How to recover a crypto wallet with or without a seed phrase

Cryptocurrencies offer individuals control over their assets and access to a diverse global market. However, navigating the crypto sphere can be daunting, especially when securing cryptocurrencies, nonfungible tokens ( NFTs) and other forms of digital assets. This article aims to demystify the crucial components of crypto wallets and seed phrases, highlighting recovery options and alternative solutions like Zengo and Solana Saga Mobile.
What is a crypto wallet?
A physical wallet is where users store their cash and cards. Similarly, a crypto wallet serves as a digital vault for cryptocurrencies, NFTs and other tokenized assets.
Unlike traditional wallets, however, a crypto wallet doesn’t store actual crypto assets. Instead, it holds the private keys, which act like passwords, granting users access to their funds on the blockchain.
The importance of crypto wallet seed phrases
A seed phrase, or a recovery phrase, is a sequence of 12 or 24 randomly generated words. This phrase serves as the master key to a crypto wallet, allowing users to restore access if they lose their device or forget their password.
When generated by a user’s wallet software, these words are based on a standardized algorithm (BIP-39) and are unique to their wallet. They are designed to be easy for humans to write down and remember while being extremely difficult for others to guess or recreate.
With great power comes great responsibility. As the sole gateway to users’ crypto assets, securing their seed phrase is paramount. Users should not share their seed phrase with anyone. This includes family, friends and even customer support representatives. The seed phrase is like a bank PIN; revealing it to anyone risks user funds.
Additionally, users should store seed phrases offline. Storing it electronically, such as on a computer or phone, makes them vulnerable to hacking. On the contrary, users should keep it in a fireproof safe, a secure location like a safety deposit box, or use specialized metal sheets designed to withstand damage to ensure protection against physical threats like fire, water or wear and tear. Moreover, holding multiple backups of a seed phrase is critical. This ensures users can access their funds even if one backup is lost or damaged.

Recovering a crypto wallet with or without a seed phrase
Loss of access to a crypto wallet can be a stressful experience. Fortunately, recovery is relatively straightforward if users have their seed phrase stored somewhere safe.
Recovering a wallet with a seed phrase
To recover a wallet with a seed phrase, follow the steps below:
- Download the appropriate wallet app. Make sure to download the official wallet app from the developer’s website. Do not download apps from third-party sources.
- Select “Recover wallet” or “Import wallet.” The exact wording will vary depending on the app.
- Enter the seed phrase. Be careful to type the words exactly as they appear, including the correct order and capitalization.
- Create a new password. This password will be used to access the wallet on this device.
- Confirm the password.
- The wallet will be restored. Users may need to wait a few minutes for the wallet to synchronize with the blockchain.
Recovering a wallet without a seed phrase
Unfortunately, recovering a crypto wallet without the seed phrase is generally impossible. The seed phrase is the only way to access the private keys that control crypto assets.
Here are some options users can try if they do not have their seed phrase:
- Contact the wallet provider. Some wallet providers may be able to help users recover their wallets if they can provide them with enough information, such as email addresses or phone numbers.
- Hire a data recovery specialist. This is a last resort option, and it is not guaranteed to be successful. Data recovery may work if the seed phrase was stored in a file and the file was subsequently deleted. Data recovery tools help retrieve deleted files, including the seed phrase.
Alternatives to traditional seed phrases for wallet recovery
As the Web3 space looks to onboard its first billion users, intuitive wallet experiences are critical. Seed phrases are a hindrance to that experience. Here are a few options that could enhance the crypto wallet experience without compromising security.
Hardware security modules
Hardware security modules (HSMs) are dedicated hardware devices designed to protect cryptographic keys. HSMs perform essential cryptographic operations like encryption, decryption, digital signing and authentication. These operations occur within the HSM’s secure environment, ensuring their integrity and authenticity.
However, HSMs can be expensive devices and would need some level of technical prowess. Therefore, mainstream adoption can be difficult.

Multisignature wallets
Multisig wallets, or multisignature wallets, are a type of crypto wallet that requires multiple private keys to authorize transactions. This differs from traditional single-signature wallets, where only one key is needed. By requiring multiple signatures, multisig wallets offer additional security and control over crypto assets.
Multisig wallets can be complex to manage and coordinate transactions due to relying on several parties to approve them. However, in a multisig wallet with five participants needing at least three approvals to perform a transaction, one participant losing their private key wouldn’t mean loss of access to assets in the multisig wallet.

