually realizing on-chain regulations and compliance.
Future crypto wallets will not only serve as identification portals in accessing any digital assets or virtual assets in Metaverse (land, real estate, game props, and many other NFTs), but also enhancing the ability engaging in projects that are suitable to on-chain indemnifications.
4.2 As Portal for Payments
Currently, retail cryptocurrency payments are still in the very early stage due to incomplete global regulatory environment and low awareness of cryptocurrency among merchants, etc. However, as cryptocurrency gradually becomes popular and the regulatory environment is upgrading, project developers and users of cryptocurrency payments skyrocket. Wallets, as portals for Web3, can integrate all crypto projects of payments, forming a new generation of Web3 payment ecosystem. All relevant offline and online operations can be carried out through the wallet, including shopping, ordering food, taking a cab, traveling and other P2P payments.
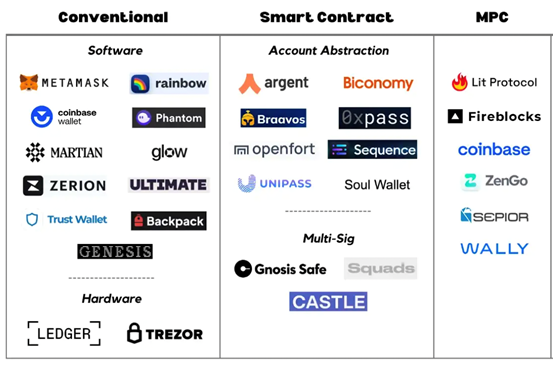
4.3 Non-self-custodial Wallets
Non-self-custodial wallets are those custodial wallets without mnemonics, which include two main types of wallets, MPC wallets and smart contract wallets. MPC (Multi-Party Computation) wallets are multi-sig wallets enhanced by authentication of performing multi-party computation on private keys off-chain. Smart contract wallets are based on smart contracts rather than EOA. Compared to traditional wallets that require users to keep their private keys (Figure 4), non-self-custodial wallets do not involve traditional private key generation and storage, effectively lowering the threshold for Web2 users to enter Web3.

Figure 5. classification of wallets (source: https://medium.com/1kxnetwork/wallets-91c7c3457578)
For novice Web3 users, the login experience may be somewhat unfavorable, even difficult to get started. Traditional EOA wallets require a series of complex and tedious processes, such as wallet generation, private key management, and saving mnemonics before secured login. The next generation of non-self-custodial wallets without mnemonics is reducing the barrier of entry for Web2 users by simplifying the login process and complexity. In the foreseeable future, non-self-custodial wallets have the potential to be the next growth point by introducing Web2 users to enter Web3.
4.4 Multi-chain Wallets
Current competitive landscape of multi-chain has been in shape, and each L1 chain has created its own wallet for the sake of the ecological development, but it is still incompetent to meet current demand of multi-chain and cross-chain. Furthermore, the management of private keys on multi-chain will be problematic with chaos; only one identity is necessary to create a multi-chain wallet with the absence of other tools managing private keys, so that one identity is sufficient to manage assets on different chains. At the same time, users are able to cross chains and redeem assets on multiple chains with utilization of the wallet ecosystem.
As mentioned earlier, multi-chain wallets already covered most mobile and desktop wallets as well as hardware wallets. Plug-in wallets are currently slower in growth, mainly on EVM-compatible multi-chain wallets, Polkadot's Polkadot.js cross-chain wallet and Cosmos’s multi-chain wallet. The competition for multi-chain wallets is expected to become more intense in the future as the demand for interoperability increases among multiple chains and multiple smart contracts.
About Huobi Research Institute
Huobi Blockchain Application Research Institute (referred to as "Huobi Research Institute") was established in April 2016. Since March 2018, it has been committed to comprehensively expanding the research and exploration of various fields of blockchain. As the research object, the research goal is to accelerate the research and development of blockchain technology, promote the application of the blockchain industry, and promote the ecological optimization of the blockchain industry. The main research content includes industry trends, technology paths, application innovations in the blockchain field, Model exploration, etc. Based on the principles of public welfare, rigor and innovation, Huobi Research Institute will carry out extensive and in-depth cooperation with governments, enterprises, universities and other institutions through various forms to build a research platform covering the complete industrial chain of the blockchain. Industry professionals provide a solid theoretical basis and trend judgments to promote the healthy and sustainable development of the entire blockchain industry.
Contact us:
Website: http://research.huobi.com
Email: [email protected]
Twitter https://twitter.com/Huobi_Research
Telegram: https://t.me/HuobiResearchOfficial
Medium: https://medium.com/huobi-research
Disclaimer
1. The author of this report and his organization do not have any relationship that affects the objectivity, independence, and fairness of the report with other third parties involved in this report.
2. The information and data cited in this report are from compliance channels. The Sources of the information and data are considered reliable by the author, and necessary verifications have been made for their authenticity, accuracy and completeness, but the author makes no guarantee for their authenticity, accuracy or completeness.
3. The content of the report is for reference only, and the facts and opinions in the report do not constitute business, investment and other related recommendations. The author does not assume any responsibility for the losses caused by the use of the contents of this report, unless clearly stipulated by laws and regulations. Readers should not only make business and investment decisions based on this report, nor should they lose their ability to make independent judgments based on this report.
4. The information, opinions and inferences contained in this report only reflect the judgments of the researchers on the date of finalizing this report. In the future, based on industry changes and data and information updates, there is the possibility of updates of opinions and judgments.
5. The copyright of this report is only owned by Huobi Blockchain Research Institute. If you need to quote the content of this report, please indicate the Source. If you need a large amount of references, please inform in advance (see "About Huobi Blockchain Research Institute" for contact information) and use it within the allowed scope. Under no circumstances shall this report be quoted, deleted or modified contrary to the original intent.




… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More Information here on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More here to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Read More Info here on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Info on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Here you will find 37559 more Information on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] There you will find 39723 additional Info on that Topic: x.superex.com/academys/deeplearning/2046/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/deeplearning/2046/ […]