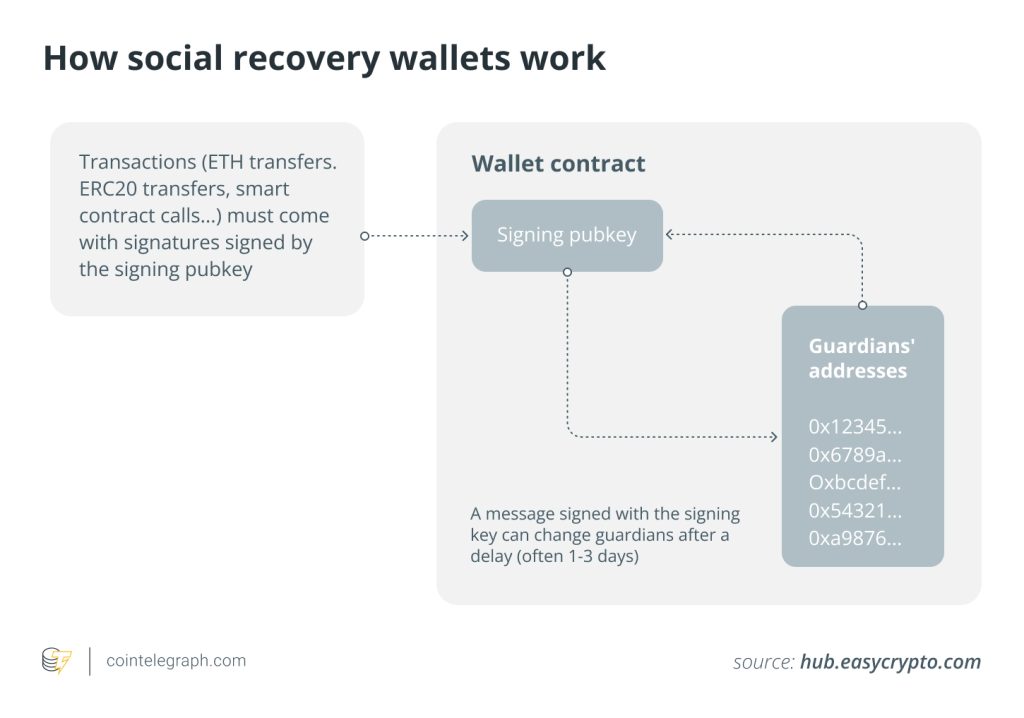
Social recovery systems
Social recovery systems offer a unique approach to regaining access to crypto wallets in case of lost, stolen or forgotten private keys. Unlike traditional methods like seed phrases or hardware wallets, it relies on a network of trusted contacts to assist with recovery.
During wallet setup, users choose a group of trusted individuals known as guardians. Each guardian receives a unique “recovery fragment” or information needed for wallet access; users who lose access to their private key request their fragments from the guardians. Once enough fragments are collected (as defined by the user-chosen “threshold”), they can be combined to reconstruct the private key and regain access to the wallet.
As guardians will have insights into the user’s crypto holdings, this approach has a privacy concern. There is also a risk that multiple guardians could conspire to take control of the user’s wallet.

Biometric authentication
Biometric authentication uses unique biological traits like fingerprints, facial features or iris patterns to verify a person’s identity. In crypto wallets, it offers a convenient and secure way to access digital assets, replacing the traditional password or seed phrase approach.
In a world of smartphones, this option offers the best user experience. However, some biometric data can be faked using advanced prosthetics. This can be an outlier when compared to risks with other wallet options.
These solutions demonstrate a shift toward user-centric security in the crypto space, making it easier for individuals to manage their digital wealth without compromising safety.
The cost of lost crypto: A stark reality
The importance of securing seed phrases is further emphasized by the staggering amount of crypto wealth lost due to negligence. According to a report by Chainalysis, an estimated $140 billion worth of Bitcoin alone is inaccessible due to lost private keys or seed phrases.
For example, James Howells from New Port, Wales, threw away his hard drive that held 7,500 Bitcoin (BTC) in 2013, and Stefan Thomas lost access to his wallet in San Francisco, holding 7,008 Bitcoin. A reliable wallet infrastructure can be as critical as its assets.
Therefore, wallet providers should consider providing a better and more secure user experience to ensure recovering wallets is possible. On the other hand, Crypto users should keep their wallet details safe to ensure they don’t lose access to their assets.
Written by Arunkumar Krishnakumar



… [Trackback]
[…] Read More on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Info to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More Info here to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Here you will find 95262 additional Information to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More Information here on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More here to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More on to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More on on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More on on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More here on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Information to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Here you can find 2794 more Information on that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Here you will find 87848 additional Information to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Read More Information here to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More Information here to that Topic: x.superex.com/academys/beginner/1927/ […]
… [Trackback]
[…] Find More on that Topic: x.superex.com/academys/beginner/1927/ […]